Suche
Beiträge, die mit ThreatIntel getaggt sind
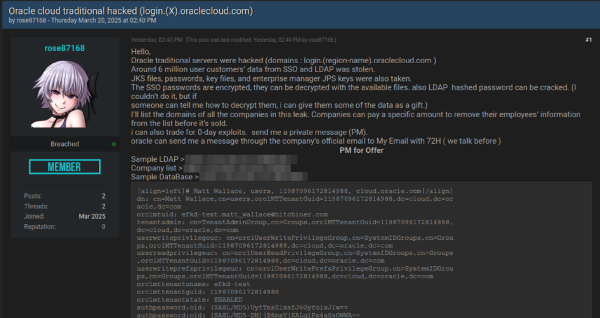
Somebody is claiming to have exfiltrated 6 million lines of data with Oracle Cloud’s SSO and LDAP that includes JKS files, encrypted SSO passwords, key files and enterprise manager JPS keys from servers on login.*.oraclecloud.com
The poster has no prior reputation, it is unclear if they're LARPing. Some of the sample data does align with prior infostealer logs, I'm told. https://breachforums.st/Thread-SELLING-Oracle-cloud-traditional-hacked-login-X-oraclecloud-com
#threatintel
The poster has no prior reputation, it is unclear if they're LARPing. Some of the sample data does align with prior infostealer logs, I'm told. https://breachforums.st/Thread-SELLING-Oracle-cloud-traditional-hacked-login-X-oraclecloud-com
#threatintel
Sekoia: https://blog.sekoia.io/clearfakes-new-widespread-variant-increased-web3-exploitation-for-malware-delivery/
A few days ago Brian Krebs wrote about ClickFix, and now Sekoia has written a technical deep dive of said malicious framework.
In the Sekoia report they analyze the evolution of ClearFake, a malicious JavaScript framework that compromises legitimate websites to deliver malware through drive-by downloads. Since its emergence in July 2023, ClearFake has evolved from displaying fake browser updates to using sophisticated social engineering tactics called 'ClickFix' that trick users into executing malicious PowerShell code. The latest variant (December 2024-February 2025) uses fake reCAPTCHA or Cloudflare Turnstile verifications alongside technical issues to deceive users. ClearFake leverages the Binance Smart Chain through a technique called 'EtherHiding' to store malicious code, making it impossible to remove. The framework has infected thousands of websites and is actively distributing Lumma Stealer and Vidar Stealer malware.
https://krebsonsecurity.com/2025/03/clickfix-how-to-infect-your-pc-in-three-easy-steps/
@briankrebs
@sekoia_io
#CyberSecurity #ClickFix #ThreatIntel
A few days ago Brian Krebs wrote about ClickFix, and now Sekoia has written a technical deep dive of said malicious framework.
In the Sekoia report they analyze the evolution of ClearFake, a malicious JavaScript framework that compromises legitimate websites to deliver malware through drive-by downloads. Since its emergence in July 2023, ClearFake has evolved from displaying fake browser updates to using sophisticated social engineering tactics called 'ClickFix' that trick users into executing malicious PowerShell code. The latest variant (December 2024-February 2025) uses fake reCAPTCHA or Cloudflare Turnstile verifications alongside technical issues to deceive users. ClearFake leverages the Binance Smart Chain through a technique called 'EtherHiding' to store malicious code, making it impossible to remove. The framework has infected thousands of websites and is actively distributing Lumma Stealer and Vidar Stealer malware.
https://krebsonsecurity.com/2025/03/clickfix-how-to-infect-your-pc-in-three-easy-steps/
@briankrebs
@sekoia_io
#CyberSecurity #ClickFix #ThreatIntel

clearfake-malware-compromised-websites
ClearFake spreads malware via compromised websites, using fake CAPTCHAs, JavaScript injections, and drive-by downloads.Sekoia TDR (SEKOIA.IO Blog)