Suche
Beiträge, die mit CyberSecurity getaggt sind
On Wednesday, the Barcelona-based human rights nonprofit Iridia announced that it had filed a complaint in a Catalan court earlier this week accusing NSO’s founders Omri Lavie and Shalev Hulio, as well as Yuval Somekh, an executive of two affiliate companies, of hacking crimes.
Iridia represents lawyer Andreu Van den Eynde, an attorney and university professor who specializes in cybersecurity. According to a 2022 investigation by Citizen Lab, a nonprofit that has been investigating government spyware for more than a decade, Van den Eynde was among the victims of a wide-ranging hacking campaign against at least 65 Catalans linked to the region’s attempts to become independent from Spain, which was carried out using NSO’s Pegasus software. Amnesty International independently confirmed Citizen Lab’s findings."
https://techcrunch.com/2024/11/13/lawyer-allegedly-hacked-with-spyware-names-nso-founders-in-lawsuit/
#CyberSecurity #NSOGroup #Pegasus #Spyware #Spain #Hacking

Lawyer allegedly hacked with spyware names NSO founders in lawsuit | TechCrunch
Spanish lawyer Andreu Van den Eynde is suing NSO Group and its founders Omri Lavie and Shalev Hulio, accusing them of illegal hacking.Lorenzo Franceschi-Bicchierai (TechCrunch)
#Palestine #hack #Israel #dataleak #CyberSecurity
https://cnews.link/israel-ministry-national-security-alleged-breach-1/
Pulse ID: 6734783599d63a48c4802abe
Pulse Link: https://otx.alienvault.com/pulse/6734783599d63a48c4802abe
Pulse Author: cryptocti
Created: 2024-11-13 09:58:13
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#CyberSecurity #InfoSec #Israel #Malware #OTX #OpenThreatExchange #bot #cryptocti

LevelBlue - Open Threat Exchange
Learn about the latest cyber threats. Research, collaborate, and share threat intelligence in real time. Protect yourself and the community against today's emerging threats.LevelBlue Open Threat Exchange
The data includes the employees’ name, work contact information, and what location they work at, and has more than 2.8 million lines of data, according to the post on Breach Forums. The post says the source of the data was MOVEit, which is suite of cloud data management tools.
“Amazon and AWS systems remain secure, and we have not experienced a security event. We were notified about [a] security event at one of our property management vendors that impacted several of its customers including Amazon. The only Amazon information involved was employee work contact information, for example work email addresses, desk phone numbers, and building locations,” an Amazon spokesperson told 404 Media in an email."
https://www.404media.co/amazon-confirms-breach-of-employee-data/
#Amazon #DataBreach #DataProtection #Privacy #Hacking #CyberSecurity

Amazon Confirms Breach of Employee Data
The breach includes the employees’ name, work contact information, and what location they work at.Joseph Cox (404 Media)
#northkorea #flashdrivesforfreedom #tech #linux #media #follow #boost #social #mastodon #peace #help #donate #cybersecurity #trending #freedom
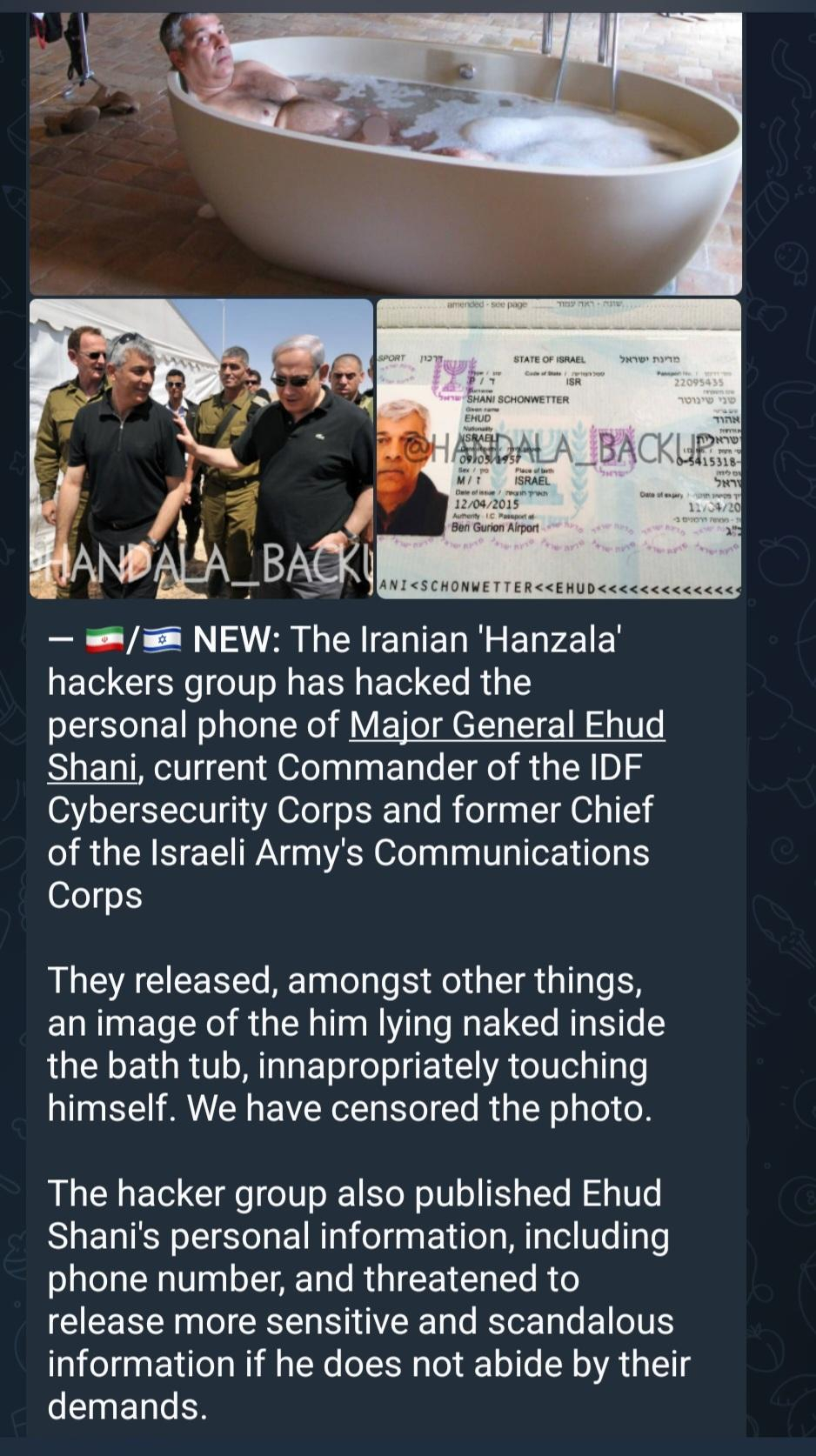
The #Iranian #Hanzala #hackers group has #hacked the personal phone of Major General Ehud Shani, current Commander of the #IDF #Cybersecurity Corps and former Chief of the #Israeli Army's Communications Corps
They released, amongst other things, an image of the him lying naked inside the bath tub, innapropriately touching himself. We have censored the photo.
The hacker group also published Ehud Shani's personal information, including phone number, and threatened to release more sensitive and scandalous information if he does not abide by their demands.
From the Middle_East_Spectator channel on Telegram.
#ThankYouHacktivists
#Terrorist
#FreePalestine
#IsraelIsATerroristState
#IsraelWarCrimes
#RacistIsrael
#IsraelRogueState
#ArmsEmbargoOnIsrael
#USAFundsGenocide
#BoycottIsrael
#BDSMovement
#BoycottIsraeliApartheid
#StopGenocide
#ApartheidIsrael
#SanctionIsrael
#ExposeIsraeliTerrorists
#ZionismIsACult
#FAFO
And that is quite a first hack, if it's legitimate.
#cybersecurity #databreach #israel
https://www.cyberdaily.au/security/11332-exclusive-anti-israel-hacker-claims-hack-on-ministry-of-national-security-posts-settler-ids-online

Exclusive: Anti-Israel hacker claims hack on Ministry of National Security, posts settler IDs online
Threat actor Radwan Cyber Pal has published firearms licence documents and photo IDs on Telegram belonging to 5,000 Israelis.David Hollingworth (Cyber Daily)
Thanks to a joint effort from the Tor community, InterSecLab, and the support of Andrew Morris and the team at GreyNoise, the origin of these spoofed packets was identified and shut down on November 7th, 2024.
We want to reassure everyone that this incident had no effect on Tor users. While the attack had a limited impact on the Tor network - taking a few relays offline temporarily - it caused unnecessary stress and inconvenience for many relay operators who had to address these complaints. Although this attack targeted our community, IP spoofing attacks can happen with any online service.
There's still work ahead: we need to support relay operators in getting their accounts reinstated and assist providers in unblocking IPs for Tor directory authorities."
https://blog.torproject.org/defending-tor-mitigating-IP-spoofing/
#Tor #CyberSecurity #Anonymity #Privacy #IPSpoofing
Defending the Tor network: Mitigating IP spoofing against Tor | Tor Project
Over the last few weeks, the Tor Project and relay operators received abuse complaints regarding alleged port scanning activity from their servers. Thanks to a collaborative effort, the source of the spoofed packets has been identified and shut down.blog.torproject.org
The FBI’s public notice filed this week is a rare admission from the federal government about the threat from fraudulent emergency data requests, a legal process designed to help police and federal authorities obtain information from companies to respond to immediate threats affecting someone’s life or property. The abuse of emergency data requests is not new, and has been widely reported in recent years. Now, the FBI warns that it saw an “uptick” around August in criminal posts online advertising access to or conducting fraudulent emergency data requests, and that it was going public for awareness.
“Cyber-criminals are likely gaining access to compromised US and foreign government email addresses and using them to conduct fraudulent emergency data requests to US based companies, exposing the personal information of customers to further use for criminal purposes,” reads the FBI’s advisory."
https://techcrunch.com/2024/11/08/fbi-says-hackers-are-sending-fraudulent-police-data-requests-to-tech-giants-to-steal-peoples-private-information/
#USA #CyberSecurity #FBI #Hacking #Privacy #DataProtection #DataBreaches

FBI says hackers are sending fraudulent police data requests to tech giants to steal people's private information | TechCrunch
The warning is a rare admission from the FBI about the threat from fake emergency data requests submitted by hackers with access to police email accounts.Zack Whittaker (TechCrunch)
A combination of good high-speed internet coverage, high digital literacy rates, large rural populations and fast-growing fintech industries had put the Nordic neighbours on a fast track to a future without cash.
Swish, a mobile payment system that six banks launched in 2012, is ubiquitous in Sweden, from market stalls to coffee shops and clothes stores. The Norwegian equivalent, Vipps, which merged with Danish MobilePay in 2022 to form Vipps MobilePay, is also very popular. Last month, it also launched in Sweden."
#Sweden #Norway #CashlessSociety #Russia #CyberSecurity #Money #Banking
https://www.theguardian.com/world/2024/oct/30/sweden-and-norway-rethink-cashless-society-plans-over-russia-security-fears
Based on interviews with malware developers, hackers who use the stolen credentials, and a review of manuals that tell new recruits how to spread the malware, 404 Media has mapped out this industry. Its end result is that a download of an innocent-looking piece of software by a single person can lead to a data breach at a multibillion-dollar company, putting Google and other tech giants in an ever-escalating cat-and-mouse game with the malware developers to keep people and companies safe."
https://www.wired.com/story/inside-the-massive-crime-industry-thats-hacking-billion-dollar-companies/
#CyberSecurity #CyberCrime #Hacking #Malware #InfoStealers #DataBreaches
The news comes after months of high profile data breaches, including AT&T, Ticketmaster, and LendingTree. In all, the hacker, who uses the nicknames Judische and Waifu, is linked to more than 165 Snowflake instance breaches. The arrest also comes after 404 Media reported that the walls were closing in on the hacker, with cybersecurity researchers gathering valuable information on the suspect and coordinating with international law enforcement.
Messages sent by 404 Media to Judische over the last week have gone undelivered, with 404 Media last speaking to them on October 27. In mid-October, Judsiche told 404 Media they were worried that they would be arrested soon. “I've destroyed a lot of evidence and well poisoned the stuff I can't destroy so when/if it does happen it's just conspiracy which I can bond out and beat,” they claimed."
https://www.404media.co/suspected-snowflake-hacker-arrested-in-canada/
#CyberSecurity #DataBreaches #Hacking #CyberCrime #Snowflake #Canada
Suspected Snowflake Hacker Arrested in Canada
For more than a week Judische, the hacker linked to the AT&T, Ticketmaster and other breaches, has not been responding to messages. That's because he's been arrested.Joseph Cox (404 Media)
https://sites.google.com/view/dan-tech-blog
@altbot
#LLM #tech #blog #ai #cybersecurity #phishing #perplexity #perplexityai
https://www.bleepingcomputer.com/news/security/hackers-exploit-wordpress-plugin-flaw-to-infect-3-300-sites-with-malware/
#technology #tech #web #blogging #security #cybersecurity #hacked #hackers #wordpress
https://www.wired.com/story/russia-hackers-microsoft-source-code/
#technology #tech #hacked #hackers #microsoft #security #cybersecurity #datasecurity

Russian Hackers Stole Microsoft Source Code—and the Attack Isn’t Over
Plus: An ex-Google engineer gets arrested for allegedly stealing trade secrets, hackers breach the top US cybersecurity agency, and X’s new feature exposes sensitive user data.Dhruv Mehrotra (WIRED)
1 million data points exclusively about Ashkenazi Jews have been advertised for sale on a cybercrime forum. There's also information about hundreds of thousands of users of Chinese descent.
It appears to be a credential stuffing attack—where previously leaked logins and passwords from other sites are tried on 23andMe—with the attackers then scraping data from profiles
@lhn's story has all the details we know so far:
https://www.wired.com/story/23andme-credential-stuffing-data-stolen/ #cybersecurity #news #tech #23andme #infosec

23andMe User Data Stolen in Targeted Attack on Ashkenazi Jews
At least a million data points from 23andMe accounts appear to have been exposed on BreachForums. While the scale of the campaign is unknown, 23andMe says it's working to verify the data.Lily Hay Newman (WIRED)