Suche
Beiträge, die mit infosec getaggt sind
Folks, I just want to remind you all that “vibe accounting” is better known as “fraud” or “embezzlement”. Please plan accordingly.
#InfoSec
#InformationSecurity
The author misses some utterly crucial details however.
1) When your encrypted device is on, it is in an *unlocked* state. Only by powering off such a device is it in an encrypted state. Further, MicroSD cards are often unencrypted. Check before you fly, and power off before the border.
2) (next post)
https://www.theguardian.com/technology/2025/mar/26/phone-search-privacy-us-border-immigration
#privacy #infosec
#infosec #opsec
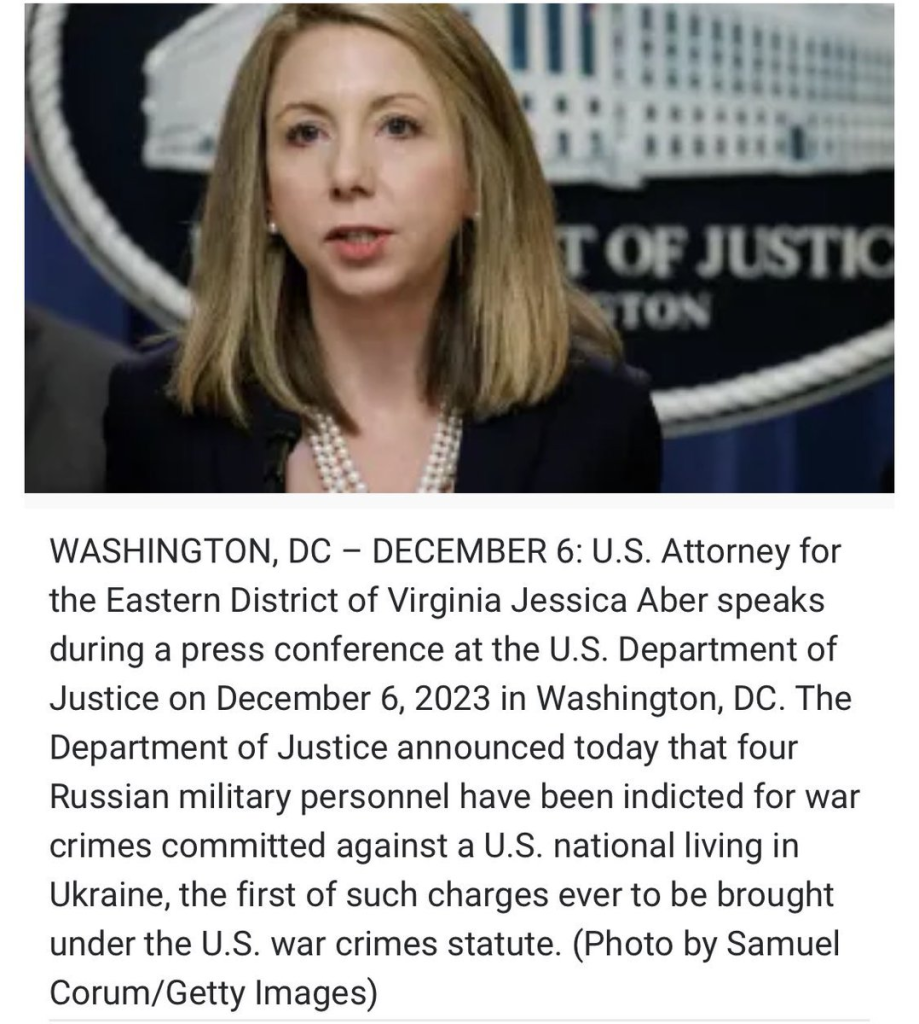
September 2024: US District Attorney Jessica Aber indicts Russian cryptocurrency money launderer / cybercriminal #SergeyIvanov
November 2024: US District Attorney Jessica Aber accuses Virginia based companies of running "three different schemes to illegally transship sensitive American technology to Russia," including sending equipment to a Russian telecommunications company linked to the #Kremlin and Russia's notorious #FSB security agency.
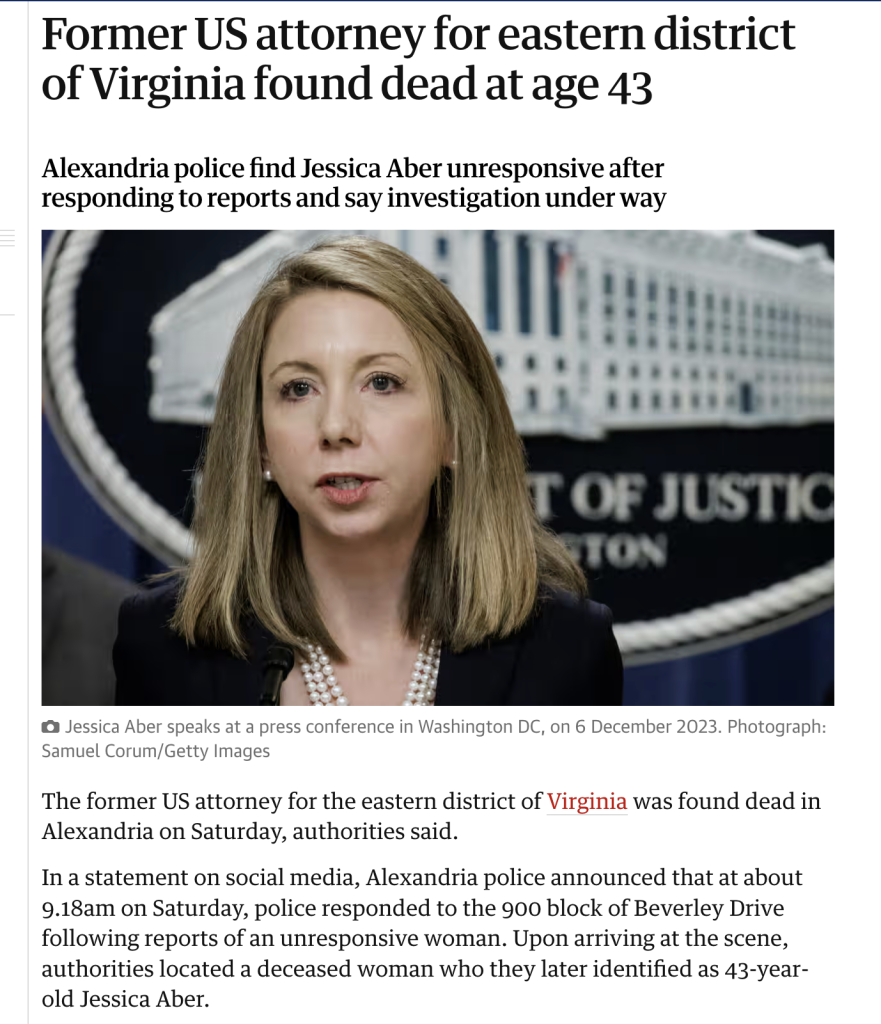
March 2025: Former US District Attorney Jessica Aber found dead at age 43
More: https://www.newsweek.com/jessica-aber-death-2049234
#Putin #VladimirPutin #JessicaAber #Russia #UkraineWar #Virginia #Vapol #crime #alexandria #TrueCrime #uspol #eupol #eu #AsifRahman #infosec #ransomware #cybersecurity
Ex-US Attorney Jessica Aber Investigated Russia, CIA Leaker Before Death
Aber resigned as U.S. Attorney for the Eastern District of Virginia after President Donald Trump returned to the Oval Office.Ellie Cook (Newsweek)
Pig butchering isn't going to stop if you ignore it like it does with the script kiddies and discord ethugs.
#infosec
The report investigates Paragon Solutions, an Israeli spyware company founded in 2019 that sells a product called Graphite. Through infrastructure analysis, the researchers identified potential Paragon deployments in several countries. They also found evidence linking Paragon to the Canadian Ontario Provincial Police. Working with WhatsApp, they discovered and mitigated a Paragon zero-click exploit targeting civil society members. Forensic analysis of Android devices in Italy confirmed Paragon infections. The report also examines a potentially related iPhone spyware case. It highlights Paragon's targeting of individuals involved in migrant rescue operations in the Mediterranean, raising questions about the company's claims of only selling to customers respecting human rights. The findings challenge Paragon's marketing approach and demonstrate the ongoing risks of mercenary spyware abuse, even in democracies.
Pulse ID: 67db3e42358011c1a3975302
Pulse Link: https://otx.alienvault.com/pulse/67db3e42358011c1a3975302
Pulse Author: AlienVault
Created: 2025-03-19 21:59:30
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#Android #Canadian #CyberSecurity #InfoSec #Israel #Italy #OTX #OpenThreatExchange #RAT #RCE #SpyWare #WhatsApp #bot #AlienVault
New #Blog post going through a #TryHackMe challenge. This time detecting two different attack types with snort!
https://ligniform.blog/posts/snort-live-attacks/
💜 🌱
#InfoSec #Learning #CyberSecurity #BlueTeam #Hacking
CTF Writeup: Snort Challenge - Live Attacks
Quick writeup of a Snort challenge on TryHackMe.Ligniform (Ligniform Blog)
https://pluralistic.net/2025/03/18/asbestos-in-the-walls/
#USpol #musk #elon #ai #DataEthics #infosec #safety
🔗 https://biziday.ro/?p=313782
#Știri #InfoSec #SecuritateInformatică
Google realizează cea mai mare achiziție din istoria sa. A încheiat un acord pentru preluarea start-up-ului israelian de securitate cibernetică Wiz, în schimbul a 32 de miliarde de dolari. - Biziday
Google și compania-mamă Alphabet urmăresc să sporească securitatea serviciilor lor cloud, firma israeliană fiind specializată în acest domeniu și oferindAuras Rosu (Biziday)
Has anyone come across any businesses that have made the leap recently? Feel free to DM or message on Signal, mattburgess.20
#infosec #privacy #cloud #security
Author: Ben Tasker
https://www.bentasker.co.uk/posts/blog/security/seducing-a-romance-scammer.html?utm_source=rss
#infosec #osint #scams #security
My Scammer Girlfriend: Baiting A Romance Fraudster
Romance fraud has been growing as an issue for years. It's not uncommon to see news stories with bewildered victims explaining just how deeply they'd been sucked in. After receiving a number of openerwww.bentasker.co.uk
"France is proposing a law to require encrypted messaging applications, including Signal and WhatsApp, and encrypted email services such as Proton Mail to provide law enforcement with decrypted data on request.
The law, which aims to provide French law enforcement with stronger powers to combat drug trafficking, has raised concerns among tech companies and civil society groups that it will lead to the creation of “backdoors” in encrypted services that will be exploited by cyber criminals and hostile nation-states."
The law also permits the use of spyware such as NSO Group’s Pegasus or Paragon to allow police to remotely activate microphones and cameras of mobile phones and computers, according to an analysis by the civil society group, La Quadrature Du Net.
It also extends the scope of algorithms, known as “black boxes”, which collect data on communications over the internet with the intention of identifying people suspected of criminal activity to authorise the collection of data for “combatting crime and organised crime”."
https://www.computerweekly.com/news/366619707/France-pushes-for-law-enforcement-access-to-Signal-WhatsApp-and-encrypted-email#:~:text=Law%20permits%20police%20use%20of%20spyware&text=Police%20will%20also%20have%20powers,the%20intervention%20of%20a%20judge
#Privacy #InfoSec #Data #Security #CivilRights #Encryption #BackDoor #Journalism #MediaLiteracy

France pushes for law enforcement access to Signal, WhatsApp and encrypted email
Proposals to be discussed in the French Parliament will require tech companies to hand over decrypted messages and email or face huge finesBill Goodwin (ComputerWeekly.com)
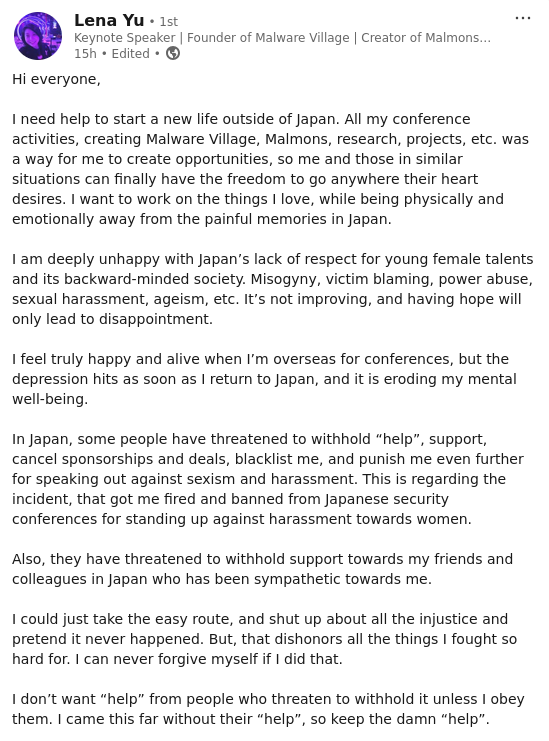
sadly, it wasn't valued in Japanese #InfoSec society, esp. when calling out sexual harassment & because of that Lena was ostracised. she deserves better than this
sharing her msg in hope someone in #Fediverse would be interested in hiring her outside of Japan. reposts appreciated
https://lambdamamba.com/index.html
#FediHired #GetFediHired #Malware #CyberSecurity #Job #JobSearch #Hiring #Security
https://support.delta.chat/t/webxdc-threat-model/3018
#puzzle #puzzles #competitive #game #multiplayer

WebXDC threat model?
Hi, I’ve just came across this WebXDC idea through its implementation in Monocles Chat (which does not appear to be working at the moment, but that’s another story).Delta.Chat
https://www.pysec.online/blog
#blog #technology #security #onlinechildsafety #infosec
Journey to #FOSS (updated Mar 3)
🧵1/2
--Messages ➡️ Signal-FOSS
--Chrome ➡️ Fennec & Bitwarden
--Gmail ➡️ Thunderbird & TBA*
--Keep ➡️ Quillpad
--Drive/Dropbox ➡️ TBA/ProtonDrive**
--Photos/editor ➡️ Ente/Fossify Gallery
--Maps ➡️ Magic Earth**
--Contacts & calc ➡️ Fossify & yetCalc
--Camera ➡️ TBA*
--Translate ➡️ Translate You
--YT ➡️ NewPipe**
--Swiftkey ➡️ HeliBoard w/ Whisper
--Authy ➡️ Aegis
--GReaderPro ➡️ Capy Reader
--G Song ID ➡️ Audile
#Android #InfoSec
Recall allows Microsoft’s Windows 11 Copilot+ devices to screenshot every action a person takes on their PC.
What can you do? Switching to Linux is the clear answer, but some don't know what distro to try.
DistroSea.com is a website that lets you run and test 60+ Linux distributions straight from your web browser.
Have fun!
Source: https://distrosea.com/
#Linux #Computer #Windows #DOS #OPSEC #InfoSec #Privacy #Surveillance
Damn it! I did it again!
Apple currently only able to detect Pegasus spyware in half of infected iPhones
https://9to5mac.com/2025/02/20/apple-currently-only-able-to-detect-pegasus-spyware-in-half-of-infected-iphones/
#Apple #Pegasus #NSOGroup #Israel #iPhone #InfoSec #Tech
Apple currently only able to detect Pegasus spyware in half of infected iPhones
NSO’s Pegasus spyware is one of the most frightening privacy threats an iPhone owner can face. Without you taking any...Ben Lovejoy (9to5Mac)
Thank you.
#infosec #cybersecurity
Perhaps they could ask about the use of #GammaGroup's #FinFisher #FinSpy #Finsky software used for targeting users at around a 250k run rate since 2015 & how that's a key user acquisition strategy software component wise but is never mentioned for some reason in the #press as a key component of ' non-organic growth ' but basic racketeering ( #RICO ) ¯\_(ツ)_/¯
#infosec #KiwiFarmsClone site #Meta #FacebookGroups #StalkerForums #StateSponsoredMalware use cases
https://www.jwz.org/xscreensaver/google.html
#privacy #security #infosec #Android #screensaver
#law #privacy #Trump #InfoSec #PersonalFinance
#law #privacy #Trump #InfoSec #PersonalFinance
#law #privacy #Trump #InfoSec #PersonalFinance
“At this rate, they will break it. And they will break it fast, & there will be an interruption of #benefits,” said Martin O’Malley, the #SocialSecurity commissioner under the Biden admin & a fmr Maryland governor.
#law #PersonalFinance #privacy #ElonMusk #InfoSec
#law #privacy #ElonMusk #InfoSec
Michelle King, who spent several decades at the agency before being named its acting commissioner last month, left her position Sunday after the disagreement, the people said.
#law #privacy #Trump #InfoSec
Yet another top career staffer is leaving the administration amid a disagreement over a request by #ElonMusk’s team for sensitive government #information.
#law #privacy #Trump #InfoSec
https://www.washingtonpost.com/politics/2025/02/17/doge-social-security-musk/
 for reach.
for reach.#politics #USPol #resist #infosec
Does this seem like improving government efficiency?
#politics #USPol #DOGE #USDS #VA #infosec
2/2
#CyberSecurity #cyberattacks #logins #Networking #infosec
https://cnews.link/over-2-million-ips-attacking-edge-network-devices-1/
We need people to test (also trash^^) a prototype (website + back-end) we're working on & to open/submit issues.
A central index of archives, with metadata about who archived what, when, to be disseminated widely alongside torrent files.
Please contact me on Matrix or Signal:
Matrix: @schoeneh:matrix.org
Signal: upon request via DM
Please boost and share! 🚀🔁
#SafeguardingResearch @SafeguardingResearch
Gerade mal die Kassensysteme funktionieren wohl.
Wer mag das wohl sein …
Unabhängig davon:
Habt ein Incident Management. Habt einen Manager dafür. Spielt Szenarien durch (Testen, Testen, Testen). Macht Backups, die offline gesichert werden. Monitored eure Systeme.
#InfoSec #Ransomeware
#infosec #OperationRubicon
https://www.pcmag.com/how-to/what-are-zero-day-exploits-and-attacks
https://signal.org/
#Resistance #Infosec

Signal Messenger: Speak Freely
Say "hello" to a different messaging experience. An unexpected focus on privacy, combined with all of the features you expect.Signal Messenger
Mobile communications best practices guide from the Federal Cybersecurity and Infrastructure Security Agency. (2/x)
#Resistance #Infosec
https://www.cisa.gov/sites/default/files/2024-12/guidance-mobile-communications-best-practices.pdf