Suche
Beiträge, die mit tech getaggt sind
https://grafa.com/asset/archer-exploration-ltd-5699-axe.asx?utm_source=asxmktsensitive&utm_medium=mastodon&utm_campaign=axe.asx
The “world’s worst digital dash”, a Nintendo Game Boy as a digital speedometer. Interfacing the handheld with the vehicle’s CAN bus system, this project has something to offer.
🖇️Check my Image Description’s🖇️
https://github.com/JohnSutley/Worlds-Worst-Digital-Dash
#diy #retro #gameboy #speedometer #car #canbus #system #it #engineer #artist #media #maker #tech #art #progamming #news
GitHub - JohnSutley/Worlds-Worst-Digital-Dash
Contribute to JohnSutley/Worlds-Worst-Digital-Dash development by creating an account on GitHub.GitHub
jetzt noch bei X bleibt ist nicht mehr zu retten.
#leavex #musk #elonmusk #datenschutz #exploration #datamining #X #tech #socialmedia
https://blog.codeminer42.com/codeminer42-dev-weekly-54/
#blog #codeminer42 #tech #news #weekly
Codeminer42 Dev Weekly #54 - The Miners
The last and newest Dev Weekly of March is out! Check it out and share with your friends.Gabriel Quaresma (The Miners - Codeminer42's Engineering Blog)
#PeerTube: the Fediverse’s decentralized video platform (part 2: creator edition)
https://blog.elenarossini.com/peertube-the-fediverses-decentralized-video-platform-part-2-creator-edition/
My PeerTube account: @elena
mentioning @Framasoft @peertube @paige @srosset @MakerTube
#ActivityPub #tech #Fediverse #activism #BigTech #SocialMedia #FOSS #blog

PeerTube: the Fediverse’s decentralized video platform (part 2: creator edition)
What is it like to use PeerTube as a video creator? Spoiler alert: it's amazing!Elena Rossini
Despite the hype from Silicon Valley, my belief is the generative #AI and LLM bubble is nearing its bursting point.
Like with the dot com crash, Wall Street and Investors are getting impatient and want to see profitability.
Most AI startups aren't even close. And mass adoption of AI tools still hasn't become ubiquitous among the general public - and probably never will.
Most "features" are over-hyped and AIs can still "hallucinate" (lie) when providing information - a very big issue the tech industry is trying to downplay.
Startups are going to either shut down or be acquired by the bigger players.
Also, like the dot com bust, only the biggest, most deep-pocketed players are going to remain standing after the shakeout.
I think the AI landscape is going to start imploding as early as the end of this year.
AI will still play a role, but not be as revolutionary as the tech industry wants us to believe.
The creators and top execs of Meta do not allow their own children on it.
Think about that.
#carelesspeople #facebook #tech
https://grafa.com/news/technology-kyndryl-holdings-shares-plunge-after-short-seller-report-alleges-financial-manipulation-408027?utm_source=us_news_en&utm_medium=mastodon&utm_campaign=408027
https://gomoot.com/gemini-2-5-pro-il-modello-ia-di-google-che-pensa/
#blog #dataset #gemini #google #grok #llm #lmarena #modelloai #multimodale #news #openai #pensare #picks #tech #tecnologia #token
Gemini 2.5 Pro: il modello IA di Google che “pensa”
Gemini 2.5 Pro, il "modello più intelligente" di Google focalizzato sul ragionamento. Prestazioni top, multimodalità, contesto enorme e accesso via AI Studiocristina (Gomoot : tecnologia e lifestyle)
https://gomoot.com/gpt-4o-riceve-la-generazione-immagini-integrata-in-chatgpt
#ai #blog #gpt4o #ia #news #openai #picks #tech #tecnologia

GPT-4o riceve la generazione immagini integrata in ChatGPT
GPT-4o cambia il generatore di immagini DALL-E con un generatore di immagini nativo in grado di creare immagini dettagliate e coerenti con interazioni in chat.Graziano (Gomoot : tecnologia e lifestyle)
https://grafa.com/news/auto-and-cars-mobileye-shares-jump-as-volkswagen-deepens-collaboration-on-autonomous-driving-tech-405854?utm_source=us_news_en&utm_medium=mastodon&utm_campaign=405854
According to LayerX Labs, who have been tracking this campaign for more than a year, the phishing attack attempts to trick Mac users into thinking that their computers have been “locked” via a fake security warning that pops up while users are browsing the web.
https://layerxsecurity.com/blog/layerx-identifies-new-phishing-campaign-targeted-at-mac-users/
#apple #macos #it #security #privacy #engineer #media #tech #news
LayerX Labs Identifies New Phishing Campaign Targeted at Mac Users - LayerX
A new phishing attack campaign, targeting Mac users and identified by LayerX Labs, shows the trials and tribulations of combating online phishing, and how attacks morph and shift in response to adaptations by security tools.Or Eshed (LayerX)
https://grafa.com/news/health-kezar-life-sciences-reports-positive-results-for-zetomipzomib-and-2024-financials-405779?utm_source=us_news_en&utm_medium=mastodon&utm_campaign=405779
https://www.inc.com/ben-sherry/employees-are-sabotaging-their-companys-ai-strategy-according-to-a-new-survey/91162740
The survey found that 41 percent of Millennial and Gen-Z employees said they’d done some form of sabotage.
#AI #sabotage #tech #press
https://www.theguardian.com/games/2025/mar/24/video-games-cant-escape-their-role-in-the-radicalisation-of-young-men
Those of us who spend our lives gaming can no longer deny knowledge that our online communities are awash with disturbing hate speech and violent rhetoric. There is a lot of attention on young men and toxic masculinity at the moment. It’s about time.
KEWL🌀NEWS
#MEN #TOXICITY #ADOLESCENTS #BOYS #NETFLIX #TECH #PRESS
https://grafa.com/news/technology-tesla-to-launch-smart-driving-feature-in-china-following-software-approval-404666?utm_source=us_news_en&utm_medium=mastodon&utm_campaign=404666

Silicosis is ruining the lungs of construction workers. An AI-powered breath test can detect it in minutes
Silicosis is preventable but difficult to detect early. A promising new breath test could change this.The Conversation
 📄 Minimal Linux OS runs in a 6MB PDF Document in Chrome.
📄 Minimal Linux OS runs in a 6MB PDF Document in Chrome.A version of the Linux operating system can now be run inside a PDF opened by a Chromium-based browser. The developer [Ading2210] explains that Linux need a modified version of the TinyEMU RISC-V emulator.
https://github.com/ading2210/linuxpdf
#linux #pdf #chromium #based #browser #it #engineer #media #programming #art #tech #developer #artist #news
GitHub - ading2210/linuxpdf: Linux running inside a PDF file via a RISC-V emulator
Linux running inside a PDF file via a RISC-V emulator - ading2210/linuxpdfGitHub
#Python #Programming #Coding #IT #Tech #Software #computer #Statistics #DataAnalysis #MachineLearning #DataScience #Jokes #Memes #Funny #NeuralNetworks #AI #DevOps
💻
Python Knowledge Base
https://python-code.pro/
Where curiosity meets code – explore our Python knowledge hub today!
Become a Python expert with our comprehensive knowledge base, covering everything from the basics to advanced topics, take your coding to the next level.Andrey BRATUS (python-code.pro)
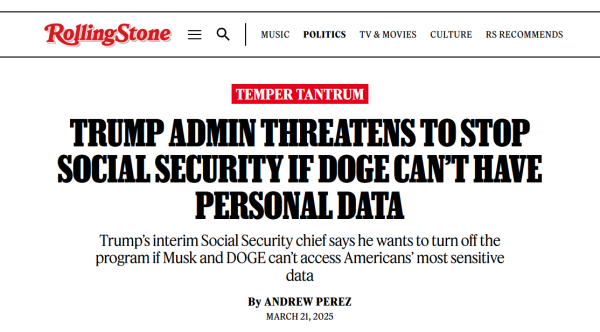
Trump’s interim Social Security chief says he wants to turn off the program if #Musk & #DOGE can’t access #Americans’ most sensitive #data
https://www.rollingstone.com/politics/politics-news/trump-musk-stop-social-security-doge-data-1235300785/
"Dudek’s threat to block #SSA employees from using the agency’s #IT systems — a move that could halt #SocialSecurity payments — came in response to a judge’s temporary restraining order"
#ElonMusk #Coup #Corruption #Trump #GOP #USPol #Tech #News #US #USA
Trump Admin Threatens to Stop Social Security If DOGE Can’t Have Data
Lee Dudek, Trump’s interim Social Security chief, says he wants to turn off the program if Musk and DOGE can’t access Americans’ most sensitive data.Andrew Perez (Rolling Stone)
Using Israeli tech directly contributes to Israel's war on Palestinians.
#Israel #Palestine #Gaza #Tech #BDS
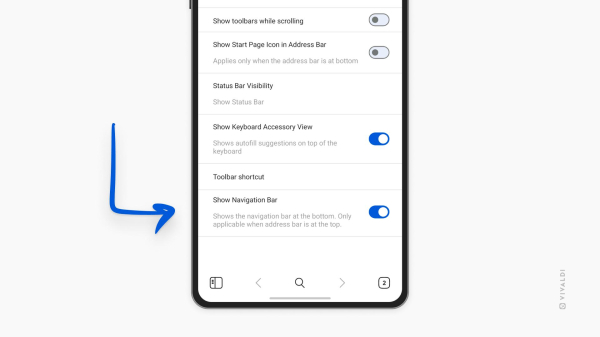
When you move the Tab and Address Bars to the bottom, the Navigation Bar disappears and you have more screen space. If you prefer to keep the Tab and Address Bars on top there’s still a way to hide the Navigation Bar.
To hide it:
Settings > Appearance & Theme > Disable “Show Navigation Bar”.
When hidden, the Tab Switcher button is moved to the Address Bar and other features are available from the main Vivaldi menu.
#Android #Browser #Tech #Apps
Nicola Wrachien with Silicon Labs created this fun handheld, porting Quake using the Arduino Nano Matter. For easy playing a custom controller shaped board was designed with joysticks and a screen.
https://next-hack.com/index.php/2024/09/22/quake-port-to-sparkfun-and-arduino-nano-matter-boards-using-only-276-kb-ram/
#quake #arduino #nano #diy #handheld #port #retro #gaming #art #maker #engineer #artist #media #programming #tech #news
I'm new around these parts.
I'm a mid 20s woman from Denmark 🇩🇰
Mostly lurking but will be posting my random thoughts, #tech, #fashion, whenever I do any #travel, and whenever I do something around the web.
I'm also the (currently only blind) software engineer @bemyeyes
Looking forward to chat with you all around these parts
https://www.axios.com/2025/03/21/yahoo-techcrunch-regent
#business #technology #journalism #TechNews #SiliconValley
Keep up to date with social media trends and news with Lifewire, https://flipboard.com/@lifewiretech/social-media-beat-p1a7jmh1z
Gamers: IGN has you covered, with news and game reviews, https://flipboard.com/@ign/gaming-news-and-reviews-s4u82mu1z
AI news overwhelming you? Gizmodo can break it down, https://flipboard.com/@gizmodo/artificial-intelligence-7bv07f1uz
Engadget breaks down trends, news and deals on the newest gear, https://flipboard.com/@engadget/gear-nv6v86arz
#Tech #Technology #FollowFriday #Fediverse #Media #News #Journalism

Gear | @Engadget | Flipboard
Explore Engadget's magazine "Gear", followed by 643660 people on Flipboard. See more stories about ChatGPT, Logo Design, Consumer Tech.Flipboard
Why do you think Tards like #Musk and #Trump are DISRUPTING MARKETS? Because it makes them aqnd their scumbag bffs rich as ordinary joe investors lose everything and jump from windows
Got that @gilduran? I WATCHED as scum like this forced all the creatives out in the 80s when you were still a child.
🍎 Format your Notes with Markdown & rich text
🍎 Fine-tune your Address Bar suggestions
🍎 Access past translations with Translation History
🍎 Set custom zoom levels for individual sites
🍎 7 new UI languages added
…and more. Go try it now, and check out our blog post for all the details: https://vivaldi.com/blog/vivaldi-on-ios-7-2/
#iOS #iPadOS #iPhone #iPad #Apps #Tech #Vivaldi #Browser #Notes
Vivaldi 7.2 for iOS: More Control, More Customization, More You. | Vivaldi Browser
We’re back with another update for Vivaldi on iOS, bringing more ways to fine-tune your browsing experience and stay in control. With Vivaldi 7.2…Jon von Tetzchner (Vivaldi Technologies)
Text messages sent between iOS & Android devices will soon benefit from end-to-end encryption, after the GSM Association published new specifications for the RCS protocol that include support for cross-platform E2EE.
https://www.gsma.com/solutions-and-impact/technologies/networks/gsma_resources/gsma-rcs-universal-profile-3-0-specifications/
#ios #android #rcs #protocol #it #security #privacy #engineer #media #tech #news

![Months of work have gone into decoding the Game Boy’s data bus and creating a schematic for the interface board. Tricking the Game Boy into thinking it was loading a game, while actually displaying incoming speed data. The screen’s low resolution and slow refresh rate rendered it barely readable in a moving vehicle. But [John]’s goal wasn’t practicality — it was just proving it could be done. Months of work have gone into decoding the Game Boy’s data bus and creating a schematic for the interface board. Tricking the Game Boy into thinking it was loading a game, while actually displaying incoming speed data. The screen’s low resolution and slow refresh rate rendered it barely readable in a moving vehicle. But [John]’s goal wasn’t practicality — it was just proving it could be done.](https://friendica-leipzig.de/photo/preview/1024/846999)
![[ImageSource: John Sutley]
Showing real-time vehicle speed on the Game Boy sounds like it should be relatively easy, but the iconic game system wasn’t exactly built for such a task. Its 2 MHz CPU and 160×144 pixel dot-matrix screen were every kid’s dream in 1989, but using it as a car dashboard is pushing it. To bridge that gap, [John] designed two custom circuit boards.
One interfaces with the Game Boy, intercepting its memory requests and feeding it data from a microcontroller. The other processes the CAN bus signals, translating speed information into a form the Game Boy can display. [John] used inexpensive tools and software to read the CAN bus data, and used GBDK-2020 to write the software in C. [ImageSource: John Sutley]
Showing real-time vehicle speed on the Game Boy sounds like it should be relatively easy, but the iconic game system wasn’t exactly built for such a task. Its 2 MHz CPU and 160×144 pixel dot-matrix screen were every kid’s dream in 1989, but using it as a car dashboard is pushing it. To bridge that gap, [John] designed two custom circuit boards.
One interfaces with the Game Boy, intercepting its memory requests and feeding it data from a microcontroller. The other processes the CAN bus signals, translating speed information into a form the Game Boy can display. [John] used inexpensive tools and software to read the CAN bus data, and used GBDK-2020 to write the software in C.](https://friendica-leipzig.de/photo/preview/600/847001)

![[ImageSource: LayerX Labs]
The webpage then appears to be frozen which, like most phishing attempts, adds a sense of urgency and fear that something is wrong with your computer. The window that appears displays a warning that the computer has been subjected to a trojan virus and asks the user to enter in their Mac username and password.
The warning message [captured in a screenshot by LayerX Labs], contains some glaring errors that show it’s not legitimate: It does not conform to any of Apple’s styling either in color or general appearance and misspells macOS as “MacOS.”
It also provides a phone number to contact “support,” however, when [Macworld] called this number they only got a message playback that said the recipient was not available and to call back between 8am and 5pm – even though they were calling during that time frame. The number is obviously fake and will likely never be answered.
<https://www.macworld.com/article/2642938/new-mac-phishing-attack-causes-fake-freezes-to-nab-your-apple-id-password.html> [ImageSource: LayerX Labs]
The webpage then appears to be frozen which, like most phishing attempts, adds a sense of urgency and fear that something is wrong with your computer. The window that appears displays a warning that the computer has been subjected to a trojan virus and asks the user to enter in their Mac username and password.
The warning message [captured in a screenshot by LayerX Labs], contains some glaring errors that show it’s not legitimate: It does not conform to any of Apple’s styling either in color or general appearance and misspells macOS as “MacOS.”
It also provides a phone number to contact “support,” however, when [Macworld] called this number they only got a message playback that said the recipient was not available and to call back between 8am and 5pm – even though they were calling during that time frame. The number is obviously fake and will likely never be answered.
<https://www.macworld.com/article/2642938/new-mac-phishing-attack-causes-fake-freezes-to-nab-your-apple-id-password.html>](https://friendica-leipzig.de/photo/preview/600/821761)


![If you wish to try out the LinuxPDF, it requires a Chromium-based browser to work correctly (I checked, but it didn't work in Firefox on PC).
On the topic of speed and efficiency, [Ading2210] humbly admits that performance might be the largest problem with LinuxPDF. "The Linux kernel takes about 30-60 seconds to boot up within the PDF, which [is] over 100x slower than normal," notes the developer. With Chrome's current PDF engine having its Just-in-Time (JIT) compiler disabled, [Ading2210] sees no way of speeding up the code, for now. If you wish to try out the LinuxPDF, it requires a Chromium-based browser to work correctly (I checked, but it didn't work in Firefox on PC).
On the topic of speed and efficiency, [Ading2210] humbly admits that performance might be the largest problem with LinuxPDF. "The Linux kernel takes about 30-60 seconds to boot up within the PDF, which [is] over 100x slower than normal," notes the developer. With Chrome's current PDF engine having its Just-in-Time (JIT) compiler disabled, [Ading2210] sees no way of speeding up the code, for now.](https://friendica-leipzig.de/photo/preview/1024/810578)
![[ImageSource: Ading2210]
The TinyEMU RISC-V emulator runs in the PDF thanks to a technique where its code is compiled "using an old version of Emscripten that targets asm.js instead of WebAssembly." This is embedded and loads in the PDF, subsequently auto-running a minimal Linux kernel targeting that architecture.
In this implementation, once you agree to 'Start Emulator' in your browser, you will see the LinuxPDF UI load, and a welcome message in the Linux viewport, as you wait for the OS to boot. [ImageSource: Ading2210]
The TinyEMU RISC-V emulator runs in the PDF thanks to a technique where its code is compiled "using an old version of Emscripten that targets asm.js instead of WebAssembly." This is embedded and loads in the PDF, subsequently auto-running a minimal Linux kernel targeting that architecture.
In this implementation, once you agree to 'Start Emulator' in your browser, you will see the LinuxPDF UI load, and a welcome message in the Linux viewport, as you wait for the OS to boot.](https://friendica-leipzig.de/photo/preview/600/810580)
![[ImageSource: Ading2210]
Below the Linux viewport in the PDF is a soft keyboard created by an array of PDF buttons. However, it is likely quicker for everyone with a decent physical keyboard to input commands into the 'type here for keyboard inputs' field to the lower right of the keyboard UI area. [ImageSource: Ading2210]
Below the Linux viewport in the PDF is a soft keyboard created by an array of PDF buttons. However, it is likely quicker for everyone with a decent physical keyboard to input commands into the 'type here for keyboard inputs' field to the lower right of the keyboard UI area.](https://friendica-leipzig.de/photo/preview/600/810582)



![[ImageSource: Nicola Wrachien]
For a much tougher challenge, a group from Silicon Labs decided to port DOOM‘s successor, Quake, to the Arduino Nano Matter Board platform instead even though this platform has some pretty significant limitations for a game as advanced as Quake.
<https://community.silabs.com/s/share/a5UVm000000Vi1ZMAS/quake-ported-to-arduino-nano-matter-and-sparkfun-thing-plus-matter-boards?language=en_US>
To begin work on the memory problem, the group began with a port of Quake originally designed for Windows, allowing them to use a modern Windows machine to whittle down the memory usage before moving over to hardware. They do have a flash memory module available as well, but there’s a speed penalty with this type of memory. To improve speed they did what any true gamer would do with their system: overclock the processor. This got them to around 10 frames per second, which is playable, but not particularly enjoyable.
The further optimizations to improve the FPS required a much deeper dive which included generating lookup tables instead of relying on computation, optimizing some of the original C programming, coding some functions in assembly and only refreshing certain sections of the screen when needed. [ImageSource: Nicola Wrachien]
For a much tougher challenge, a group from Silicon Labs decided to port DOOM‘s successor, Quake, to the Arduino Nano Matter Board platform instead even though this platform has some pretty significant limitations for a game as advanced as Quake.
<https://community.silabs.com/s/share/a5UVm000000Vi1ZMAS/quake-ported-to-arduino-nano-matter-and-sparkfun-thing-plus-matter-boards?language=en_US>
To begin work on the memory problem, the group began with a port of Quake originally designed for Windows, allowing them to use a modern Windows machine to whittle down the memory usage before moving over to hardware. They do have a flash memory module available as well, but there’s a speed penalty with this type of memory. To improve speed they did what any true gamer would do with their system: overclock the processor. This got them to around 10 frames per second, which is playable, but not particularly enjoyable.
The further optimizations to improve the FPS required a much deeper dive which included generating lookup tables instead of relying on computation, optimizing some of the original C programming, coding some functions in assembly and only refreshing certain sections of the screen when needed.](https://friendica-leipzig.de/photo/preview/600/806495)
![The new GSMA specifications for RCS include E2EE based on the Messaging Layer Security [MLS] protocol via what's called the Rich Communication Services [RCS] Universal Profile 3.0.
"The new specifications define how to apply MLS within the context of RCS," Tom Van Pelt, technical director of GSMA, said. "These procedures ensure that messages and other content such as files remain confidential and secure as they travel between clients."
<https://www.gsma.com/newsroom/article/rcs-encryption-a-leap-towards-secure-and-interoperable-messaging/>
This also means that RCS will be the first "large-scale messaging service" to have support for interoperable E2EE between different client implementations from different providers in the near future.
The development comes nearly six months after the GSMA said it was working towards implementing end-to-end encryption [E2EE] to secure messages sent between the Android and iOS ecosystems. The move followed Apple's decision to roll out support for RCS in its own Messages app with iOS 18.
Google said, "We've always been committed to providing a secure messaging experience, and Google Messages users have had end-to-end encrypted [E2EE] RCS messaging for years. We're excited to have this updated specification from GSMA and work as quickly as possible with the mobile ecosystem to implement and extend this important user protection to cross-platform RCS messaging." The new GSMA specifications for RCS include E2EE based on the Messaging Layer Security [MLS] protocol via what's called the Rich Communication Services [RCS] Universal Profile 3.0.
"The new specifications define how to apply MLS within the context of RCS," Tom Van Pelt, technical director of GSMA, said. "These procedures ensure that messages and other content such as files remain confidential and secure as they travel between clients."
<https://www.gsma.com/newsroom/article/rcs-encryption-a-leap-towards-secure-and-interoperable-messaging/>
This also means that RCS will be the first "large-scale messaging service" to have support for interoperable E2EE between different client implementations from different providers in the near future.
The development comes nearly six months after the GSMA said it was working towards implementing end-to-end encryption [E2EE] to secure messages sent between the Android and iOS ecosystems. The move followed Apple's decision to roll out support for RCS in its own Messages app with iOS 18.
Google said, "We've always been committed to providing a secure messaging experience, and Google Messages users have had end-to-end encrypted [E2EE] RCS messaging for years. We're excited to have this updated specification from GSMA and work as quickly as possible with the mobile ecosystem to implement and extend this important user protection to cross-platform RCS messaging."](https://friendica-leipzig.de/photo/preview/600/795396)