Suche
Beiträge, die mit Technology getaggt sind
Metr: Electricity Tracker is a new Android app to track Pre-Paid Electricity in South Africa
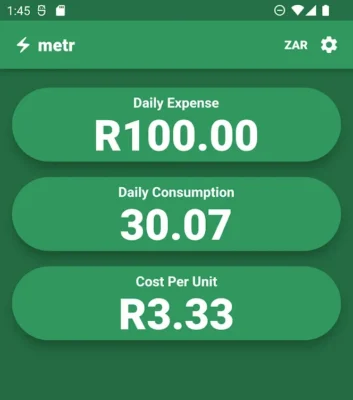
Metr helps you simplify your prepaid electricity budget. All you need to do is create an entry each time you purchase electricity and Metr will automatically calculate your cost per unit, daily expenses and daily consumption. These statistics can help you be more aware of your electricity usage, providing a metric for you to improve and save!
Under useful stats, it also has Time Until Next Refill. This can help you budget and plan, knowing when you will need to purchase electricity again. It will also allow you to know how long your balance is going to last.
This is by a brand-new developer as their first attempt at writing an Android app, so it may have some rough edges, but it could be really useful to many in South Africa.
It is free with adverts so although the dev does not collect or share your data, the Google ad system may well do so. If the app does well enough, maybe the dev will consider doing a paid ad-free version too.
See https://play.google.com/store/apps/details?id=app.metr.metr
#Blog, #electricity, #southafrica, #technology
Cape has been selling a privacy-focused cellphone service to the U.S. military, now offering to high-risk members of the public
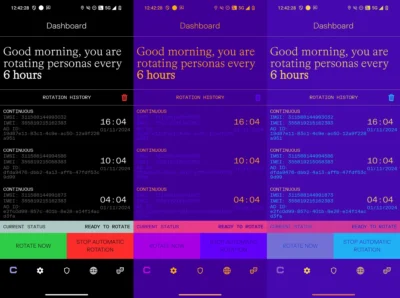
Cape runs its own mobile core, all of the software necessary to route messages, authenticate users, and basically be a telecom. Ultimately, this gives Cape the control to do more privacy-enhancing things, such as periodically give its phones a new IMEI—a unique identifier for the phone—and new IMSI—a similar identifier, but one attached to the SIM card (or eSIM in Cape’s case). The phone can also give itself a new mobile advertising identifier (MAID), which is an identifier advertising ecosystems and apps use to track peoples’ web browsing activity and is sometimes linked to their physical movement data. Cape said the IMEI and MAID rotation is handled by the custom Cape handset, which runs standard up-to-date Android.
Cape lets users create bundles of these identifiers, called “personas”, then cycle through them at different points. This means that during some attacks, a Cape phone may look like a different phone each time.
Well, this is a very interesting phone. Whether governments really want their citizens (or their terrorists or child molesters) to have these devices is another story…
The author also raises an intriguing point about why has AT&T and other phone networks not offered something like this before. The easy answer is wire-tapping requirements (remember the NSA vs PGP encryption in the 1990’s). Google could have offered encrypted email too if it wished, but reading our mail helps fuel its advertising business.
But way more shocking in the linked article, was the statement by the author that they have not owned a smartphone since 2017! I get that you can do a lot on your desktop (like I do), but even I realised that I needed that banking app to do 2FA when approving payments, or SMS for some sites still to authenticate access, and needed Waze to navigate through ever denser traffic, etc. Even the poorest of the poor in our country now at least have a feature phone.
I find it difficult enough telling many people, no, really, I don’t have WhatsApp when they want to send receipts to me via WhatsApp.
See https://www.404media.co/i-dont-own-a-cellphone-can-this-privacy-focused-network-change-that
#Blog, #privacy, #technology
DXOMARK’s Apple iPhone 16 Camera test

Although I no longer use an iPhone, I do always find DXOMARK’s benchmark testing interesting for the various flagship phones. It shows too that a megapixel number is not what you should compare one phone against another on.
I always try to compare based on like for like tests done between the various devices.
Spoiler: iPhone 16 falls behind the Pixel 9 and 8 cameras. But still it is worth “zooming” in on the aspects that are important to you as none of the phones perform equally across all the different aspects measured.
See https://www.dxomark.com/apple-iphone-16-camera-test
#Blog, #camera, #photography, #technology
4 reasons why you should use Docker containers on your PC
I use Docker containers exclusively on my servers, but have yet to explore using them on my desktop computer or a Raspberry Pi. I do use Flatpaks quite a bit, and there seems to be a case for Docker containers being lighter than Flatpaks even (not sure about this yet).
But certainly, Docker containers are ultra-lightweight (just think also how quickly they spin up).
And yes, they do isolate their environment and prevent any chance of conflicting packages.
If you use Docker containers on your desktop, let me know which you are finding useful for a desktop environment.
See https://www.xda-developers.com/reasons-why-you-should-set-up-docker-containers-on-your-pc
#Blog, #containers, #docker, #technology
https://lindseygamble.beehiiv.com/p/instagram-debunks-the-myth-around-sponsored-posts?utm_source=flipboard&utm_medium=activitypub
Posted into LINDSEY GAMBLE'S CREATOR ECONOMY NEWSLETTER @lindsey-gamble-s-creator-economy-newsletter-LindseyGamble_

Instagram Debunks the Myth Around Sponsored Posts 👀
Instagram joins TikTok and YouTube in debunking the myth that its disclosure tool impact the performance of sponsored content.Lindsey Gamble's Newsletter
You want to amplify the opposite? Then build, raise awareness about, and help fund the opposite:
Small Tech.
https://small-tech.org/about/#small-technology
#BigTech #SmallTech #fascism #democracy #humanRights #technology

About
We’re a tiny and independent two-person not-for-profit based in Ireland. We’re working on building the Small Web.Small Technology Foundation
How to update your SSD firmware on Windows

Software updates are an integral part of modern life, with your computer’s operating system and your smartphone being smart enough to update on its own. But that’s not the case for every piece of electronics, and many need a manual touch to get them updated. Pretty much every computing device you own, from the best M.2 SSDs to your computer’s motherboard and the router powering your home network, all runs on a combination of firmware and hardware. It’s called firmware instead of software because it’s designed to be permanently embedded in the device that it controls and updated only periodically.
These firmware updates can fix performance-related issues, security holes, or other types of bugs. Because they’re not scheduled regularly, it’s even more important that you update the firmware when a new version arrives. For SSDs, firmware controls how data is stored and read, as well as other functions that the SSD controller needs to operate efficiently to give you the best performance possible. Every SSD manufacturer has a slightly different way of handling updates, but they all have one thing in common–they’re quick and easy to do.
This is a bit of a Catch-22: Updating firmware on a SSD does have a slight chance of borking the drive, and some say it is better not to mess with something that is working OK…
See https://www.xda-developers.com/how-update-ssd-firmware
#Blog, #SSD, #technology
from #NewYorkTimes #NYT
[gift article - link can be shared. Expires in 30 days]
Trying to avoid antitrust suits, #Google systematically told employees to destroy messages, avoid certain words and copy the lawyers as often as possible.
By David Streitfeld
#DavidStreitfeld has written about Google since it was a start-up.
Nov. 20, 2024 Updated 9:19 a.m. ET
https://www.nytimes.com/2024/11/20/technology/google-antitrust-employee-messages.html?unlocked_article_code=1.bU4.j2LO.yf7ztU404uYS&smid=url-share
#news #press #technology
🔗 https://blog.allthingstech.social/my-first-few-days-with-the-mac-mini/
#Tech #Technology #AllThingsTech #Blog #TechBlog
My First Few Days With The Mac Mini
https://blog.allthingstech.social/my-first-few-days-with-the-mac-mini/
#Tech #Technology #AllThingsTech #Blog #Blogger #Blogging #Author #Writer #WordPress
https://blog.samclemente.me/macos-might-have-an-apps-problem-in-the-world-of-apple-intelligence/
#Apple #Technology #ArtificialIntelligence #AppleIntelligence #Blog

macOS Might Have an Apps Problem in the World of Apple Intelligence
Apple has been pushing for the dominance of native apps on iOS, but macOS isn't quite the same—can it hold up in the world of Apple Intelligence?Sam Clemente (The Digital Renaissance)
Thankfully, we have an amazing 1-year MA program on just this subject in Washington #DC. Check it out:
https://www.american.edu/soc/communication-studies/ma/ma-mtd.cfm #academia #academicchatter #highered #commodon @academicchatter @commodon

EU disease agency considers quitting Elon Musk’s X over disinfo
The spread of scientific misinformation on the social media platform is making the ECDC think twice, its director says.Elena Giordano (POLITICO)
https://blog.samclemente.me/apple-intelligence-might-give-ipados-the-edge-over-macos-it-needed/
#Apple #Technology #ArtificialIntelligence #AppleIntelligence #Blog #IndieWeb
Apple Intelligence Might Give iPadOS the Edge Over macOS it Needed
iPadOS may have an easier time implementing certain Apple Intelligence features, which could potentially give it a competitive edge over the Mac for some peopleSam Clemente (The Digital Renaissance)
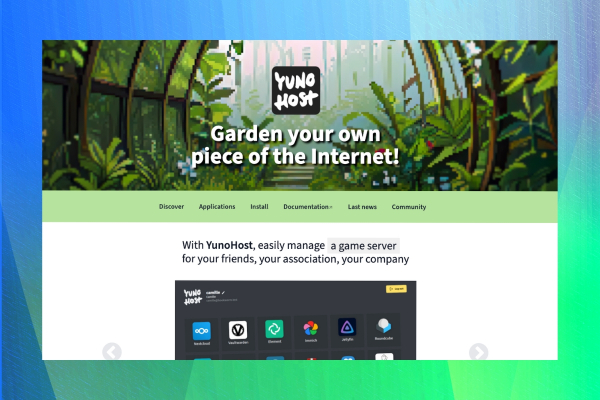
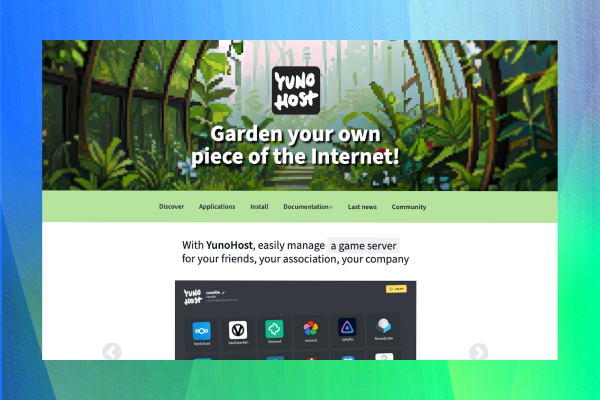
🔗 https://blog.allthingstech.social/yunohost-an-easy-way-to-self-host-apps/
#Tech #Technology #AllThingsTech #Blog #TechBlog
YunoHost: An Easy Way to Self-Host Apps
https://blog.allthingstech.social/yunohost-an-easy-way-to-self-host-apps/
#Tech #Technology #AllThingsTech #Blog #Blogger #Blogging #Author #Writer #WordPress
https://atix.de/en/blog/winrm-ansible-wege-der-authentifizierung-und-verschluesselung/
#windows #ansible #domain #user #authentication #certificate #blog #techblog #technology
WinRM & Ansible – 🔑 Authentication and 🔒 Encryption | ATIX AG
Ansible on Windows: Simple authentication and encryption for the configuration and administration of Windows systems.Daniel Schumacher (ATIX AG)
You can actually turn an old phone into a NAS

If you’re a tech enthusiast like me, chances are you have an old phone or two lying around unused. While it’s not necessarily the best use for it, you can definitely take one of those older devices and use it as a rudimentary NAS (network attached storage device) for sharing data across all your devices.
On top of that, if you really want to take things a step further, you can root an old Android phone and set up Docker on it. From there, you can host normal applications that you would on any other NAS and deploy them on your network, including running things like Pi-hole or Jellyfin. They’re making just a NAS out of an Android phone, but you can easily host a Nextcloud Pi server on your smartphone if it’s rooted.
We forget that yesterday’s flagship, or even mid-range, phones are actually pretty powerful devices, often a fair bit of storage. With a USB hub plugged in, you can attach storage, an Ethernet connection, and more.
Repurposing an old phone, instead of throwing it out, is certainly also cutting down on e-waste.
See https://www.xda-developers.com/how-turned-old-phone-nas
#Blog, #environment, #NAS, #technology
“Check out some of the apps that I use to customize the macOS experience”
https://blog.allthingstech.social/apps-i-use-to-customize-macos/
#AllThingsTech #Apple #Apps #Blog #FOSS #Mac #MacOS #Technology
Apps I Use to Customize macOS
https://blog.allthingstech.social/apps-i-use-to-customize-macos/
#Tech #Technology #AllThingsTech #Blog #Blogger #Blogging #Author #Writer #WordPress
🔗 https://blog.allthingstech.social/apps-i-use-to-customize-macos/
#Tech #Technology #AllThingsTech #Blog #TechBlog
eSIM security vs. a physical SIM: An eSIM is safer

Apart from, the convenience of being able to easily enable an eSIM (without waiting for a physical SIM delivery), the ease of switching SIM profiles when travelling, and not having a physical card that gets damaged, these eSIMs also have some security advantages too.
eSIM (embedded subscriber identity module) technology employs various additional security measures that make it less prone to hacking than physical SIMs. Those measures include a secure element, which stores sensitive data and protects it from unauthorized access or tampering, adding an extra layer of protection against hacking attempts.
They cannot be cloned, as they cannot be physically accessed from outside the phone. Also, if your phone is stolen, it is not like a physical SIM where a thief can just remove the SIM card (the eSIM is always active inside the phone).
In other aspects they are quite similar to physical SIM cards, for example, with SIM swapping, as SIM swapping is done virtually on the network side and has little to do with the SIM in your phone.
But remember that no online device is ever fully immune to hacking. So whilst eSIMs are a step up from physical SIM cards, they may not be fully immune.
See https://nordvpn.com/blog/is-esim-safe
#Blog, #eSIM, #security, #technology
Google is CRIPPLING their Find My Device network with ‘aggregation by default’ setting
From the beginning, Google has prioritized being privacy-conscious with the Find My Device (FMD) network, including delaying the launch until the iPhone gained unknown tracker alerts. Google chose “aggregation by default” to the detriment of Find My Device performance, and is seemingly doubling down on that decision.
The default Find My Device network setting is “With network in high-traffic areas only.” Multiple Android devices have to detect an object before its location is shared. So far, users have found this ineffective in real-world usage, with trackers not being located.
Unlike Apple who has this type of setting as opt-out by users, and which results in a far more extensive network to find your lost items, Google has restricted it to opt-in. Looking at reviews about the Motorola Moto tags, I see this issue cropping up a lot. Great tags, but the Google network is just not locating your device until multiple Android users have passed it.
It is not as if any 3rd party is going to identify you or your location whether this setting is enabled or not. Your identity and location is never passed to the others users.
What it means is that Google is basically crippling their network, whilst Apple’s is functioning extremely well. With Apple being who they are, they seem to be happy with the default settings reporting the location of a lost tag with just one iOS device passing by.
We are all familiar with default settings, and with this one as it is, it means Google’s network is never really going to function well. You can really forget about expecting a few billion people to all changing this setting themselves. It would have been better to activate it properly and put a notice on the start-up screen to inform what it does.
See https://9to5google.com/2024/07/09/google-find-my-device-aggregation-default
#Blog, #findmydevice, #technology, #trackers
7 free open-source tools for amazing photo and video edits
While there is no shortage of powerful photo and video editing tools, most of them come with a hefty price tag or require a subscription to get started. It may discourage students, beginners, and freelancers from exploring them fully. Luckily, thanks to free, open-source tools, you don’t need to shell out hundreds of dollars to achieve stunning results.
XDA Developers have short-listed their choices in the linked article below, and explained why each has been chosen.
I’d certainly also add digiKam for photo editing. It has some very powerful features, including advanced geolocation editing, batch editing, blending of stacked images, OCR text generation, creation of calendars, creation of panoramas, RAW editing, camera control, and exporting to numerous cloud services including Flickr, Imgur, Piwigo, Pinterest, etc.
See https://www.xda-developers.com/free-open-source-tools-for-amazing-photo-and-video-edits
#Blog, #opensource, #photography, #technology
https://www.wheresyoured.at/lost-in-the-future/
---
"All I know is that I feel like I am at war, and we — if I can be considered part of the media — are at war with people that have changed the terms of innovation so that it’s synonymous with value extraction. Technology is how I became a person, how I met my closest friends and loved ones, and without it I would not be able to write, let alone be able to write this newsletter, and I feel poison flow through my veins as I see what these motherfuckers have done and what they will continue to do if they’re not consistently and vigorously interrogated."
Agreed. It all took a wrong turn somewhere and we need to figure out how to get back to empowering people rather than value extraction.
#enshittification #technology #journalism

Lost In The Future
Soundtrack: Post Pop Depression - Paraguay I haven't wanted to write much in the last week. Seemingly every single person on Earth with a blog has tried to drill down into what happened on November 5 — to find the people to blame, to somehow e…Edward Zitron (Ed Zitron's Where's Your Ed At)
"How dare you use Twitter to spread your message. How dare you maintain a crypto product. I'm disappointed in you."
"You're using Google's services and therefore you don't care about privacy. AI? The horror! You don't belong here."
We gotta understand:
- Firstly, it's none of our business
- Second, who are we to judge.
I have faced this a lot of times. I receive blatant evisceration and harsh criticism and questions because I was asking for help or making a remark about my use of a big tech service. Well, it may not have been that bad, but in a situation where you're asking for and expecting help, and you I stead receive this, it definitely sucks.
There were times when I had to literally tell people that their comments are useless for me, because they really were.
We gotta understand that not all people can switch to Firefox, or daily drive GrapheneOS, or search in DuckDuckGo, or migrate to Proton Mail, or from Twitter to Mastodon.
And that should be okay with us. We can't force stuff onto people. We might instead respect individual choices while equipping them with the required information and reasons to switch to better alternatives.
No open source software (or proprietary, for that matter) is perfect. Better to acknowledge the shortcomings and collectively improve instead of vigorously fighting on them. BROWSER WARS ARE STUPID.
It would do us and the community at large a huge service if we took the time to understand the entire context before jumping in with free advice.
We are SO divided over silly things sometimes. We can do better by our people. Let's work to make this a more constructive and helpful space.
Peace.
#Privacy
#Mastodon
#Fediverse
#Technology
#Community
#Positivity
#FOSS
https://www.propublica.org/article/microsoft-solarwinds-golden-saml-data-breach-russian-hackers
#Tech #News #Cybersecurity #Hacking #Data #Technology
#News #Technology #Government #Biden #Tech
https://propub.li/4evDWGW

Biden Asked Microsoft to “Raise the Bar on Cybersecurity.” He May Have Helped Create an Illegal Monopoly.
When the White House welcomed Microsoft’s offer of $150 million in tech services, it helped the world’s largest software provider tighten its grip on federal business and freeze out competitors.ProPublica
11 Must-Have Docker Tools To Simplify Your Workflow And Why CLI Is Good
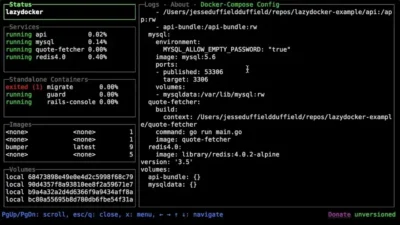
Docker is a popular tool for creating, deploying, and managing containerised applications, but managing containers, images, and configurations can become complex over time.
Here’s a detailed guide to some essential Docker tools that simplify your work, whether you’re a beginner or experienced. These tools help you monitor, troubleshoot, and manage Docker more effectively.
I do monitor and work with three different docker based servers, and activating the VPN, then opening Portainer or whatever to work on each one, can all take time. So I’m testing some of the CLI based tools listed in the linked article.
The reason is I can open a terminal window and just type ‘ssh het’ or whatever the shortcut is which I use, and instantly that opens a public private key based session into that server. I can quickly run (or keep open) the CLI app to monitor my containers. I could have three terminal windows open, one for each server, at the same time if I wish.
It is why terminal windows and apps can be super useful and lightweight for many occasions.
See https://www.tecmint.com/docker-tools
#Blog, #docker, #servers, #technology

Europe’s press goes after Musk’s X
Media organizations turns up the heat on X amid cries of ‘toxic’ content.Mathieu Pollet (POLITICO)
Online shopping syndicate warning in South Africa

Hot on the heels of today’s report about some incredibly weak passwords that South Africans are using online, and then re-using across other websites, comes this warning now about very realistic looking fake online shopping sites that closely resemble the real brand.
We have Black Friday coming up, as well as the festive season, so everyone is looking out for bargains. We should never be clicking on links we receive over instant messengers or e-mails, but now you want to be doubly sure you are actually on Takealot, or whatever site you expect to be on.
I’d suggest you check the URL carefully before making purchases, and rather use your saved bookmarks to access sites you regularly use. Your password manager refusing to show a login, is also a sign you may be on a fake site.
See https://mybroadband.co.za/news/security/570114-online-shopping-syndicate-warning-in-south-africa.html
#Blog, #scams, #southafrica, #technology
@zackwhittaker
@oliverdarcy
@karaswisher
@joanwestenberg @_elena
@ben
Download the app and give them a follow to see posts from your favorite fediverse folks while catching up on headlines, recipes, tech news, film reviews and more.
https://about.flipboard.com/download-flipboard/
#Flipboard #Fediverse #Federation #ActivityPub #Technology #Media #Journalism #Journalist #Tech
Download Flipboard - About Flipboard
Download Flipboard, the award winning app that gives you curated news, personalized content and deep dives all in one place.About Flipboard
Google’s Gemini AI Chatbot Finally Has an iPhone App
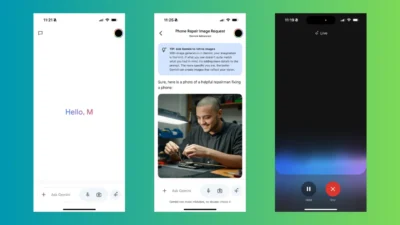
Billed as a way to converse with Google’s AI, it’s kind of like using speech-to-text, but without having to press a microphone icon before each question. Just say your questions out loud, and Gemini will respond to them in real time, incorporating context from your previous questions.
Exclusive to the iPhone app is some clever use of the Dynamic Island. While you’re talking to Gemini, you’ll see icons in the Dynamic island indicating that Live is still active and whether it’s listening to you.
So far I’ve been Gemini the most useful for decent answers to things, including helping out with getting various code snippets sorted out. But it is pretty good for most things you’d ask of any smart speaker.
I see it can also be used to report road conditions and issues in Waze, something which I need to try instead of doing the three button presses on the car dashboard.
See https://lifehacker.com/tech/googles-gemini-finally-has-an-iphone-app
#Blog, #AI, #ios, #technology
https://atix.de/en/blog/the-future-of-software-architecture-focus-on-event-driven-architecture/
#devops #software #softwaredevelopment #eventdriven #blog #tech #technology
The future of event-driven architecture | ATIX AG
The article explains the Event-Driven Architecture (EDA) and its advantages for flexible, scalable and responsive systems.Michael Morlock (ATIX AG)