Suche
Beiträge, die mit security getaggt sind
iOS-Dating-Apps für LGBTQ+-, BDSM- und Sugar-Daddy-Communitys haben viele Nutzerfotos kompromittiert. Darunter sind explizite Bilder aus privaten Nachrichten.
https://www.heise.de/news/Datenleck-1-5-Millionen-private-Fotos-von-Dating-Apps-fuer-LGBTQ-enthuellt-10333383.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Journal #Security #news
Mehrere Schwachstellen bedrohen die Softwareentwicklungsplattform Gitlab. Gegen mögliche Attacken gerüstete Versionen stehen zum Download.
https://www.heise.de/news/Sicherheitsluecken-Gitlab-Heruntergestufte-Admins-behalten-weitreichende-Rechte-10332147.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Git #IT #Patchday #Security #Sicherheitslücken #Updates #news
Updates für Firefox schließen eine Sandbox-Lücke unter Windows. Sie ähnelt derjenigen, die in Google Chrome angegriffen wird.
https://www.heise.de/news/Firefox-Mozilla-schliesst-kritische-Sandbox-Luecke-in-Windows-Version-10331842.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Chrome #Firefox #IT #Mozilla #Security #Sicherheitslücken #news
Solarspeicher verteilen die Stromlast über den Tag. Beschädigte Geräte können jedoch brandgefährlich werden, auf eine Reparatur muss man sich nicht einlassen.
https://www.heise.de/news/Vorsicht-Kunde-Brandgefaehrlicher-Solarstromspeicher-10330214.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#IT #Journal #Verbraucherschutz #Photovoltaik #Podcast #Security #Solarenergie #Stromversorgung #VorsichtKunde #Wirtschaft #Wissen #news
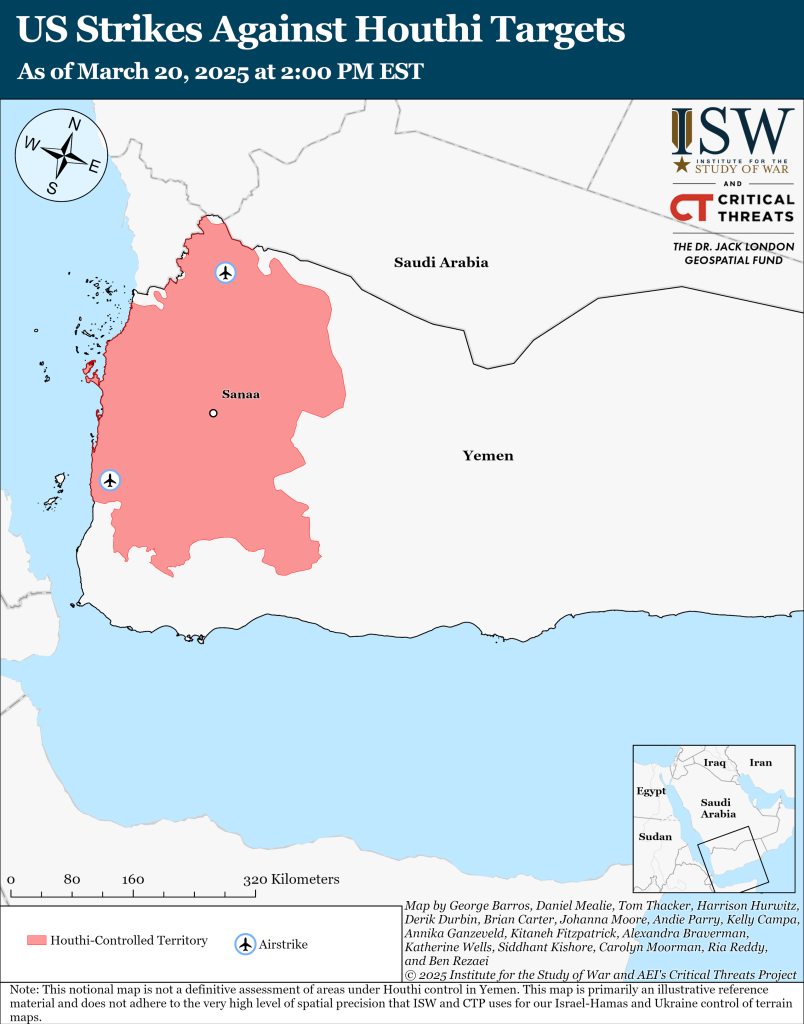
Iran Update, March 27, 2025
Iran Update March 27, 2025 Ria Reddy, Siddhant Kishore, Kelly Campa, Annika Ganzeveld, Carolyn Moorman, Alexandra Braverman, Andie Parry, Katherine Wells, Ben Rezaei, Avery Borens, Alexis Thomas, and Brian Carter Information Cutoff: 2:00 pm ET The Cr…BYTESEU (Bytes Europe)
- Also make shure it uses #OpenStandards, because #OpenSource can be just a "smoke grenade" when it's a #centralized, #proprietary, #SingleVendor & #SingleProvider solution.
- Both of the latter points are something that @monocles / #monoclesChat does perfectly and that @signalapp completely fails at!
On Monday, shortly after we published a story about a massive #Trump-admin #security breach, a reporter asked the secretary of #defense, #PeteHegseth, why he had shared plans about a forthcoming attack on #Yemen on the Signal messaging app. He answered, “Nobody was texting war plans. And that’s all I have to say about that.”
#law #NationalSecurity #SignalGate #idiocracy #kakistocracy #intelligence #JeffreyGoldberg #TheAtlantic
Unitree sieht die Verwendung von humanoiden Robotern im Haushalt als schwierig an. Die Roboter müssen so konzipiert sein, dass sie niemanden verletzen.
https://www.heise.de/news/Unitree-will-vorerst-keine-humanoiden-Haushaltsroboter-rausbringen-10328864.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Roboter #Security #Wirtschaft #Wissen #news

We need to pay closer attention to Svalbard
NATO members and other allies would do well to start thinking about how they’d respond if Russia took action against one of its most remote geographies.Elisabeth Braw (POLITICO)
Trump backs 'good man' Mike Waltz, rips 'sleazeball' Atlantic in alleged security breach President Donald Trump holds an ambassadors meeting where he addresses the Atlantic article which alleged war plans were accidentally texted to a journalist. #trump #foxnews #journalist #security Subscribe to Fox News! Watch more Fox News Video: Watch Fox News Channel Live: FOX News…
https://www.shibuyaworldnews.online/fox-trump-backs-good-man-mike-waltz-rips-sleazeball-atlantic-in-alleged-security-breach/

#FOX Trump backs ‘good man’ Mike Waltz, rips ‘sleazeball’ Atlantic in alleged security breach - SHIBUYA World News
https://www.youtube.com/watch?v=WtRvlYidXKk Trump backs 'good man' Mike Waltz, rips 'sleazeball' Atlantic in alleged security breach President Donald Trump holds an ambassadors meeting where he addresses the Atlantic article which alleged war plans w…🐈 (SHIBUYA World News)
A great headline - the and is doing multiple jobs here
the messaging app’s co-founder said on X: “There are so many great reasons to be on Signal. Now including the opportunity for the vice-president of the United States of America to randomly add you to a group chat for co-ordination of sensitive military operations. Don’t sleep on this opportunity.”
http://archive.today/2025.03.25-132922/https://www.thetimes.com/uk/social-media/article/what-is-signal-app-group-chat-jz6fdfkrz
#Signal #Security #Privacy
According to LayerX Labs, who have been tracking this campaign for more than a year, the phishing attack attempts to trick Mac users into thinking that their computers have been “locked” via a fake security warning that pops up while users are browsing the web.
https://layerxsecurity.com/blog/layerx-identifies-new-phishing-campaign-targeted-at-mac-users/
#apple #macos #it #security #privacy #engineer #media #tech #news
LayerX Labs Identifies New Phishing Campaign Targeted at Mac Users - LayerX
A new phishing attack campaign, targeting Mac users and identified by LayerX Labs, shows the trials and tribulations of combating online phishing, and how attacks morph and shift in response to adaptations by security tools.Or Eshed (LayerX)
Die IT-Security-Konferenzmesse secIT lockte abermals tausende Admins und CISOs nach Hannover und war ein voller Erfolg. Im Herbst geht es weiter.
https://www.heise.de/news/Rueckblick-secIT-2025-Patentrezepte-gegen-Cybercrime-und-21-kg-Espressobohnen-10326431.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Cyberangriff #Cybercrime #IT #Ransomware #Security #news

Six Short Thoughts on the Most Insane Trump Story of All Time
Trump's "Team of Amateurs" Screwed Up in the Most Hilarious (and Troublesome) WayDoomsday Scenario
FBI warnings are true—fake file converters do push malware

“The FBI is warning that fake online document converters are being used to steal peoples’ information and, in worst-case scenarios, to deploy ransomware on victims’ devices. The warning came last week from the FBI Denver field office, after receiving an increasing number of reports about these types of tools.”
It seems that many of these relate mostly to creating to or from PDF files, but really most good word processors already do that as a built-in function, e.g. free LibreOffice.
See https://www.bleepingcomputer.com/news/security/fbi-warnings-are-true-fake-file-converters-do-push-malware
#Blog, #malware, #security, #technology
https://techcrunch.com/2025/03/19/researchers-name-several-countries-as-potential-paragon-spyware-customers/
#Toronto #AU #CA #CY #DK #IL #SG #government #academic #security #research #surveillance #SurveillanceCapitalism #WhatsApp #Italy #IT #VentureCapital #authoritarian #authoritarianism

Researchers name six countries as likely customers of Paragon's spyware | TechCrunch
The Citizen Lab said it believes several governments may be customers of spyware maker Paragon Solutions.Lorenzo Franceschi-Bicchierai (TechCrunch)
#Australia #Trump #US #ForeignPolicy #Geopolitics #Trade #Security #Alliances #AUKUS #GlobalPolitics #Politics #Economy
https://the-14.com/at-what-point-do-we-say-enough-to-trump/
At what point do we say ‘enough’ to Trump? | The-14
Australia must decide its red lines as Trump’s policies test alliances, trade, and security. How far will it bend before saying “enough” to US demands?The 14 (The-14)
Das EU-Parlament hat seine Abgeordneten und Mitarbeiter zum Messenger-Dienst Signal geraten, wenn Jabber und Teams nicht funktionieren. Das sorgt für Kritik.
https://www.heise.de/news/Debatte-um-sichere-Kommunikationstools-im-EU-Parlament-10324200.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Netzpolitik #Security #Signal #Verschlüsselung #news
Anfang März hatte das BSI vor Fake-Captcha gewarnt. Worauf man achten sollte, erklärt Benedict Padberg von Friendly Captcha.
https://www.heise.de/hintergrund/Interview-Warum-traditionelle-Bild-Captchas-verschwinden-sollten-10323101.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#BSI #Security #Wirtschaft #news
Durch ein neues Gesetz in Frankreich können Behörden Zugriff auf eigentlich verschlüsselte Kommunikation erhalten. Dagegen regt sich online massiver Widerstand.
https://www.heise.de/news/Messenger-App-Signal-droht-mit-Rueckzug-aus-Frankreich-wegen-Drogenhandelsgesetz-10323566.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Kriminalität #Messaging #Mobiles #Netzpolitik #Security #Signal #Überwachung #Verschlüsselung #WhatsApp #news
Iran Update, March 20, 2025 - EUROPE SAYS
Iran Update March 20, 2025 Katherine Wells, Carolyn Moorman, Ben Rezaei, Johanna Moorman, Siddhant Kishore, Kelly Campa, AveryEUROPE SAYS (EUROPESAYS.COM)
Text messages sent between iOS & Android devices will soon benefit from end-to-end encryption, after the GSM Association published new specifications for the RCS protocol that include support for cross-platform E2EE.
https://www.gsma.com/solutions-and-impact/technologies/networks/gsma_resources/gsma-rcs-universal-profile-3-0-specifications/
#ios #android #rcs #protocol #it #security #privacy #engineer #media #tech #news
#Cybersecurity #Journal #Netzpolitik #Security #news
Oh weh, da kann man den Menschen nur alles Gute und viel Glück wünschen. Im Kreml lacht man sich bestimmt den Rücken krumm.
Liebe Leute, lasst euch das eine Warnung sein, was passiert, falls hier jemals die #AFD irgendetwas relevantes zu sagen bekommt. Die werden denn Staat genauso auf links ... äh ... rechts drehen und alles zerstören, was über Jahrzehnte mühsam aufgebaut wurde!
The U.S. mentioned "FALCO," a new APKWS II variant under a BAE Systems program to enhance air-launched counter-drone operations.
https://defensemirror.com/news/39092/U_S_A_F_Uses_Laser_Guided_Rockets_against_Houthi_Drones__Houthis_Claim_16th_MQ_9_Reaper_Downed
#USAF #Military #Defense #Drones #UAV #AirForce #Iran #Houthi #MQ9Reaper #RedSea #MissileDefense #CounterUAV #Security #MiddleEast #CENTCOM #F16 #AirDefense #Technology #Geopolitics #laserguided #APKWSII #Israel #Reaper #PredatorB
U.S.A.F Uses Laser-Guided Rockets against Houthi Drones; Houthis Claim 16th MQ-9 Reaper Downed
APKWS II rocket, originally an air-to-ground weapon, was recently adapted for air-to-air use against drones.defensemirror.com
So, looks like for now the only increase in defence spending that will be spent in the UK is out own...
But, hey those Europeans, eh? Glad to see the back of them.... /s
#Brexit #defence #security #politics
The plan was led by Biden's #NSC & involved at least 7 national security agencies working w/European allies to disrupt plots targeting #Europe & the #UnitedStates….
#security #USpol #geopolitics #Russia #sabotage #disinformation #cyberattacks #NewWorldOrder #Trump #PutinsPuppet
counter Russian sabotage as #Trump moves closer to #Putin
Several US #NationalSecurity agencies have halted work on a coordinated effort to counter Russian #sabotage, #disinformation & #cyberattacks, easing pressure on Moscow as the Trump Admin pushes #Russia to end its war in #Ukraine.
#intelligence #security #USpol #geopolitics #NewWorldOrder #PutinsPuppet
https://www.reuters.com/world/us-suspends-some-efforts-counter-russian-sabotage-trump-moves-closer-putin-2025-03-19/

EU opens fiscal tap to secure Europe but warns against ‘defense washing’
Economy Commissioner Valdis Dombrovskis stressed the flexibility is a stop-gap until countries reframe budgets around higher defense needs.Giovanna Faggionato (POLITICO)
Ukraine Daily summary - Wednesday, March 19 2025
Wednesday, March 19
Russia’s war against Ukraine

Russian President Vladimir Putin speaks during the plenary session of Russia Union of Industrialists and Entrepreneurs, March 18, 2025, in Moscow, Russia. Putin spoke prior to his telephone call with U.S. President Donald Trump. (Contributor/Getty Images)
Trump-Putin call: Russia agrees to 30-day pause of energy infrastructure strikes. "Vladimir Putin responded positively to this initiative and immediately gave the appropriate command to the Russian military," the Kremlin said.
Kremlin demands halt to foreign military aid**, intelligence to Ukraine as condition for avoiding war escalation.** The Kremlin has demanded a complete cessation of foreign military aid and intelligence to Ukraine as a "key condition for avoiding an escalation of the war," according to a statement released on March 18.
Kyiv supports energy sector ceasefire**, expects military aid to continue, Zelensky says.** "We will support such a proposal, but we're very interested in the details," Zelensky said after the Trump-Putin call.
US announces another round of negotiations in Middle East on war in Ukraine. "This conflict should never have started and should have been ended long ago with sincere and good faith peace efforts," the White House's statement read.
'I don't want us to be on Putin's menu' — Zelensky says negotiations must include Ukraine. "We are an independent state. Without us, I think it's wrong to negotiate," President Volodymyr Zelensky said on March 18.
Your contribution helps keep the Kyiv Independent going. Become a member today_._
Putin didn't mention military aid in phone call, Trump says. Trump also said it was "a great call" and that the U.S. hopes to expand trade with Russia, including deals on "very big forms of rare earth."
Ukraine withdraws from one front-line sector in Donetsk Oblast, commander says. "This allowed us not only to save our soldiers, but also to improve our defense. (Russia) is suffering losses, and we can act more effectively," Lieutenant General Serhii Naiev said.
Ukrainian forces attempted to enter Belgorod Oblast**, repelled by Russian forces, Russia claims.** The Russian Defense Ministry claimed on March 18 that the Ukrainian Armed Forces attempted to enter Russia's Belgorod Oblast but were repelled by the Russian military.
Zelensky arrives in Finland for official visit to discuss security and strengthen ties. President Volodymyr Zelensky and First Lady Olena Zelenska arrived in Finland for an official visit on March 18. The plane carrying the couple landed at Helsinki-Vantaa Airport in the afternoon.
Russian energy giant Gazprom suffers $13.1 billion loss in 2024. Gazprom's losses averaged $251 million per week, $35 million per day, or $1.4 million per hour. While the company's total revenue increased by 11% and its gas revenue by 14%, it still ended the year with a sales loss of 192 billion rubles ($2.3 billion).
Read our exclusives

Meet the Ukrainian fashion brand that's making heritage trendy
Natalia Kamenska had grown tired of a fashion industry she felt was too focused on mass production and commercial interests, rather than creativity. While in the Carpathian mountains, Kamenska encountered a “gunia,” a traditional western Ukrainian shag fur coat that weighs around six kilos (13 pounds).
Photo: Gunia
Learn more

Polish right takes hard line on Ukraine ahead of presidential vote
With the Polish presidential elections just two months away, two of the country's leading right-wing candidates have become increasingly antagonistic toward Ukraine and its leadership. Both men have made headlines by public spats with Ukrainian officials and denounced Kyiv as ungrateful for Polish aid.
Photo: Beata Zawrzel/NurPhoto via Getty Images
Learn more

Ukraine war latest: Putin, Trump hold 1.5-hour call, discuss ceasefire in Ukraine
Russian President Vladimir Putin has agreed to a 30-day pause of energy infrastructure strikes during a call with U.S. President Donald Trump, according to a readout of the call issued by the Kremlin on March 18.
Photo: Maxim Shemetov/Pool/AFP via Getty Images
Learn more

Human cost of Russia’s war
2 killed, 13 injured in Russian attacks across Ukraine over past day. Ukrainian air defenses shot down 63 of the 137 Russian attack and decoy drones overnight over 12 oblasts, the Air Force said. Sixty-four decoy drones reportedly disappeared from radars without causing damage.
General Staff: Russia has lost 897,010 troops in Ukraine since Feb. 24, 2022. The number includes 1,560 casualties Russian forces suffered just over the past day.
International response
UK reportedly hopes US drones, satellites will help monitor Ukraine ceasefire. The U.S. military has 247 military satellites and thousands of commercial satellites, providing an "unrivaled picture" of eastern Ukraine that European forces would struggle to replicate, the Times wrote.
UK, EU to discuss confiscating Russian assets ahead of Ukraine peace talks, Bloomberg reports. Negotiations will focus on establishing the legal and financial framework to seize Russian assets, despite opposition from some EU member states, particularly Belgium and Germany.
Italy, Spain hesitant on EU's $43 billion military aid to Ukraine plan. Italian Foreign Minister Antonio Tajani said the proposal needed further discussion and that Italy was awaiting the outcome of the upcoming call between U.S. President Donald Trump and Russian President Vladimir Putin.
Trump boasts of saving 'surrounded' Ukrainian soldiers despite Kyiv denying encirclement in Kursk Oblast. U.S. President Donald Trump claimed on March 17 that he took an unspecified action to save "surrounded" Ukrainian soldiers, apparently referring to his earlier and unsubstantiated claims of Kyiv's troops being encircled in Russia's Kursk Oblast.
Trump's aid cuts threaten supply of HIV treatments to Ukraine**, 7 more countries, WHO warns.** The World Health Organization warned that Kenya, Haiti, Lesotho, Burkina Faso, Mali, Nigeria, South Sudan, and Ukraine could run out of critical antiretroviral drugs in the coming months.
Russian negotiator says he expects talks with Musk on space, tech. Kirill Dmitriev, the CEO of the Russian Direct Investment Fund (RDIF), said he expects Russia to hold talks with U.S. billionaire and President Donald Trump's ally, Elon Musk, in the near future, the pro-state news agency RBK reported on March 18.
In other news
Notorious judge dismissed amid accusations of criminal activity, power grab. Judge Pavlo Vovk was held responsible for "committing a significant disciplinary offense, gross or systematic neglect of duties that is incompatible with the status of a judge or revealed his incompatibility with the position he holds."
France to deploy fighter jets with nuclear warheads on German border by 2035, Macron says. France will deploy Rafale fighter jets equipped with supersonic nuclear warheads along its border with Germany in 2035, French President Emmanuel Macron announced on March 18 at the Luxeuil-Saint-Sauveur Airbase, according to BFMTV.
Telegram CEO Durov returns to Dubai amid French investigation. Pavel Durov, Telegram's Russian-born founder and CEO, said that the investigating judges allowed him to depart even though the probe is ongoing.
Poland, Baltics to withdraw from anti-personnel mine ban treaty. The defense ministers of the four nations argued that the security situation in the region has "fundamentally deteriorated" and that military threats to NATO member states bordering Russia and Belarus have "significantly increased."
EU approves over $2 billion in economic support for Moldova. The Reform and Growth Facility, which includes 1.5 billion euros ($1.6 billion) in low-interest loans and 385 million euros ($420 million) in grants, will cover the period of 2025-2027 and is part of the EU's long-term Moldova Growth Plan.
Ukraine Daily is made possible thanks to support of our readers.
For as little as $5/month you can help us keep going.
SUPPORT US
Your donation is processed by a U.S.-based secure payment system.
We have no access to your bank data.
This newsletter is open for sponsorship. Boost your brand's visibility by reaching thousands of engaged subscribers. Click here for more details.
Today’s Ukraine Daily was brought to you by Martin Fornusek, Teah Pelechaty, Tymur Zadorozhnyy, Kateryna Hodunova, Abbey Fenbert, and Olena Goncharova.
If you’re enjoying this newsletter, consider joining our membership program_**. Start supporting independent journalism today.**_
Firings & buyouts hit the top-secret National Nuclear Safety Admn amid a major effort to upgrade America’s #nuclear arsenal. Critics say it shows the consequences of heedlessly cutting the federal work force.
https://www.nytimes.com/2025/03/17/us/politics/federal-job-cuts-nuclear-bomb-engineers-scientists.html
"Officials had initially expected that the nuclear agency’s #NationalSecurity mission would protect it from layoffs."
#ElonMusk #Musk #Doge #Trump #GOP #USPol #Politics #Security #News #USA
As Trump cuts aid, EU leaders make plans to contain ISIS-linked camps – POLITICO - EUROPE SAYS
“The EU citizens there are not necessarily people member states will be rushing to welcome back in aEUROPE SAYS (EUROPESAYS.COM)
As Trump cuts aid, EU leaders look to contain ISIS-linked camps – POLITICO
“The EU citizens there are not necessarily people member states will be rushing to welcome back in a disorganized manner,” said the first EU official. The camps, run by U.S.BYTESEU (Bytes Europe)
Geschasste Mitarbeiter sollen sich per E-Mail melden - und werden nach Rückkehr sofort freigestellt. Gerüchte über ihr Red Team dementiert die CISA.
https://www.heise.de/news/Chaos-bei-der-CISA-US-Cybersicherheitsbehoerde-holt-Gefeuerte-per-Website-zurueck-10320140.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Cybersecurity #Journal #Netzpolitik #Security #news

Chaos bei der CISA: US-Cybersicherheitsbehörde holt Gefeuerte per Website zurück
Geschasste Mitarbeiter sollen sich per E-Mail melden - und werden nach Rückkehr sofort freigestellt. Gerüchte über ihr Red Team dementiert die CISA.Dr. Christopher Kunz (heise online)
U.N. Security Council meets on humanitarian situation in Gaza U.N. Security Council meets on humanitarian situation in Gaza #UN #security #gaza from Islam Channel اهد الفيديو الخاص بهذا المقال هنا "
https://www.shibuyaworldnews.online/islamchannel-u-n-security-council-meets-on-humanitarian-situation-in-gaza/

#IslamChannel U.N. Security Council meets on humanitarian situation in Gaza - SHIBUYA World News
https://www.youtube.com/watch?v=RjPM9_Brf-A U.N. Security Council meets on humanitarian situation in Gaza U.N. Security Council meets on humanitarian situation in Gaza #UN #security #gaza from Islam Channel اهد الفيديو الخاص بهذا المقال هنا "🐈 (SHIBUYA World News)
UK rows back on claim Israel’s Gaza aid blockade is illegal – POLITICO - EUROPE SAYS
“But we find the lack of aid — it’s now been 15 days since aid got into Gaza — unacceptable,EUROPE SAYS (EUROPESAYS.COM)
Ein Cyberangriff legt die IT der städtischen Altenheime in Mönchengladbach lahm. Aerticket und die Schweizer Supermarktkette Spar bauen ihre Dienste wieder auf.
https://www.heise.de/news/Cyberangriff-auf-staedtische-Seniorenheime-in-Moenchengladbach-Aerticket-und-mehr-10318890.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Cyberangriff #Security #news
Israeli leaders call urgent meeting over fears of imminent 'Hamas ground invasion' - World News - News - EUROPE SAYS
Israel carried out airstrikes in the Gaza Strip, southern Lebanon and southern Syria on Monday, killing at leastEUROPE SAYS (EUROPESAYS.COM)
 GitHub uncovers new Ruby-SAML Vulnerabilities allowing Account Takeover Attacks.
GitHub uncovers new Ruby-SAML Vulnerabilities allowing Account Takeover Attacks.Two high-severity security flaws have been disclosed in the open-source ruby-saml library that could allow malicious actors to bypass Security Assertion Markup Language (SAML) authentication protections.
https://github.blog/security/sign-in-as-anyone-bypassing-saml-sso-authentication-with-parser-differentials/
#github #ruby #saml #library #it #security #privacy #engineer #media #programming #tech #news
Sign in as anyone: Bypassing SAML SSO authentication with parser differentials - The GitHub Blog
Critical authentication bypass vulnerabilities were discovered in ruby-saml up to version 1.17.0. See how they were uncovered.Peter Stöckli (The GitHub Blog)








![[ImageSource: LayerX Labs]
The webpage then appears to be frozen which, like most phishing attempts, adds a sense of urgency and fear that something is wrong with your computer. The window that appears displays a warning that the computer has been subjected to a trojan virus and asks the user to enter in their Mac username and password.
The warning message [captured in a screenshot by LayerX Labs], contains some glaring errors that show it’s not legitimate: It does not conform to any of Apple’s styling either in color or general appearance and misspells macOS as “MacOS.”
It also provides a phone number to contact “support,” however, when [Macworld] called this number they only got a message playback that said the recipient was not available and to call back between 8am and 5pm – even though they were calling during that time frame. The number is obviously fake and will likely never be answered.
<https://www.macworld.com/article/2642938/new-mac-phishing-attack-causes-fake-freezes-to-nab-your-apple-id-password.html> [ImageSource: LayerX Labs]
The webpage then appears to be frozen which, like most phishing attempts, adds a sense of urgency and fear that something is wrong with your computer. The window that appears displays a warning that the computer has been subjected to a trojan virus and asks the user to enter in their Mac username and password.
The warning message [captured in a screenshot by LayerX Labs], contains some glaring errors that show it’s not legitimate: It does not conform to any of Apple’s styling either in color or general appearance and misspells macOS as “MacOS.”
It also provides a phone number to contact “support,” however, when [Macworld] called this number they only got a message playback that said the recipient was not available and to call back between 8am and 5pm – even though they were calling during that time frame. The number is obviously fake and will likely never be answered.
<https://www.macworld.com/article/2642938/new-mac-phishing-attack-causes-fake-freezes-to-nab-your-apple-id-password.html>](https://friendica-leipzig.de/photo/preview/600/821761)




![The new GSMA specifications for RCS include E2EE based on the Messaging Layer Security [MLS] protocol via what's called the Rich Communication Services [RCS] Universal Profile 3.0.
"The new specifications define how to apply MLS within the context of RCS," Tom Van Pelt, technical director of GSMA, said. "These procedures ensure that messages and other content such as files remain confidential and secure as they travel between clients."
<https://www.gsma.com/newsroom/article/rcs-encryption-a-leap-towards-secure-and-interoperable-messaging/>
This also means that RCS will be the first "large-scale messaging service" to have support for interoperable E2EE between different client implementations from different providers in the near future.
The development comes nearly six months after the GSMA said it was working towards implementing end-to-end encryption [E2EE] to secure messages sent between the Android and iOS ecosystems. The move followed Apple's decision to roll out support for RCS in its own Messages app with iOS 18.
Google said, "We've always been committed to providing a secure messaging experience, and Google Messages users have had end-to-end encrypted [E2EE] RCS messaging for years. We're excited to have this updated specification from GSMA and work as quickly as possible with the mobile ecosystem to implement and extend this important user protection to cross-platform RCS messaging." The new GSMA specifications for RCS include E2EE based on the Messaging Layer Security [MLS] protocol via what's called the Rich Communication Services [RCS] Universal Profile 3.0.
"The new specifications define how to apply MLS within the context of RCS," Tom Van Pelt, technical director of GSMA, said. "These procedures ensure that messages and other content such as files remain confidential and secure as they travel between clients."
<https://www.gsma.com/newsroom/article/rcs-encryption-a-leap-towards-secure-and-interoperable-messaging/>
This also means that RCS will be the first "large-scale messaging service" to have support for interoperable E2EE between different client implementations from different providers in the near future.
The development comes nearly six months after the GSMA said it was working towards implementing end-to-end encryption [E2EE] to secure messages sent between the Android and iOS ecosystems. The move followed Apple's decision to roll out support for RCS in its own Messages app with iOS 18.
Google said, "We've always been committed to providing a secure messaging experience, and Google Messages users have had end-to-end encrypted [E2EE] RCS messaging for years. We're excited to have this updated specification from GSMA and work as quickly as possible with the mobile ecosystem to implement and extend this important user protection to cross-platform RCS messaging."](https://friendica-leipzig.de/photo/preview/600/795396)






![[ImageSource: GitHub]
"Attackers who are in possession of a single valid signature that was created with the key used to validate SAML responses or assertions of the targeted organization can use it to construct SAML assertions themselves and are in turn able to log in as any user," GitHub Security Lab researcher Peter Stöckli said in a post.
The Microsoft-owned subsidiary also noted that the issue boils down to a "disconnect" between verification of the hash and verification of the signature, opening the door to exploitation via a parser differential.
Versions 1.12.4 and 1.18.0 also plug a remote denial-of-service (DoS) flaw when handling compressed SAML responses (CVE-2025-25293, CVSS score: 7.7).
⚠️Users are recommended to update to the latest version to safeguard against potential threats.⚠️
The findings come nearly six months after GitLab and ruby-saml moved to address another critical vulnerability (CVE-2024-45409, CVSS score: 10.0) that could also result in an authentication bypass. [ImageSource: GitHub]
"Attackers who are in possession of a single valid signature that was created with the key used to validate SAML responses or assertions of the targeted organization can use it to construct SAML assertions themselves and are in turn able to log in as any user," GitHub Security Lab researcher Peter Stöckli said in a post.
The Microsoft-owned subsidiary also noted that the issue boils down to a "disconnect" between verification of the hash and verification of the signature, opening the door to exploitation via a parser differential.
Versions 1.12.4 and 1.18.0 also plug a remote denial-of-service (DoS) flaw when handling compressed SAML responses (CVE-2025-25293, CVSS score: 7.7).
⚠️Users are recommended to update to the latest version to safeguard against potential threats.⚠️
The findings come nearly six months after GitLab and ruby-saml moved to address another critical vulnerability (CVE-2024-45409, CVSS score: 10.0) that could also result in an authentication bypass.](https://friendica-leipzig.de/photo/preview/600/777841)