Suche
Beiträge, die mit Encryption getaggt sind
Because of the Signal chat leak, it’s less likely that they’ll use vulnerabilities in Signal to do that. Equally, bad actors such as drug cartels may also feel safer using Signal. Their security against the US government lies in the fact that the US government shares their vulnerabilities. No one wants their secrets exposed.
I have long advocated for a "defense dominant" cybersecurity strategy. As long as smartphones are in the pocket of every government official, police officer, judge, CEO, and nuclear power plant operator—and now that they are being used for what the White House now calls calls "sensitive," if not outright classified conversations among cabinet members—we need them to be as secure as possible. And that means no government-mandated backdoors.
We may find out more about how officials—including the vice president of the United States—came to be using Signal on what seem to be consumer-grade smartphones, in a apparent breach of the laws on government records. It’s unlikely that they really thought through the consequences of their actions.
Nonetheless, those consequences are real. Other governments, possibly including US allies, will now have much more incentive to break Signal’s security than they did in the past, and more incentive to hack US government smartphones than they did before March 24.
For just the same reason, the US government has urgent incentives to protect them."
https://www.schneier.com/blog/archives/2025/03/the-signal-chat-leak-and-the-nsa.html
#USA #CyberSecurity #Signal #Encryption #Backdoors #Privacy #NSA #StateHacking
The Signal Chat Leak and the NSA - Schneier on Security
US National Security Advisor Mike Waltz, who started the now-infamous group chat coordinating a US attack against the Yemen-based Houthis on March 15, is seemingly now suggesting that the secure messaging service Signal has security vulnerabilities.Bruce Schneier (Schneier on Security)
Now, there are a lot of ways that you can get access to somebody's phone. You can look over their shoulder while they're reading their messages, right? You can find out their password and unlock their phone, right? You can use forensic tools that police have like a Cellebrite or a break-in device to unlock phones, and then you can read the messages that way. You can also use malware. Installing malware on somebody's phone is a way that governments often gain access to people's private encrypted communications. Things like Pegasus malware or they're recently written about malware from Paragon Solutions that was going after WhatsApp messages, which was also end-to-end encrypted.
A concern about national security folks using these devices for the communications is that it makes it much more likely that their devices will get targeted by malware. And there's a lot of countries that have espionage capabilities that have the capability to target people's phones that would be very interested in knowing what Pete Hegseth is talking about, or what other high-level cabinet officials are talking about. So that makes for a very juicy intelligence target for foreign intelligence, and I think it's safe to assume that's something that many countries are now going to be going after."
https://www.techpolicy.press/about-that-signal-chat/
#USA #Trump #CyberSecurity #Signal #Encryption #CyberWarfare

About that Signal Chat
To learn more about the scandal, Justin Hendrix spoke to Just Security co-editor-in-chief Ryan Goodman and EFF senior staff technologist Cooper Quintin.Justin Hendrix (Tech Policy Press)
“These differences may be marketing gloss to Meta, but to us, they’re fundamental life or death issues that the public deserves to understand so they can make an informed choice,” Whittaker concludes.
On Sunday, WhatsApp sent a message to Dutch users stating that the company can’t read their messages, including text and voice messages, photos, videos, and calls.
“They are protected by end-to-end encryption because we are always committed to protecting your privacy,” the note reads."
https://cybernews.com/news/whatsapp-signal-executives-battle/
#Cybersecurity #Privacy #Encryption #Signal #WhatsApp
There’s also a contradiction at play. If politicians dream of making the UK a technology hub they should not be working to undermine the foundations of cyber security, on which a workable tech industry relies.
The government should withdraw its misguided mandate. Instead of surreptitiously cutting the brake cables on the technological car, it should be working to strengthen security and privacy of the technology that forms the nervous system of our world. Business leaders must also take a role, making it clear that these dangerous moves are unacceptable, and pushing the companies they license technology from to deploy encryption, and other protections, without which their interests and those of their customers will be vulnerable.
We have ceded so many of the core operations of our lives and institutions to tech, we must recognise that strong encryption isn’t the enemy of security — it is security. The argument that weakening encryption will make any of us safer is as wrong as it is dangerous."
https://www.ft.com/content/a934150f-e0f5-4e75-a2d1-a3671ea52ca0
#UK #CyberSecurity #Encryption #Backdoors #Privacy #Apple
The war on encryption is dangerous
Government demands to access encrypted data via back doors will leave it vulnerable to hacks, breaches and theftMeredith Whittaker (Financial Times)
Teilen erbeten ‼️

#DSGVO #TDDDG ( #unplugtrump )
#Datenschutz #Privatsphäre #sicherheit #Verschlüsselung
#encryption #WEtell #SoloKey #NitroKey #Email #Cybersecurity #Pixelfed #Massenűberwachung
#Google #Metadaten #WhatsApp #Threema #Cryptpad #Signal
#Hateaid #Cyberstalking #Messenger #Browser #Youtube #NewPipe #Chatkontrolle #nichtszuverbergen #ÜberwachungsKapitalismus #Microsoft #Apple #Windows #Linux #Matrix #Mastodon #Friendica #Fediverse #Mastodir #Loops #2FA #Ransomware #Foss #VeraCrypt #HateAid #Coreboot #Volksverpetzer #Netzpolitik #Digitalisierung #FragdenStaat #Shiftphone #OpenSource #GrapheneOS #CCC #Mail #Mullvad #PGP #GnuPG #DNS #Gaming #linuxgaming #Lutris #Protondb #eOS #Enshittification
#Bloatware #TPM #Murena #LiberaPay #GnuTaler #Taler #PreppingforFuture
#FediLZ #BlueLZ #InstaLZ #ThreatModel
#FLOSS #UEFI #Medienkompetenz
https://cryptpad.digitalcourage.de/file/#/2/file/C3-dKGz23Qhw1ZSBmDnOAK3s/
ORG, Big Brother Watch and Index on Censorship call for the Tribunal into the UK government's secret order for Apple to break encryption to be held in public.
The case happens TOMORROW.
Read more ⬇️
https://techcrunch.com/2025/03/13/apples-appeal-against-uks-secret-icloud-backdoor-order-must-be-held-in-public-rights-groups-urge/
#encryption #e2ee #privacy #security #ukpolitics #ukpol #cybersecurity #apple

Apple’s appeal against UK’s secret iCloud backdoor order must be held in public, rights groups urge | TechCrunch
Privacy rights groups have called on Apple's legal challenge to a secret U.K. government order asking it to backdoor an end-to-end encrypted (E2EE)Natasha Lomas (TechCrunch)
The change was spotted by security expert Alec Muffett, who wrote in a blog post on Wednesday that the U.K.’s National Cyber Security Centre (NCSC) is no longer recommending that high-risk individuals use encryption to protect their sensitive information.
The NCSC in October published a document titled “Cybersecurity tips for barristers, solicitors & legal professionals,” that advised the use of encryption tools such as Apple’s Advanced Data Protection (ADP).
ADP allows users to turn on end-to-end encryption for their iCloud backups, effectively making it impossible for anyone, including Apple and government authorities, to view data stored on iCloud."
https://techcrunch.com/2025/03/06/uk-quietly-scrubs-encryption-advice-from-government-websites/
#UK #CyberSecurity #Encryption #Surveillance #Apple #iCloud

UK quietly scrubs encryption advice from government websites | TechCrunch
The UK is no longer recommending the use of encryption for at-risk groups following its iCloud backdoor demandsCarly Page (TechCrunch)
You can’t scan communications without breaching privacy.
You can’t introduce message scanning software that undermines encryption in a way that’s anything other than less secure than what we have now.
Find out more ➡️ https://www.openrightsgroup.org/press-releases/practice-safe-text-campaign-launched/
#e2ee #encryption #privacy #cybersecurity #security
Practice Safe Text Campaign launched
Open Rights Group has launched a new campaign, ‘Practice Safe Text’ which highlights the importance of end-to-end encryption in keeping our communications safe.Open Rights Group
"If they're going to cave into Zuck's demand to facilitate spying on Instagram users, do we really think they'll resist Kier Starmer's demands to remove Signal – and any other app that stands up to the Snooper's Charter – from the App Store?
It goes without saying that the "bad guys" the UK government claims it wants to target will be able to communicate in secret no matter what Apple does here. They can just use an Android phone and sideload a secure messaging app, or register an iPhone in Ireland or any other country and bring it to the UK. The only people who will be harmed by the combination of the British government's reckless disregard for security, and Apple's designs that trade the security of its users for the security of its shareholders are millions of law-abiding Britons, whose most sensitive data will be up for grabs by anyone who hacks their accounts."
https://pluralistic.net/2025/02/25/sneak-and-peek/
#CyberSecurity #UK #Apple #Encryption #Backdoors #Privacy #Totalitarianism #iCloud
The U.K. news cannot be seen in isolation and follows years of battling between big tech and governments over warranted, legal access to encrypted messages and content to fuel investigations into serious crimes such as terrorism and child abuse.
As I reported in 2020, “it is looking ever more likely that proponents of end-to-end security, the likes of Facebook and Apple, will lose their campaign to maintain user security as a priority.” It has taken five years, but here we now are.
The last few weeks may have seemed to signal a unique fork in the road between the U.S. and its primary Five Eyes ally, the U.K. But it isn’t. In December, the FBI and CISA warned Americans to stop sending texts and use encrypted platforms instead. And now the U.K. has forced open iCloud to by threatening to mandate a backdoor. But the devil’s in the detail — and we’re fast approaching a dangerous pivot."
https://www.forbes.com/sites/zakdoffman/2025/02/24/fbis-new-iphone-android-security-warning-is-now-critical/
#USA #FBI #CyberSecurity #Encryption #Privacy #UK #CISA #Apple #Backdoor

FBI Warns iPhone, Android Users—We Want ‘Lawful Access’ To All Your Encrypted Data
UK forces Apple to provide encrypted data to security agencies—is America next?Forbes
Apple had previously allowed end-to-end encryption of data on UK devices through its Advanced Data Protection (ADP) tool, but that ended Friday, a spokesperson said in a lengthy statement.
"Apple can no longer offer Advanced Data Protection (ADP) in the United Kingdom to new users and current UK users will eventually need to disable this security feature," Apple said."
https://arstechnica.com/tech-policy/2025/02/apple-pulls-data-protection-tool-instead-of-caving-to-uk-demand-for-a-backdoor/
#UK #CyberSecurity #Apple #Encryption #Backdoors #DataProtection #Surveillance

Apple pulls end-to-end encryption in UK, spurning backdoors for gov’t spying
Apple abruptly yanks privacy tool in UK, taking bold stance against snooping law.Ashley Belanger (Ars Technica)

Apple pulls data protection tool after UK government security row
Customers' photos and documents stored online will no longer be protected by end to end encryption.Zoe Kleinman (BBC News)
The secret order, first reported by The Washington Post, was issued in January under the auspices of the UK’s Investigatory Powers Act of 2016. Apple’s compliance or refusal will have ramifications far beyond the UK, potentially making users less safe and signaling to other governments that they, too, can seek backdoor access — a way of bypassing encryption — to users’ information via legislation.
“Simply put, the message the UK government is sending is that its own citizens cannot expect its government to respect their privacy, and that it is willing to put their security at risk from all manner of bad actors like hackers and thieves because it cannot tolerate the ability to have a private conversation online,” Andrew Crocker, surveillance litigation director at the Electronic Frontier Foundation, told The Verge."
https://www.theverge.com/policy/612136/uk-icloud-investigatory-powers-act-war-on-encryption
#UK #CyberSecurity #Privacy #Encryption #Apple #iCloud

The UK’s war on encryption affects all of us
The UK is using its Investigatory Powers Act to demand backdoor access to iCloud users’ encrypted backups worldwide.Gaby Del Valle (The Verge)
https://www.kuketz-blog.de/verschluesselung-der-nextcloud-eine-grundlegende-entscheidung-nextcloud-teil-2/
#nextcloud #encryption #e2ee #cryptomator #security #sicherheit

Verschlüsselung der Nextcloud: Eine grundlegende Entscheidung – Nextcloud Teil 2
Verschlüsselung in Nextcloud: Serverseitig, mit Benutzer-Schlüssel oder Ende-zu-Ende? Wir erklären die Unterschiede und helfen bei der richtigen Wahl.www.kuketz-blog.de
Verschlüsselung in Nextcloud: Serverseitig, mit Benutzer-Schlüssel, Ende-zu-Ende oder Drittanbieter-Lösung? Wir erklären die Unterschiede und helfen bei der richtigen Wahl. 👇
https://www.kuketz-blog.de/verschluesselung-der-nextcloud-eine-grundlegende-entscheidung-nextcloud-teil-2/
#nextcloud #encryption #e2ee #cryptomator #security #sicherheit

Verschlüsselung der Nextcloud: Eine grundlegende Entscheidung – Nextcloud Teil 2
Verschlüsselung in Nextcloud: Serverseitig, mit Benutzer-Schlüssel oder Ende-zu-Ende? Wir erklären die Unterschiede und helfen bei der richtigen Wahl.www.kuketz-blog.de
Verschlüsselung in Nextcloud: Serverseitig, mit Benutzer-Schlüssel, Ende-zu-Ende oder Drittanbieter-Lösung? Wir erklären die Unterschiede und helfen bei der richtigen Wahl. 👇
https://www.kuketz-blog.de/verschluesselung-der-nextcloud-eine-grundlegende-entscheidung-nextcloud-teil-2/
#nextcloud #encryption #e2ee #cryptomator #security #sicherheit

Verschlüsselung der Nextcloud: Eine grundlegende Entscheidung – Nextcloud Teil 2
Verschlüsselung in Nextcloud: Serverseitig, mit Benutzer-Schlüssel oder Ende-zu-Ende? Wir erklären die Unterschiede und helfen bei der richtigen Wahl.www.kuketz-blog.de
As reported, the British government’s undisclosed order was issued last month, and requires the capability to view all encrypted material in iCloud. The core target is Apple’s Advanced Data Protection, which is an optional feature that turns on end-to-end encryption for backups and other data stored in iCloud, making it so that even Apple cannot access that information. For a long time, iCloud backups were a loophole for law enforcement to gain access to data otherwise not available to them on iPhones with device encryption enabled. That loophole still exists for anyone who doesn’t opt in to using Advanced Data Protection. If Apple does comply, users should consider disabling iCloud backups entirely. Perhaps most concerning, the U.K. is apparently seeking a backdoor into users’ data regardless of where they are or what citizenship they have."
https://www.eff.org/deeplinks/2025/02/uks-demands-apple-break-encryption-emergency-us-all
#CyberSecurity #UK #Privacy #Encryption #Apple #iCloud
Back doors are not a good idea. And this comes on top of Starmer's proposals to open up all of our bank accounts to public examination
http://archive.today/2025.02.07-202742/https://www.thetimes.com/uk/politics/article/home-office-orders-apple-to-let-it-snoop-on-encrypted-files-rb8grfzh8 (archived)
https://bigbrotherwatch.org.uk/press-releases/big-brother-watch-response-to-the-government-ordering-apple-to-let-them-spy-on-users-messages/
https://bigbrotherwatch.org.uk/bankspying/big-issue-the-governments-mass-bank-spying-proposals-is-an-assault-on-welfare/
#Encryption #BigBrotherWatch #BigBotherWatch #Privacy #IT
So far we have seen strides for at least keeping messages private on mobile devices with end-to-end encrypted apps like Signal, WhatsApp, and iMessage. Encryption on the web has been widely adopted. We even declared in 2021 that “HTTPS Is Actually Everywhere.” Most web traffic is encrypted and for a website to have a reputable presence with browsers, they have to meet certain requirements that major browsers enforce today. Mechanisms like certificate transparency, Cross-origin resource sharing (CORS) rules, and enforcing HTTPS help prevent malicious activity happening to users every day.
Yet, mobile has always been a different and ever expanding context. You access the internet on mobile devices through more than just the web browser. Mobile applications have more room to spawn network requests in the app without the user ever knowing where and when a request was sent. There is no “URL bar” to see the network request URL for the user to see and check. In some cases, apps have been known to “roll their own” cryptographic processes outside of non-standard encryption practices."
https://www.eff.org/deeplinks/2025/02/closing-gap-encryption-mobile
#CyberSecurity #Encryption #Mobile #Cellphones #VPNs #Privacy
Closing the Gap in Encryption on Mobile
It’s time to expand encryption on Android and iPhone. With governments around the world engaging in constant attacks on user’s digital rights and access to the internet, removing glaring and potentially dangerous targets off of people’s backs when th…Electronic Frontier Foundation
How do you organise this communication in a way so that no-one - including police - can steal it?
Are you using encrypted computers and #email or #messengers with #e2e #encryption? - If so, what messengers or method are you using?
Are you storing documents in a safe? If so, where and what brand?
What is feasible, what is practical?
#privacy #therapy #data_protection #encryption
Please read up on whether your messaging system is *end-to-end* encrypted, not just “encrypted”, and think about whether you trust the developers to write good code and not lie to you about how things work.
Mastodon DMs are *not* end-to-end encrypted! You should not write anything on Mastodon that you don’t want published in the open (given sufficient incentive).
Some systems *can* be end-to-end encrypted but are not by default. RCS, FB Messenger, and Instagram DMs fall into this category AFAICT. Some systems don’t even offer it, like Discord.
Please consider moving your private messages to a system that is private by design! I’m partial to Signal, but feel free to choose your own.
#privacy #encryption
Wie bekommt man die "per-user keys" aktiviert? Die Doku erklärt das nicht wirklich.
https://nextcloud.com/de/blog/encryption-in-nextcloud/
#nextcloud #encryption
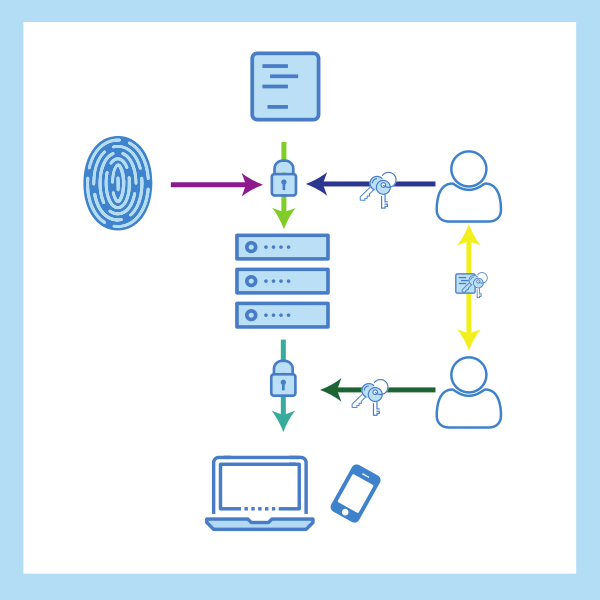
Data encryption methods in Nextcloud - Nextcloud
Exploring different kinds of encryption in Nextcloud to aid system administrators and taking the appropriate security measures.Jos Poortvliet (Nextcloud)
https://kopia.io/
#backup #linux #macos #windows #sicherheit #datenschutz #encryption
From my own perspective, computing privacy is simple: if something happens entirely on my computer, then it's private, whereas if my computer sends data to the manufacturer of the computer, then it's not private, or at least not entirely private. Thus, the only way to guarantee computing privacy is to not send data off the device.
I don't understand most of the technical details of Apple's blog post. I have no way to personally evaluate the soundness of Apple's implementation of Enhanced Visual Search. One thing I do know, however, is that Apple computers are constantly full of privacy and security vulnerabilities, as proved by Apple's own security release notes. You don't even have to hypothesize lies, conspiracies, or malicious intentions on the part of Apple to be suspicious of their privacy claims. A software bug would be sufficient to make users vulnerable, and Apple can't guarantee that their software includes no bugs. (To the contrary, Apple's QA nowadays is atrocious.)
It ought to be up to the individual user to decide their own tolerance for the risk of privacy violations. In this specific case, I have no tolerance for risk, because I simply have no interest in the Enhanced Visual Search feature, even if it happened to work flawlessly. There's no benefit to outweigh the risk. By enabling the "feature" without asking, Apple disrespects users and their preferences. I never wanted my iPhone to phone home to Apple.
Remember this advertisement? "What happens on your iPhone, stays on your iPhone.""
https://lapcatsoftware.com/articles/2024/12/3.html
#Apple #ApplePhotos #Privacy #DataProtection #Encryption #iOS #iPhone

“If we want our data to remain confidential, we have to act now”: Quantum computing can crack all our encryption, and that is everyone’s problem
Quantum computing's ability to crack encryption will cause a world of issuesBenedict Collins (TechRadar pro)
https://theyseeyourphotos.com/
#TheySeeYourPhotos #cloud #surveillance #photos #media #ai #privacy #ente #enteio #e2e #e2ee #encryption
Email services such as Gmail and Outlook generally offer encryption in transit, which means they can be read on the companies’ servers and by the end users. Messages that are encrypted in transit can’t be nabbed from a telecom network in an accessible format, but they could be accessed through an email service provider or a law enforcement request to that company.
End-to-end encryption—the kind offered by services like WhatsApp and Signal—is considered the best bet for privacy, particularly when paired with the option to auto-delete messages after a set period of time, says Mullin."
https://www.inc.com/jennifer-conrad/why-you-should-start-using-encrypted-communications-today/91034632
#CyberSecurity #Privacy #Encryption #E2EEncryption #Signal

European Court of Human Rights Confirms: Weakening Encryption Violates Fundamental Rights
In a milestone judgment—Podchasov v. Russia—the European Court of Human Rights (ECtHR) has ruled that weakening of encryption can lead to general and indiscriminate surveillance of the communications of all users and violates the human right to priva…Electronic Frontier Foundation
I will resist and it's my human right.
Encryption is not for bad actors only, it protects innocent people every day.
We are not criminals.
#privacy #encryption