Suche
Beiträge, die mit PRIVACY getaggt sind
https://aliyesha.com/sub/articles/news/display/bh_notre_dame_celebrates_alumni_meet_2024
#bihar #patna #india #news #press #education #school #alumni #alumnimeet #notredame #BackToSchool #NotreDameAcademy
Enjoy tracker free reading with us. #privacy #privacymatters

Patna: Nostalgia Revisited at Notre Dame Academy Alumni Meet 2024.
The Notre Dame Academy Alumni Association, Patna, brought old friends, former students, teachers, and staff together for a heartwarming reunion.Alok Sharma (Aliyesha)
#privacy #GDPR
https://www.dataprotection.ie/en/news-media/press-releases/irish-data-protection-commission-fines-meta-eu251-million

Data Protection Commission
The Irish Data Protection Commission (DPC) has today announced its final decisions following two inquiries into Meta Platforms Ireland Limited (‘MPIL’).Data Protection Commission

IT-security researchers have uncovered a new Linux rootkit called PUMAKIT that comes with capabilities to escalate privileges, hide files & directories, and conceal itself from system tools, while simultaneously evading detection.
https://www.elastic.co/security-labs/declawing-pumakit
#linux #pumakit #malware #it #security #privacy #engineer #media #tech #news
Declawing PUMAKIT — Elastic Security Labs
PUMAKIT is a sophisticated loadable kernel module (LKM) rootkit that employs advanced stealth mechanisms to hide its presence and maintain communication with command-and-control servers.www.elastic.co
The more you use it, the better protected are people in repressive countries who want to use a free internet, journalists and researchers who want to protect themselves from discovery, whistleblowers, activists, and ordinary people who want to opt out of invasive third party tracking.
Desktop and mobile: https://www.torproject.org/en/download
#web #privacy #tracking #journalism

The Tor Project | Privacy & Freedom Online
Defend yourself against tracking and surveillance. Circumvent censorship.www.torproject.org
https://techcrunch.com/2024/12/15/serbian-police-used-cellebrite-to-unlock-then-plant-spyware-on-a-journalists-phone/
#Serbia #privacy #cybersecurity #journalism

Serbian police used Cellebrite to unlock, then plant spyware on, a journalist's phone | TechCrunch
Amnesty said it found NoviSpy, an Android spyware linked to Serbian intelligence, on the phones of several members of Serbian civil society following police stops.Lorenzo Franceschi-Bicchierai (TechCrunch)

Privacy camp in 2025 - European Digital Rights (EDRi)
This change allows for a more impactful event in light of significant political shifts in Europe in 2024, like Members of the European Parliament and College of Commissioners.European Digital Rights (EDRi)
https://aliyesha.com/sub/articles/news/display/bh_launch_siddheshwar_ki_ghazlein_book_fair
#bihar #patna #india #news #press #book #books #bookfair #ghazal #literature #culture #SiddheshwarKiGhazlein
Enjoy tracker free reading with us. #privacy #privacymatters

Patna: Launch of 'Siddheshwar ki Ghazlein' at Patna Book Fair.
Under the aegis of Vishal Publications and Chhand:Shaala, the poetry collection Siddheshwar ki Ghazlein, was launched.Alok Sharma (Aliyesha)
The Federal Office for Information Security (BSI) announced that it had blocked communication between the infected Android IoT devices and the criminal’s command-and-control (C2) servers, to preventing further damage.
https://www.bsi.bund.de/DE/Service-Navi/Presse/Pressemitteilungen/Presse2024/241212_Badbox_Sinkholing.html
#android #badbox #bsi #it #security #privacy #engineer #media #tech #news
https://aliyesha.com/sub/articles/news/display/uk_former_cm_rawat_on_vijay_diwas
#uttarakhand #dehradun #india #news #press #indianarmy #vijaydiwas #bangladesh #pakistan #EastPakistan #indiragandhi
Enjoy tracker free reading with us. #privacy #privacymatters

Dehradun: Former Chief Minister Harish Rawat Salutes the Military’s Glory on the 1971 Vijay Diwas.
A commemorative event was held at Deen Dayal Park, Sadak Sansad, to mark Vijay Diwas. Former Chief Minister Harish Rawat paid homage to the martyrs and expressed his heartfelt sentiments.Prem Pancholi (Aliyesha)
💡 Try My Idea: USBSTICK "Pull The Plug" Bracelet (ideal for Tails)
This idea allows you to attach yourself to the inserted Tails disk, by bracelet (on demand)
If your arm ever gets too far from the computer: *POOF* there goes forensics! 😁
#HumanRights #Journalism #Tails #Linux #privacy #forensics #ideas #tech #GNU #fun #bracelet #jewelry #RAM #coldbootattack #infosec #cybersecurity #TorProject
https://tube.tchncs.de/w/q2Vdv11aTrmgAjKrrAULw2

Tails Amnesiac "Pull The Plug" Coldboot Protection Bracelet
Today sharing my new tails on bracelet concept / idea with everyone - Tails on bracelet I call the "RightToPrivacy Pull The Plug Tails Bracelet". My idea for wearing Tails usbstick detachable brace...tchncs
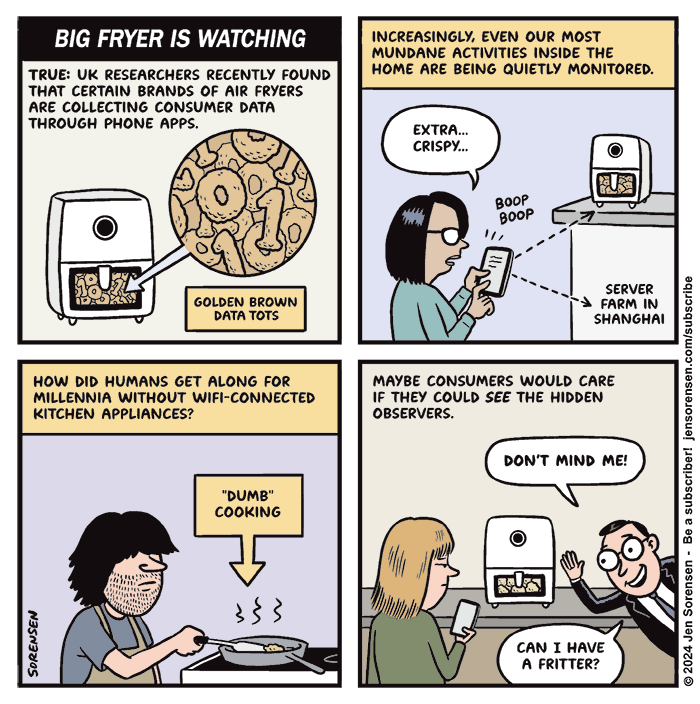
#comic #cartoon #technology #tech #privacy #surveillance #consumer #cooking #internet #internetofthings

Loose ends - net.wars
Privacy technologies typically fail for one of two reasons: 1) they're too complicated and/or expensive to find widespread adoption among users; 2) sites and seWendy M. Grossman (net.wars)
Tracking me without my consent. 🤔
That'll be a no then. #Ethics and meeting legal obligations are important to me, a simple test for deserving support, especially in #journalism.
They're still embedding Tweets as well. 🤦♂️
#privacy
https://aliyesha.com/sub/articles/news/display/uk_ayurveda_can_strengthen_global_health_care
#uttarakhand #dehradun #india #news #press #Ayurveda #GlobalHealthcare #TraditionalMedicine #NaturalHealing #10thWorldAyurvedaCongress #ArogyaExpo2024 #PMModi #CMDhami #AyurvedaForTheWorld
Enjoy tracker free reading with us. #privacy #privacymatters

Dehradun: Ayurveda Can Strengthen Global Healthcare Systems: PM Modi.
The 10th World Ayurveda Congress (WAC) and Arogya Expo 2024 commenced today in Dehradun.Prem Pancholi (Aliyesha)
https://aliyesha.com/sub/articles/news/display/bh_promoting_entrepreneurship_self_employment
#bihar #patna #india #news #press #government #governance #Entrepreneurship #SelfEmployment #EconomicGrowth #SkillDevelopment #Startups #business
Enjoy tracker free reading with us. #privacy #privacymatters

Patna: Promoting Entrepreneurship and Self-Employment: Bihar Government Hosts Fund Distribution Event.
To foster entrepreneurship, support self-employment, and elevate the economic status of educated unemployed youth, Government of Bihar, organised a fund distribution event today.Alok Sharma (Aliyesha)
Microsoft resolved 72 vulnerabilities in a variety of its products, including a zero-day [CVE-2024-49138 (CVSS score: 7.8)] that’s been exploited by attackers in the wild to execute code with higher privileges, and 16 critical vulnerabilities (all of which are remote code execution flaws).
https://msrc.microsoft.com/update-guide/releaseNote/2024-Dec
#microsoft #windows #update #it #security #privacy #engineer #media #tech #news
https://aliyesha.com/sub/articles/news/display/nd_liquor_guidelines_xmas_new_year_2024
#newdelhi #delhi #india #press #news #government #governance #liquor #sharab #party #christmas #xmas #newyear #guidelines
Enjoy tracker free reading with us. #privacy #privacymatters

नई दिल्ली: क्रिसमस और न्यू ईयर से पहले दिल्ली के युवाओं पर पाबंदी, शराब पीने की गाइडलाइंस में सख्ती।
क्रिसमस और नए साल के जश्न से पहले दिल्ली में शराब का सेवन करने वाले युवाओं के लिए मुश्किल हो सकती है।दिल्ली ब्यूरो (Aliyesha)
EFF Launches Digital Rights Bytes to Answer Tech Questions that Bug Us All

Yes, politicians and Big Corporates do twist narratives to suite their own agendas. EFF is aiming to try to give more objective and honest answers to technology questions, especially those which affect users’ privacy and security.
EFF is the leading nonprofit defending civil liberties in the digital world. Founded in 1990, EFF champions user privacy, free expression, and innovation through impact litigation, policy analysis, grassroots activism, and technology Development. Its mission is to ensure that technology supports freedom, justice and innovation for all people of the world.
An interesting twist is that you can submit your own questions and answers too (without providing your name, e-mail address, or a completed reCaptcha).
See https://www.eff.org/press/releases/eff-launches-digital-rights-bytes-answer-tech-questions-bug-us-all
#Blog, #EFF, #privacy, #security, #technology
https://aliyesha.com/sub/articles/news/display/hp_nift_15_percent_seat_reserved_himachali
#himachal #dharamshala #india #press #news #education #EntranceExam #college #NIFT #fashion #textile #FashionTechnology
Enjoy tracker free reading with us. #privacy #privacymatters

Dharamshala: 15% seats reserved for Himachali candidates at NIFT: Chandra.
NIFT application deadline January 6 2025; Entrance Exam on February 9 2025.Rajesh (Aliyesha)
https://aliyesha.com/sub/articles/news/display/bh_cm_nitish_kumar_inaugrates_collectorate_building
#bihar #patna #india #news #press #politics #jdu #nitishkumar #government #governance #infrastructure #mahatmagandhi
Enjoy tracker free reading with us. #privacy #privacymatters

Patna: Chief Minister Nitish Kumar inaugurates new Patna Collectorate Building.
Chief Minister Nitish Kumar inaugurated the newly constructed Patna Collectorate building by unveiling a stone plaque and cutting a ribbon.Alok Sharma (Aliyesha)
https://aliyesha.com/sub/articles/news/display/nd_illegal_bangladeshi_migrant_issue_boiling
#newdelhi #delhi #india #press #news #bangladesh #HinduMinority #IllegalMigrants #elections2025
Enjoy tracker free reading with us. #privacy #privacymatters

नई दिल्ली: दिल्ली चुनाव से पहले राजधानी में उठा बांग्लादेशी घुसपैठियों का मुद्दा, एलजी ने दिया सख्त कार्रवाई का आदेश।
दिल्ली में विधानसभा चुनाव से पहले राजनीतिक माहौल लगातार गरमा रहा है।दिल्ली ब्यूरो (Aliyesha)
Amazon reveals UK’s most asked Alexa questions of 2024.
#surveillance #privacy
https://www.theguardian.com/technology/2024/dec/10/amazon-reveals-uk-most-asked-alexa-questions-of-2024
https://aliyesha.com/sub/articles/news/display/pb_celebrating_success_14th_national_crafts_fair
#chandigarh #india #news #press #crafts #arts #ChandigarhNationalCraftsFair #success #thanks #kalagram
Enjoy tracker free reading with us. #privacy #privacymatters

Chandigarh: Celebrating the Success of the 14th Chandigarh National Crafts Fair.
The recently concluded 14th Chandigarh National Crafts Fair has been hailed as a roaring success.Dr. Kharbanda (Aliyesha)
[Journalists, human rights defenders, lawmakers and political officials are frequent targets of state surveillance.]
The mobile device security firm iVerify has been offering a tool that makes spyware scanning accessible to anyone.
http://iverify.io/blog/iverify-mobile-threat-investigation-uncovers-new-pegasus-samples
#android #iphone #spyware #scanner #pegasus #it #security #privacy #engineer #media #tech #news
iVerify Mobile Threat Investigation Uncovers New Pegasus Samples
iVerify’s Mobile Threat Hunting finds Pegasus spyware is more prevalent and capable of infecting a wide range of devices, not just devices of high-risk users.iverify.io
https://aliyesha.com/sub/articles/news/display/hp_state_government_unfulfilled_promises_bane
#himachal #dharamshala #india #press #news #governance #government #mismanagement #allegation #congress #SukhvinderSukhu #CmSukhu #employees #retired
Enjoy tracker free reading with us. #privacy #privacymatters

Dharamshala: State Government’s previous budget announcements for Employees and Pensioners unfulfilled: Ghanshyam Sharma.
With the new financial year’s budget preparation set to commence in two months, the promises made in the previous budget remain unfulfilled.Rajesh (Aliyesha)
A: The police.
#surveillance #privacy
https://www.theguardian.com/uk-news/2024/dec/08/police-unlawfully-storing-images-of-innocent-people-for-facial-recognition
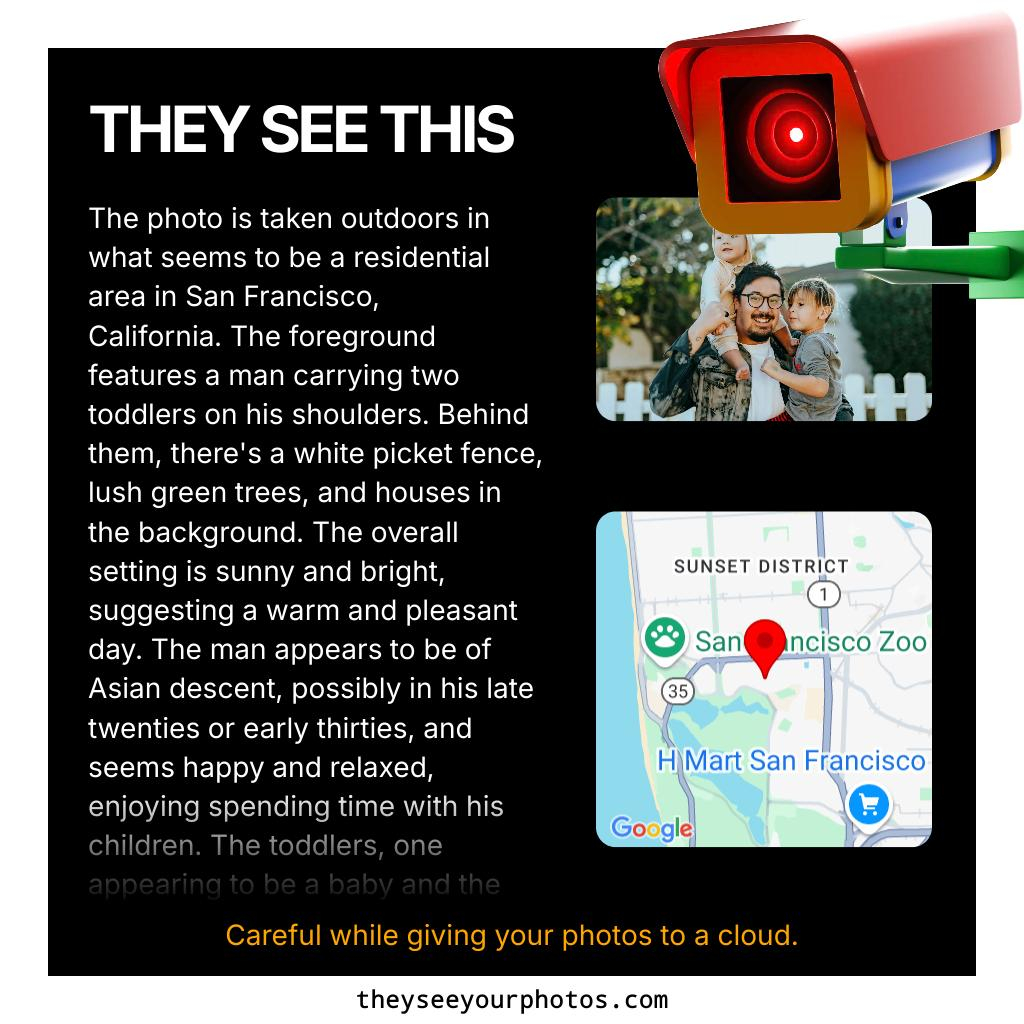
https://theyseeyourphotos.com/
#TheySeeYourPhotos #cloud #surveillance #photos #media #ai #privacy #ente #enteio #e2e #e2ee #encryption
"The notorious spyware from Israel's NSO Group has been found targeting journalists, government officials, and corporate executives in multiple variants discovered in a threat scan of 2,500 mobile phones": Pegasus Spyware Infections Proliferate Across iOS, Android Devices https://www.itprotoday.com/endpoint-security/pegasus-spyware-infections-proliferate-across-ios-android-devices https://mastodon.opencloud.lu/@BrideOfLinux/113613943709410562

Pegasus Spyware Infections Proliferate Across iOS, Android Devices
The notorious spyware from Israel's NSO Group has been found targeting journalists, government officials, and corporate executives in multiple variants discovered in a threat scan of 2,500 mobile phones.Elizabeth Montalbano (www.itprotoday.com)
https://www.wired.com/story/politics-lab-keeping-your-personal-data-safe/
#USA #Trump #DataProtection #Privacy #Surveillance #PoliceState
Email services such as Gmail and Outlook generally offer encryption in transit, which means they can be read on the companies’ servers and by the end users. Messages that are encrypted in transit can’t be nabbed from a telecom network in an accessible format, but they could be accessed through an email service provider or a law enforcement request to that company.
End-to-end encryption—the kind offered by services like WhatsApp and Signal—is considered the best bet for privacy, particularly when paired with the option to auto-delete messages after a set period of time, says Mullin."
https://www.inc.com/jennifer-conrad/why-you-should-start-using-encrypted-communications-today/91034632
#CyberSecurity #Privacy #Encryption #E2EEncryption #Signal
https://aliyesha.com/sub/articles/news/display/uk_government_strengthening_air_services
#uttarakhand #dehradun #india #press #news #government #governance #bjp #heliport #helipads #helicopter #AirWays #EmergencyServices
Enjoy tracker free reading with us. #privacy #privacymatters

Dehradun: Uttarakhand Government strengthening air services for remote areas.
The Uttarakhand government is enhancing air services to improve accessibility to remote areas.Prem Pancholi (Aliyesha)
https://aliyesha.com/sub/articles/news/display/uk_garhwali_fil_danu_bhula_captivates_audience
#uttarakhand #dehradun #india #press #news #cinema #movies #films #garhwali #DanuBhula #RegionalFIlm
Enjoy tracker free reading with us. #privacy #privacymatters

Dehradun: Garhwali Film "Danu Bhula": A tale exploring migration, unemployment, and cultural values.
With the introduction of Uttarakhand’s film policy, the landscape of local cinema has undergone significant change.Prem Pancholi (Aliyesha)
https://aliyesha.com/sub/articles/news/display/nd_metro_blue_line_disruption
#newdelhi #delhi #india #press #news #metro #trains #disruption #CableStealing #menace #DelhiMetro
Enjoy tracker free reading with us. #privacy #privacymatters

नई दिल्ली: दिल्ली मेट्रो पर केबल चोरी: लगातार घटनाएं बनीं बड़ी समस्या।
दिल्ली मेट्रो की ब्लू लाइन (द्वारका सेक्टर 21 - नोएडा इलेक्ट्रॉनिक सिटी/वैशाली) पर अपरहेड वायर और केबल चोरी की घटनाएं थमने का नाम नहीं ले रही हैं।दिल्ली ब्यूरो (Aliyesha)
Venntel, through its parent company Gravy Analytics, takes location data from smartphones, either through ordinary apps installed on them or through the advertising ecosystem, and then provides that data feed to other companies who sell location tracking technology to the government or sells the data directly itself. Venntel is the company that provides the underlying data for a variety of other government contractors and surveillance tools, including Locate X. 404 Media and a group of other journalists recently revealed Locate X could be used to pinpoint phones that visited abortion clinics.
The FTC says in a proposed order that Gravy and Venntel will be banned from selling, disclosing, or using sensitive location data, except in “limited circumstances” involving national security or law enforcement."
#USA #FTC #LocationData #Venntel #Gravy #DataBrokers #DataBrokerage #DataProtection #Privacy #Surveillance
https://www.404media.co/ftc-bans-location-data-company-that-powers-the-surveillance-ecosystem/

FTC Bans Location Data Company That Powers the Surveillance Ecosystem
Venntel is a primary provider of location data to the government or other companies that sell to U.S. agencies. The FTC is banning Venntel from selling data related to health clinics, refugee shelters, and much more.Joseph Cox (404 Media)
They bought logs of people's whereabouts from app developers and other companies that carried out software-based tracking of location, and then resold it.
And thisis one reason why you should not grants your apps blanket access to all of your data on your phone and if you do provided limited access, be aware of where you are using them and when.
https://www.theregister.com/2024/12/04/ftc_data_brokers/
#Privacy #Security #DataForSale #Apps #Mobile


![[ImageSource: Elastic Security]
Pumakit Infection Chain.
Pumakit employs a multi-stage infection process starting with a dropper named 'cron,' which executes embedded payloads ('/memfd:tgt' and '/memfd:wpn') entirely from memory.
The '/memfd:wpn' payload, which executes in a child process, performs environment checks and kernel image manipulation and eventually deploys the LKM rootkit module ('puma.ko') into the system kernel.
Embedded within the LKM rootkit is Kitsune SO ('lib64/libs.so'), acting as the userland rootkit that injects itself into processes using 'LD_PRELOAD' to intercept system calls at the user level. [ImageSource: Elastic Security]
Pumakit Infection Chain.
Pumakit employs a multi-stage infection process starting with a dropper named 'cron,' which executes embedded payloads ('/memfd:tgt' and '/memfd:wpn') entirely from memory.
The '/memfd:wpn' payload, which executes in a child process, performs environment checks and kernel image manipulation and eventually deploys the LKM rootkit module ('puma.ko') into the system kernel.
Embedded within the LKM rootkit is Kitsune SO ('lib64/libs.so'), acting as the userland rootkit that injects itself into processes using 'LD_PRELOAD' to intercept system calls at the user level.](https://friendica-leipzig.de/photo/preview/600/367019)
![[ImageSource: Elastic Security]
Pumakit using ftrace to hook Syscalls.
The malware uses the internal Linux function tracer (ftrace) to hook into as many as 18 different system calls and various kernel functions such as "prepare_creds," and "commit_creds" to alter core system behaviors and accomplish its goals.
<https://www.kernel.org/doc/html/latest/trace/ftrace.html>
"Unique methods are used to interact with Pumakid, including using the rmdir() syscall for privilege escalation and specialized commands for extracting configuration and runtime information," the researchers said. [ImageSource: Elastic Security]
Pumakit using ftrace to hook Syscalls.
The malware uses the internal Linux function tracer (ftrace) to hook into as many as 18 different system calls and various kernel functions such as "prepare_creds," and "commit_creds" to alter core system behaviors and accomplish its goals.
<https://www.kernel.org/doc/html/latest/trace/ftrace.html>
"Unique methods are used to interact with Pumakid, including using the rmdir() syscall for privilege escalation and specialized commands for extracting configuration and runtime information," the researchers said.](https://friendica-leipzig.de/photo/preview/600/367021)
![BadBox primarily targets Android devices (such as smartphones, tablets, connected TV streaming boxes and IoT devices) embedding malicious code into their firmware. According to previous reports, the operators of BadBox typically target low-cost devices, which are sold through online retailers or resale sites. [One Chinese manufacturer were shipped pre-installed with Triada malware, which is linked to BadBox's operators.]
<https://www.humansecurity.com/newsroom/human-disrupts-digital-supply-chain-threat-actor-scheme-originating-from-china>
The BSI reported that the BadBox malware it found on infected devices, like digital photo frames and streaming devices, can secretly create email and messenger accounts. This enables the malware to spread fake news, carry out advertising fraud and serve as a proxy, allowing criminals to exploit the devices internet connections for cyberattacks or illegal content distribution.
"Malware on internet-enabled products is unfortunately not a rare phenomenon. Outdated firmware versions, in particular, pose a huge risk," BSI president Claudia Plattner said in a statement. "We all have a duty here: manufacturers and retailers have a responsibility to ensure that such devices do not come onto the market."
Device owners who are impacted by this sinkholing operation will be notified by their internet service providers based on their IP address. BadBox primarily targets Android devices (such as smartphones, tablets, connected TV streaming boxes and IoT devices) embedding malicious code into their firmware. According to previous reports, the operators of BadBox typically target low-cost devices, which are sold through online retailers or resale sites. [One Chinese manufacturer were shipped pre-installed with Triada malware, which is linked to BadBox's operators.]
<https://www.humansecurity.com/newsroom/human-disrupts-digital-supply-chain-threat-actor-scheme-originating-from-china>
The BSI reported that the BadBox malware it found on infected devices, like digital photo frames and streaming devices, can secretly create email and messenger accounts. This enables the malware to spread fake news, carry out advertising fraud and serve as a proxy, allowing criminals to exploit the devices internet connections for cyberattacks or illegal content distribution.
"Malware on internet-enabled products is unfortunately not a rare phenomenon. Outdated firmware versions, in particular, pose a huge risk," BSI president Claudia Plattner said in a statement. "We all have a duty here: manufacturers and retailers have a responsibility to ensure that such devices do not come onto the market."
Device owners who are impacted by this sinkholing operation will be notified by their internet service providers based on their IP address.](https://friendica-leipzig.de/photo/preview/1024/363688)
![It's worth noting that CVE-2024-49138 is the fifth actively exploited CLFS privilege escalation flaw since 2022 after CVE-2022-24521, CVE-2022-37969, CVE-2023-23376 and CVE-2023-28252 (CVSS scores: 7.8). It's also the ninth vulnerability in the same component to be patched this year.
The fact that CLFS has become an attractive attack pathway for malicious actors has not gone unnoticed by Microsoft, which said it's working to add a new verification step when parsing such log files.
The number of fixed bugs in each vulnerability category is listed below:
• 27 Elevation of Privilege Vulnerabilities
• 30 Remote Code Execution Vulnerabilities
• 7 Information Disclosure Vulnerabilities
• 5 Denial of Service Vulnerabilities
• 1 Spoofing Vulnerabilities
[This count does not include two Edge flaws that were previously fixed on December 5 and 6th.] It's worth noting that CVE-2024-49138 is the fifth actively exploited CLFS privilege escalation flaw since 2022 after CVE-2022-24521, CVE-2022-37969, CVE-2023-23376 and CVE-2023-28252 (CVSS scores: 7.8). It's also the ninth vulnerability in the same component to be patched this year.
The fact that CLFS has become an attractive attack pathway for malicious actors has not gone unnoticed by Microsoft, which said it's working to add a new verification step when parsing such log files.
The number of fixed bugs in each vulnerability category is listed below:
• 27 Elevation of Privilege Vulnerabilities
• 30 Remote Code Execution Vulnerabilities
• 7 Information Disclosure Vulnerabilities
• 5 Denial of Service Vulnerabilities
• 1 Spoofing Vulnerabilities
[This count does not include two Edge flaws that were previously fixed on December 5 and 6th.]](https://friendica-leipzig.de/photo/preview/1024/351820)