Suche
Beiträge, die mit SECURITY getaggt sind
https://www.numerama.com/cyberguerre/1869958-un-cybercriminel-membre-du-celebre-gang-de-hackers-lockbit-se-cachait-en-israel.html
#Infosec #Security #Cybersecurity #CeptBiro #Cybercriminel #Lockbit #Israel

Un cybercriminel membre du célèbre gang de hackers Lockbit se cachait en Israël - Numerama
Un membre du groupe de hackers Lockbit, responsable de cyberattaques contre la France, a été arrêté en Israël. Il était chargé de développer des moyens de pression pour forcer à payer la rançon.Bogdan Bodnar (Numerama)
IT-Security researchers have discovered multiple vulnerabilities in the infotainment units used in some Skoda cars that could allow malicious actors to remotely trigger certain controls and track the car’s location in real time.
https://pcautomotive.com/vulnerabilities-in-skoda-and-volkswagen-vehicles
#skoda #mib3 #vulnerabilities #car #it #security #privacy #engineering #media #tech #news
Vulnerabilities in Skoda and Volkswagen vehicles
Vulnerabilities affecting Skoda and Volkswagen Group vehicles were originally identified in Skoda Superb III (3V3) - 2.0 TDI manufactured in 2022.pcautomotive.com
Oasis Security Research Team Discovers Microsoft Azure MFA Bypass: We Expect More From An Enterprise Provider Though

Oasis Security’s research team uncovered a critical vulnerability in Microsoft’s Multi-Factor Authentication (MFA) implementation, allowing attackers to bypass it and gain unauthorized access to the user’s account, including Outlook emails, OneDrive files, Teams chats, Azure Cloud, and more. Microsoft has more than 400 million paid Office 365 seats, making the consequences of this vulnerability far-reaching.
The bypass was simple: it took around an hour to execute, required no user interaction, and did not generate any notification or provide the account holder with any indication of trouble.
The news surfaced now in the last week, so Microsoft has addressed the issue already. For me, though, the real news is that a global enterprise level IT company should not have had such basic guardrails missing. It appears really that Microsoft had knowingly relaxed some measures around its 2FA to allow for convenience. But surely a lack of attack rate limiting is just unforgivable. One of the basics I always employ on my servers and blog, is attack rate limiting with lengthy blocks in place. If anyone has to guess a password or 2FA more than 3 times, there is something wrong.
Microsoft has had so many security fumbles over time that it is quite amazing that their monopoly in the workplace goes unchallenged. It seems Microsoft has very little care about their customers, as long as the money is rolling in, and if that eases, they just change the licensing parameters a bit. The recent Microsoft Recall feature was just another example of completely not appreciating their customers’ privacy, and that was also only addressed after a major outcry.
Microsoft probably has too much inertia, but actually there are some pretty good alternatives around if one takes a little trouble to rise out of the deep rut. The combination of pretty admin tools, AI, and cloud services has unfortunately made many admins way too lazy today. I think the quality of our admins on the edge, is a lot weaker than it used to be two decades back. All this usually means an even greater reliance on Microsoft where it is used in a corporate environment.
Security is about keeping it simple, and having a reasonable depth of knowledge about what is being managed.
See https://www.oasis.security/resources/blog/oasis-security-research-team-discovers-microsoft-azure-mfa-bypass
#Blog, #2fa, #security, #technology
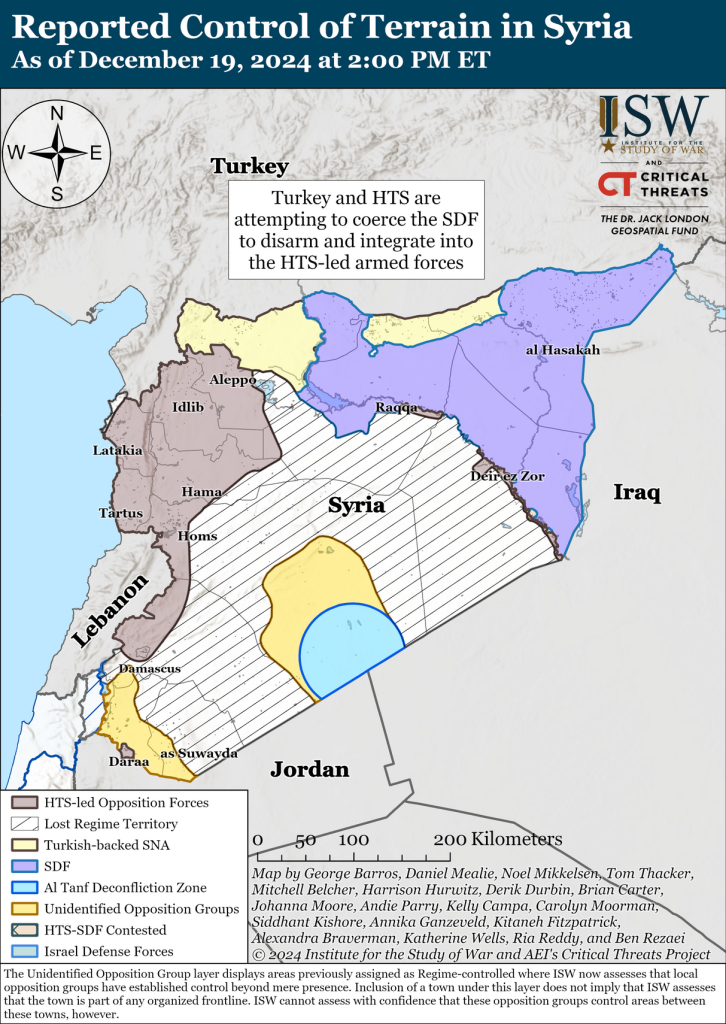
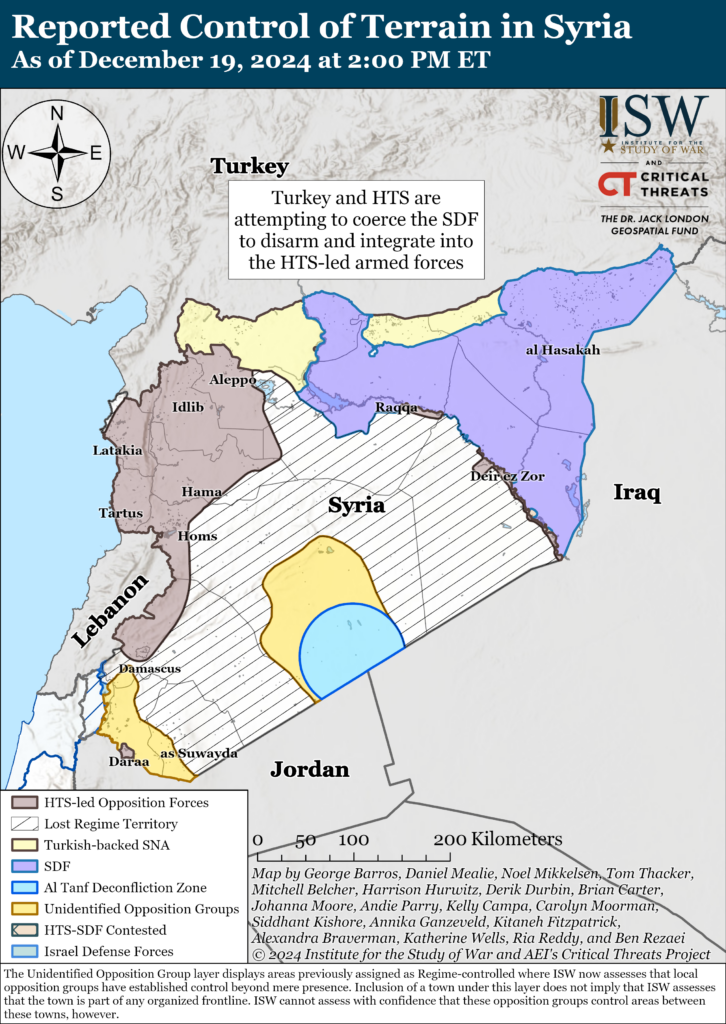
Iran Update, December 19, 2024 - EUROPE SAYS
Iran Update, December 19, 2024 Johanna Moore, Kelly Campa, Katherine Wells, Carolyn Moorman, Ria Reddy, Alexandra Braverman,EUROPE SAYS (EUROPESAYS.COM)
EU urges release of official detained in Belarus – POLITICO
According to one EU official, Khilo is expected to stand trial on Dec. 23, while a second official said he faces a sentence of between four and 12 years.BYTESEU (Bytes Europe)
Iran Update, December 19, 2024
Iran Update, December 19, 2024 Johanna Moore, Kelly Campa, Katherine Wells, Carolyn Moorman, Ria Reddy, Alexandra Braverman, Ben Rezaei, Annika Ganzeveld, and Brian Carter Information Cutoff: 2:00 pm ET The Critical Threats Project (CTP) at the Ame…BYTESEU (Bytes Europe)
EU urges release of official detained in Belarus – POLITICO - EUROPE SAYS
According to one EU official, Khilo is expected to stand trial on Dec. 23, while a second officialEUROPE SAYS (EUROPESAYS.COM)

EU urges release of official detained in Belarus
Renew MEP says Belarus is testing the bloc’s “position and response,” and that Brussels must “send a clear message” to Minsk.Jacopo Barigazzi (POLITICO)
Ein neuer Beitrag auf meinem Blog. Grundlagen zum Thema SBOMs.
https://blog.security-manufaktur.de/sbom/bom/cyclonedx/spdx/opensource/oss/2024/12/17/sbom-grundlagen.html
#bom #sbom #sboms #software #softwaredevelopment #softwarebillofmaterials #SoftwareBillsofMaterialSBOMs #dev #devops #development #developer #blog #cybersecurity #security #cyclonedx #spdx #vex
SBOM: Die Zutatenliste für Software
SBOM – Die Zutatenliste für Softwareprodukted33pjs (Security Manufaktur Blog)

IT-security researchers have uncovered a new Linux rootkit called PUMAKIT that comes with capabilities to escalate privileges, hide files & directories, and conceal itself from system tools, while simultaneously evading detection.
https://www.elastic.co/security-labs/declawing-pumakit
#linux #pumakit #malware #it #security #privacy #engineer #media #tech #news
Declawing PUMAKIT — Elastic Security Labs
PUMAKIT is a sophisticated loadable kernel module (LKM) rootkit that employs advanced stealth mechanisms to hide its presence and maintain communication with command-and-control servers.www.elastic.co
The Federal Office for Information Security (BSI) announced that it had blocked communication between the infected Android IoT devices and the criminal’s command-and-control (C2) servers, to preventing further damage.
https://www.bsi.bund.de/DE/Service-Navi/Presse/Pressemitteilungen/Presse2024/241212_Badbox_Sinkholing.html
#android #badbox #bsi #it #security #privacy #engineer #media #tech #news
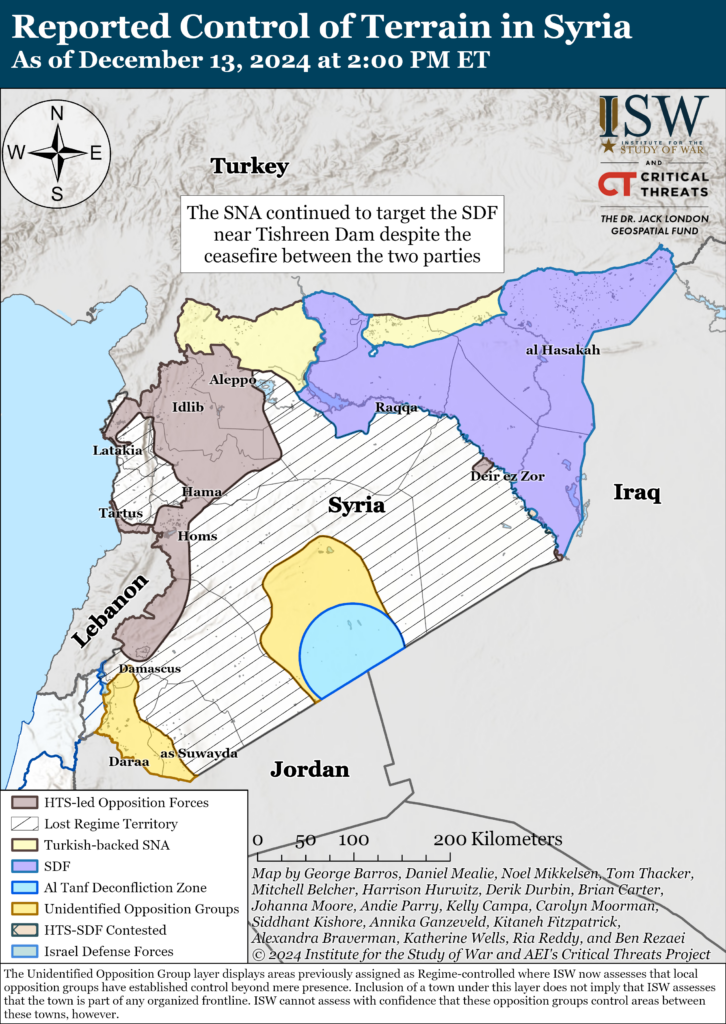
Iran Update, December 13, 2024
Iran Update, December 13, 2024 Johanna Moore, Annika Ganzeveld, Kelly Campa, Alexandra Braverman, Siddhant Kishore, Ben Rezaei, Christina Harward, Adiv Kuray, Avery Borens, and Brian Carter Information Cutoff: 2:00 pm ET The Critical Threats Projec…BYTESEU (Bytes Europe)
https://www.securityweek.com/iranian-hackers-use-iocontrol-malware-to-target-ot-iot-devices-in-us-israel/
#Infosec #Security #Cybersecurity #CeptBiro #IranianHackers #IOCONTROL #Malware #OT #IoTDevices #US #Israel
Microsoft resolved 72 vulnerabilities in a variety of its products, including a zero-day [CVE-2024-49138 (CVSS score: 7.8)] that’s been exploited by attackers in the wild to execute code with higher privileges, and 16 critical vulnerabilities (all of which are remote code execution flaws).
https://msrc.microsoft.com/update-guide/releaseNote/2024-Dec
#microsoft #windows #update #it #security #privacy #engineer #media #tech #news
Europe’s Syrians shaken by debate over repatriation to their war-ravaged homeland – POLITICO - EUROPE SAYS
Germany’s interior minister, Nancy Faeser, a member of Scholz’s Social Democratic Party (SPD), also warned that an exodusEUROPE SAYS (EUROPESAYS.COM)

What Hamas wrought
Instead of igniting a war that would destroy Israel, the militant group lit the fuse that set much of the region on fire, burning its own allies above all.Frida Ghitis (POLITICO)
EFF Launches Digital Rights Bytes to Answer Tech Questions that Bug Us All

Yes, politicians and Big Corporates do twist narratives to suite their own agendas. EFF is aiming to try to give more objective and honest answers to technology questions, especially those which affect users’ privacy and security.
EFF is the leading nonprofit defending civil liberties in the digital world. Founded in 1990, EFF champions user privacy, free expression, and innovation through impact litigation, policy analysis, grassroots activism, and technology Development. Its mission is to ensure that technology supports freedom, justice and innovation for all people of the world.
An interesting twist is that you can submit your own questions and answers too (without providing your name, e-mail address, or a completed reCaptcha).
See https://www.eff.org/press/releases/eff-launches-digital-rights-bytes-answer-tech-questions-bug-us-all
#Blog, #EFF, #privacy, #security, #technology
Israel destroys targets across Syria as Russian vessels desert Tartus naval base – POLITICO - EUROPE SAYS
The port city of Latakia on the Mediterranean Sea came under heavy attack, the BBC reported. The SyrianEUROPE SAYS (EUROPESAYS.COM)

Russia could test NATO loyalty to ‘mutual defense’ clause – POLITICO
'But if such views gain the upper hand in the government headquarters in Moscow, the risk of a military conflict will grow in the coming years,” he said.BYTESEU (Bytes Europe)
The unlikelihood of an Asian NATO – POLITICO - EUROPE SAYS
But despite the absence of a full-fledged entrance into NATO, cooperation continues to grow. Factoring in Asia’s disunity,EUROPE SAYS (EUROPESAYS.COM)
― Robert Southey
🔗 · https://poligraf.tumblr.com/post/744610514438668288/order-is-the-sanity-of-the-mind-the-health-of-the
#quotes #RobertSouthey #order #mind #sanity #peace #security
Poligraf · The Artistic Impulse
Order is the sanity of the mind, the health of the body, the peace of the city, the security of the state. — Robert Southeypoligraf (Tumblr)

Top Tony Blair aide becomes UK Palestine envoy
Government efficiency guru Michael Barber will take on a new Palestine-facing role.Andrew McDonald (POLITICO)
[Journalists, human rights defenders, lawmakers and political officials are frequent targets of state surveillance.]
The mobile device security firm iVerify has been offering a tool that makes spyware scanning accessible to anyone.
http://iverify.io/blog/iverify-mobile-threat-investigation-uncovers-new-pegasus-samples
#android #iphone #spyware #scanner #pegasus #it #security #privacy #engineer #media #tech #news
iVerify Mobile Threat Investigation Uncovers New Pegasus Samples
iVerify’s Mobile Threat Hunting finds Pegasus spyware is more prevalent and capable of infecting a wide range of devices, not just devices of high-risk users.iverify.io
#security #classified #topsecret

EU welcomes collapse of Syrian regime as Assad flees – POLITICO - EUROPE SAYS
British Deputy Prime Minister Angela Rayner welcomed the collapse of the ruling faction in an interview on SkyEUROPE SAYS (EUROPESAYS.COM)
https://www.news-cafe.eu/?go=news&n=13418
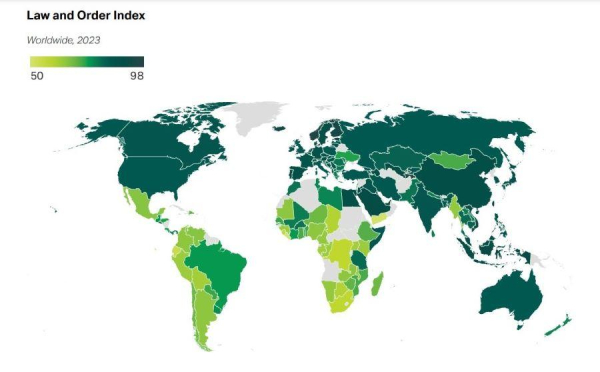
Kuwait was the world’s safest nation in 2023 - News Cafe
Gallup’s 2024 Global Safety Report suggests that democratic regime isn’t necessarily a guarantee of better law and order. High state control and community-based approaches are key solutions.www.news-cafe.eu
Romania’s pro-Europeans fear Putin is pushing them back to dictatorship – POLITICO - EUROPE SAYS
According to the latest polling from Atlas Intel, Georgescu is on 47 percent, a lead of four pointsEUROPE SAYS (EUROPESAYS.COM)
The Israel-Hezbollah Ceasefire Doesn’t Mean An End To Conflict In The Region - EUROPE SAYS
On December 3, Israeli Defense Minister Israel Katz went to northern Israel to meet with IDF troops andEUROPE SAYS (EUROPESAYS.COM)
They bought logs of people's whereabouts from app developers and other companies that carried out software-based tracking of location, and then resold it.
And thisis one reason why you should not grants your apps blanket access to all of your data on your phone and if you do provided limited access, be aware of where you are using them and when.
https://www.theregister.com/2024/12/04/ftc_data_brokers/
#Privacy #Security #DataForSale #Apps #Mobile
South Korea arrests CEO for adding DDoS feature to 240,000 satellite receivers

Allegedly, the functionality was needed to counter the attacks of a competing entity.
The exact way the DDoS functionality was leveraged on the devices was not specified, but these attacks are always illegal when targeting external systems.
Moreover, users of the satellite receivers were involuntarily taking part in attacks and might have experienced reduced device performance during these occurrences.
There has been more and more of a shift towards satellite communications for civilian Internet and mobile phone use, so this is probably just a wake-up call for all of us to realise that those satellites sitting up there in plain view, are not just going to be “allowed” to be used without any interference or weaponizations.
It will be both military (and I include all nations here) who will try to intercept or even block messages, as well as the usual hacking and ransomware suspects who will try to exploit them. The military of all nations will be pushing to have their encryption back doors included, and will want to be able to disable civilian satellite services “in times of need”.
All I’m saying is, we cannot assume these satellites will all just be there functioning in our interests 100% of the time. Of all the communications mediums ever invented, satellites are the most exposed and vulnerable of all. In other words, be sure not to rely solely on satellite communications in the future. Consider them a useful supplementary tool for communications, but do not neglect your more traditional means of communications.
See https://www.bleepingcomputer.com/news/security/korea-arrests-ceo-for-adding-ddos-feature-to-satellite-receivers
#Blog, #satellites, #security, #technology, #vulnerability
https://aliyesha.com/sub/articles/news/display/hp_security_measures_stiff_winter_session
#himachal #dharamshala #india #news #press #government #governance #winter #WinterSession #AssemblySession #security #surveillance
Enjoy tracker free reading with us. #privacy #privacymatters

Dharamshala: Security measures will not be compromised during Winter Session: Assembly Speaker.
CCTV and Drone Cameras to ensure surveillance.Rahul (Aliyesha)
https://aliyesha.com/sub/articles/news/display/hp_security_measures_stiff_winter_session
#himachal #dharamshala #india #news #press #government #governance #winter #WinterSession #AssemblySession #security #surveillance
Enjoy tracker free reading with us. #privacy #privacymatters





![[ImageSource: Elastic Security]
Pumakit Infection Chain.
Pumakit employs a multi-stage infection process starting with a dropper named 'cron,' which executes embedded payloads ('/memfd:tgt' and '/memfd:wpn') entirely from memory.
The '/memfd:wpn' payload, which executes in a child process, performs environment checks and kernel image manipulation and eventually deploys the LKM rootkit module ('puma.ko') into the system kernel.
Embedded within the LKM rootkit is Kitsune SO ('lib64/libs.so'), acting as the userland rootkit that injects itself into processes using 'LD_PRELOAD' to intercept system calls at the user level. [ImageSource: Elastic Security]
Pumakit Infection Chain.
Pumakit employs a multi-stage infection process starting with a dropper named 'cron,' which executes embedded payloads ('/memfd:tgt' and '/memfd:wpn') entirely from memory.
The '/memfd:wpn' payload, which executes in a child process, performs environment checks and kernel image manipulation and eventually deploys the LKM rootkit module ('puma.ko') into the system kernel.
Embedded within the LKM rootkit is Kitsune SO ('lib64/libs.so'), acting as the userland rootkit that injects itself into processes using 'LD_PRELOAD' to intercept system calls at the user level.](https://friendica-leipzig.de/photo/preview/600/367019)
![[ImageSource: Elastic Security]
Pumakit using ftrace to hook Syscalls.
The malware uses the internal Linux function tracer (ftrace) to hook into as many as 18 different system calls and various kernel functions such as "prepare_creds," and "commit_creds" to alter core system behaviors and accomplish its goals.
<https://www.kernel.org/doc/html/latest/trace/ftrace.html>
"Unique methods are used to interact with Pumakid, including using the rmdir() syscall for privilege escalation and specialized commands for extracting configuration and runtime information," the researchers said. [ImageSource: Elastic Security]
Pumakit using ftrace to hook Syscalls.
The malware uses the internal Linux function tracer (ftrace) to hook into as many as 18 different system calls and various kernel functions such as "prepare_creds," and "commit_creds" to alter core system behaviors and accomplish its goals.
<https://www.kernel.org/doc/html/latest/trace/ftrace.html>
"Unique methods are used to interact with Pumakid, including using the rmdir() syscall for privilege escalation and specialized commands for extracting configuration and runtime information," the researchers said.](https://friendica-leipzig.de/photo/preview/600/367021)
![BadBox primarily targets Android devices (such as smartphones, tablets, connected TV streaming boxes and IoT devices) embedding malicious code into their firmware. According to previous reports, the operators of BadBox typically target low-cost devices, which are sold through online retailers or resale sites. [One Chinese manufacturer were shipped pre-installed with Triada malware, which is linked to BadBox's operators.]
<https://www.humansecurity.com/newsroom/human-disrupts-digital-supply-chain-threat-actor-scheme-originating-from-china>
The BSI reported that the BadBox malware it found on infected devices, like digital photo frames and streaming devices, can secretly create email and messenger accounts. This enables the malware to spread fake news, carry out advertising fraud and serve as a proxy, allowing criminals to exploit the devices internet connections for cyberattacks or illegal content distribution.
"Malware on internet-enabled products is unfortunately not a rare phenomenon. Outdated firmware versions, in particular, pose a huge risk," BSI president Claudia Plattner said in a statement. "We all have a duty here: manufacturers and retailers have a responsibility to ensure that such devices do not come onto the market."
Device owners who are impacted by this sinkholing operation will be notified by their internet service providers based on their IP address. BadBox primarily targets Android devices (such as smartphones, tablets, connected TV streaming boxes and IoT devices) embedding malicious code into their firmware. According to previous reports, the operators of BadBox typically target low-cost devices, which are sold through online retailers or resale sites. [One Chinese manufacturer were shipped pre-installed with Triada malware, which is linked to BadBox's operators.]
<https://www.humansecurity.com/newsroom/human-disrupts-digital-supply-chain-threat-actor-scheme-originating-from-china>
The BSI reported that the BadBox malware it found on infected devices, like digital photo frames and streaming devices, can secretly create email and messenger accounts. This enables the malware to spread fake news, carry out advertising fraud and serve as a proxy, allowing criminals to exploit the devices internet connections for cyberattacks or illegal content distribution.
"Malware on internet-enabled products is unfortunately not a rare phenomenon. Outdated firmware versions, in particular, pose a huge risk," BSI president Claudia Plattner said in a statement. "We all have a duty here: manufacturers and retailers have a responsibility to ensure that such devices do not come onto the market."
Device owners who are impacted by this sinkholing operation will be notified by their internet service providers based on their IP address.](https://friendica-leipzig.de/photo/preview/1024/363688)
![It's worth noting that CVE-2024-49138 is the fifth actively exploited CLFS privilege escalation flaw since 2022 after CVE-2022-24521, CVE-2022-37969, CVE-2023-23376 and CVE-2023-28252 (CVSS scores: 7.8). It's also the ninth vulnerability in the same component to be patched this year.
The fact that CLFS has become an attractive attack pathway for malicious actors has not gone unnoticed by Microsoft, which said it's working to add a new verification step when parsing such log files.
The number of fixed bugs in each vulnerability category is listed below:
• 27 Elevation of Privilege Vulnerabilities
• 30 Remote Code Execution Vulnerabilities
• 7 Information Disclosure Vulnerabilities
• 5 Denial of Service Vulnerabilities
• 1 Spoofing Vulnerabilities
[This count does not include two Edge flaws that were previously fixed on December 5 and 6th.] It's worth noting that CVE-2024-49138 is the fifth actively exploited CLFS privilege escalation flaw since 2022 after CVE-2022-24521, CVE-2022-37969, CVE-2023-23376 and CVE-2023-28252 (CVSS scores: 7.8). It's also the ninth vulnerability in the same component to be patched this year.
The fact that CLFS has become an attractive attack pathway for malicious actors has not gone unnoticed by Microsoft, which said it's working to add a new verification step when parsing such log files.
The number of fixed bugs in each vulnerability category is listed below:
• 27 Elevation of Privilege Vulnerabilities
• 30 Remote Code Execution Vulnerabilities
• 7 Information Disclosure Vulnerabilities
• 5 Denial of Service Vulnerabilities
• 1 Spoofing Vulnerabilities
[This count does not include two Edge flaws that were previously fixed on December 5 and 6th.]](https://friendica-leipzig.de/photo/preview/1024/351820)