Suche
Beiträge, die mit SECURITY getaggt sind
Be careful of misleading security claims by hosting companies: US FTC cracks down on GoDaddy

The Federal Trade Commission (FTC) will require web hosting giant GoDaddy to implement basic security protections, including HTTPS APIs and mandatory multifactor authentication, to settle charges that it failed to secure its hosting services against attacks since 2018.
FTC says the Arizona-based company’s claims of reasonable security practices also misled millions of web-hosting customers because GoDaddy was instead “blind to vulnerabilities and threats in its hosting environment” due to its failings to implement standard security tools and practices.
The big problem is the company claimed to have robust security measures in place, but lots of basic security practices were found not to be in place, and they had multiple major security breaches over time.
According to a proposed settlement order, the FTC will require GoDaddy to establish a robust information security program and prohibits the company from misleading customers about its security protections. The order also mandates that GoDaddy hire an independent third-party assessor to conduct biennial reviews of its information security program.
It really appears that this was almost tantamount to fraud — where you promise something in writing to customers, but in fact, that is not what you are delivering behind the scenes.
Hopefully it is a major wakeup call to other hosting providers. Promise what you are delivering on, and don’t promise what you are not doing. It is really as simple as that. Independent security audits are certainly a desirable practice to have in place, along with how regularly it is performed.
See https://www.bleepingcomputer.com/news/security/ftc-orders-godaddy-to-fix-poor-web-hosting-security-practices
#Blog, #security, #technology, #vulnerabilities
https://github.com/GrapheneOS/platform_packages_apps_GmsCompat/releases/tag/config-153
See the linked release notes for a summary of the improvements over the previous release and a link to the full changelog.
Forum discussion thread:
https://discuss.grapheneos.org/d/19423-gmscompatconfig-version-153-released
#GrapheneOS #privacy #security #gmscompat
Release config-153 · GrapheneOS/platform_packages_apps_GmsCompat
Changes in version 153: update max supported version of Play Store to 44.5 disable update_install_enable_resume_on_reboot flag to work around crashes on end-of-life devices still on Android 13 A ...GitHub
Having Barcelona become a crucial regional outpost for offensive cybersecurity companies puts the spyware problem squarely on the doorstep of Europe, which has a fractious relationship with surveillance tech, due to scandals in Cyprus, Greece, Hungary, and Poland — all involving Israeli spyware makers.
#Barcelona #spain #israel #spyware #startups #business #malware #security #cybersecurity #privacy #surveillance
https://techcrunch.com/2025/01/13/how-barcelona-became-an-unlikely-hub-for-spyware-startups/

How Barcelona became an unlikely hub for spyware startups | TechCrunch
Barcelona's mix of affordable cost of living and quality of life has helped create a vibrant startup community — and become a hotbed for the creation of surveillance technologies.Lorenzo Franceschi-Bicchierai (TechCrunch)
Iran Update, January 24, 2025 - EUROPE SAYS
Iran Update, January 24, 2025 Carolyn Moorman, Johanna Moore, Alexandra Braverman, Ria Reddy, Ben Rezaei, and NicholasEUROPE SAYS (EUROPESAYS.COM)
Webscript security company c/side discovered during an incident response engagement for one of their clients that the malicious activity uses the wp3[.]xyz domain to exfiltrate data but have yet to determine the initial infection vector.
https://cside.dev/blog/over-5k-wordpress-sites-caught-in-wp3xyz-malware-attack
#wordpress #malicious #plugin #it #security #privacy #engineer #media #tech #news
Over 5,000 WordPress sites caught in WP3[.]XYZ malware attack
We’ve uncovered a widespread malware campaign targeting WordPress websites, affecting over 5,000 sites globally. The malicious domain: "https://wp3.xyz/plugin[.]php".c/side
Nach einem Datenleck bei einem Betreiber medizinischer Zentren in Dänemark sind persönliche Patientendaten veröffentlicht worden. Patienten sind verunsichert.
https://www.heise.de/news/Datenabfluss-bei-Gesundheitsunternehmen-Daenen-bangen-um-sensible-Informationen-10254683.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#DigitalHealth #Ransomware #Security #news
Für erfolgreiche Angriffe auf Schutzfunktionen des Mikrocontrollers RP2350 lobten die Raspi-Macher ein Preisgeld aus, das sie nun viermal auszahlten.
https://www.heise.de/news/Raspberry-Pi-RP2350-Sicherheitsfunktionen-geknackt-10254523.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#ARM #Hacking #Mikrocontroller #RaspberryPi #Security #Sicherheitslücken #news
Die Sicherheitslücke wird bereits von Missetätern angewendet, so der Hersteller. Wer die betroffene Appliance einsetzt, sollte patchen.
https://www.heise.de/news/Sicherheits-Appliance-Angreifer-kapern-SonicWall-Geraete-mit-Systemkommandos-10254491.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Exploit #Security #Dell #news
Thirty-five years ago, as December 1989 turned into January 1990, the then-largest ever cybercrime investigation was launched in response to the world's first known example of ransomware.
https://www.heise.de/news/Missing-Link-35-Jahre-Ransomware-am-Anfang-stand-eine-unscheinbare-Diskette-10247344.html
#ransomware #history #retrocomputing #retro #it #security #privacy #engineer #media #tech #news
Missing Link: Die Ära der Ransomware beginnt mit einer 5,25"-Diskette
Vor 35 Jahren markierte eine schlichte 5,25 Zoll-Diskette mit der Aufschrift "AIDS Information" den Beginn einer der größten Geißeln der vernetzten Menschheit.Stefan Krempl (heise online)
Cisco warnt vor einer kritischen Sicherheitslücke in Meeting Management sowie Schwachstellen in Broadworks und ClamAV.
https://www.heise.de/news/Cisco-Kritische-Sicherheitsluecke-in-Meeting-Management-10253499.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Cisco #Virenscanner #Security #Sicherheitslücken #news
Angreifer könnten die Lücken ausnutzen, um dem UnRAID-Admin eigenen Javascript-Code oder bösartige Plug-ins unterzuschieben.
https://www.heise.de/news/Heimserver-Betriebssystem-Updates-beheben-Sicherheitsluecken-in-Unraid-10253366.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#XSS #NAS #Security #news
Während Behörden in Frankreich und den USA die Schadsoftware Plug-X auf betroffenen Computern abschalten, wird in Deutschland über Infektionen nur informiert.
https://www.heise.de/news/Botnetz-Plug-X-Reinemachen-geht-nicht-10252309.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Bundeskriminalamt #Botnet #BSI #Cybercrime #Security #news
https://github.com/GrapheneOS/Vanadium/releases/tag/132.0.6834.122.0
See the linked release notes for a summary of the improvements over the previous release and a link to the full changelog.
Forum discussion thread:
https://discuss.grapheneos.org/d/19322-vanadium-version-132068341220-released
#GrapheneOS #privacy #security #browser
Release 132.0.6834.122.0 · GrapheneOS/Vanadium
Changes in version 132.0.6834.122.0: update to Chromium 132.0.6834.122 A full list of changes from the previous release (version 132.0.6834.79.2) is available through the Git commit log between t...GitHub
In den vergangenen Wochen gab es großflächige Angriffe auf Zugangsdaten zur Microsoft-Cloud. IT-Admins sollten prüfen, ob diese eventuell erfolgreich waren.
https://www.heise.de/news/Grossflaechige-Brute-Force-Angriffe-auf-M365-vorsichtshalber-Log-ins-checken-10252167.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#ZweifaktorAuthentisierung #Microsoft #MicrosoftAzure #Passwörter #Security #news
For #trans people in the #US.
The US is now under a #fascist #authoritarian #regime. Here's some #safety tips.
Avoid using a mobile #phone in #conservative states. Disable #location services. Always use a #VPN. Consider all #corporate #online service to be potential #security risk.
Stock up on #hormones and #medications. Keep a bag with everything you need to #survive at least 3-5 days.
https://www.890.blog/post/my-thoughts-on-grapheneos
#GrapheneOS #Privacy #Security #TechReview #890Blog #OpenSource #Android
My thoughts on GrapheneOS
I've been using GrapheneOS on my Google Pixel 9 Pro XL for about six months now, and it's been great. It's considerably better than standard Android 14. Plus, unlike Google's Android 14 flavor, it's completely FOSS (Free and Open Source Software).Marco Liberale (890 Blog)
https://github.com/obfusk/fdroid-fakesigner-poc?tab=readme-ov-file#update-2025-01-19
#fdroid #security #privacy #certpinning #signature

GitHub - obfusk/fdroid-fakesigner-poc: F-Droid Fake Signer PoC
F-Droid Fake Signer PoC. Contribute to obfusk/fdroid-fakesigner-poc development by creating an account on GitHub.GitHub
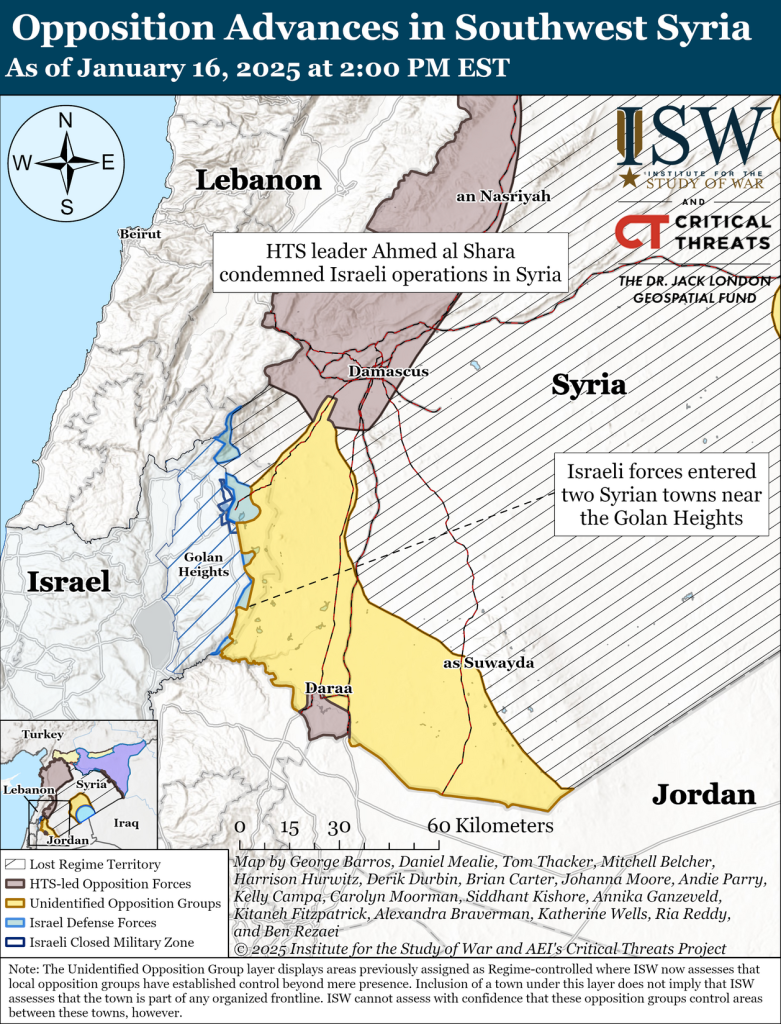
Syria’s Future Depends On The Kurds - EUROPE SAYS
After more than fifty years of iron-fisted rule, the Assad regime in Syria was finally overthrown a fewEUROPE SAYS (EUROPESAYS.COM)
https://aliyesha.com/sub/articles/news/display/nd_delhi_elections_and_republic_day_vigilance
#newdelhi #delhi #india #news #press #police #elections2025 #RepublicDay2025 #security #weapons #drugs #MoneyLaundering #safety #security
Enjoy tracker free reading with us. #privacy #privacymatters

नई दिल्ली: दिल्ली पुलिस ने कसी कमर: विधानसभा चुनाव और गणतंत्र दिवस के लिए सघन अभियान।
दिल्ली विधानसभा चुनाव और गणतंत्र दिवस को लेकर दिल्ली पुलिस पूरी तरह एक्शन मोड में आ गई है।दिल्ली ब्यूरो (Aliyesha)
Der neue US-Präsident macht dutzende Erlässe seines Vorgängers rückgängig und bremst so Innovation. Also braucht es mehr Energie, die Öl und Gas bringen sollen.
https://www.heise.de/news/Trump-kuendigt-KI-Sicherheit-auf-stoppt-Umweltschutz-und-Infrastruktur-10249761.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Arbeitswelt #Deepfake #DonaldTrump #Elektroauto #Elektromobilität #Energie #Gesundheit #Security #JoeBiden #KünstlicheIntelligenz #Klimaschutz #Politik #Recht #Umweltschutz #Windkraft #news
The cat-and-mouse game between state-sponsored Russian threat actor group’s and one of the world’s biggest technology companies has continued into 2025.
https://www.microsoft.com/en-us/security/blog/2025/01/16/new-star-blizzard-spear-phishing-campaign-targets-whatsapp-accounts/
#whatsapp #phishing #campaign #it #security #privacy #engineer #media #tech #news
New Star Blizzard spear-phishing campaign targets WhatsApp accounts | Microsoft Security Blog
In mid-November 2024, Microsoft Threat Intelligence observed the Russian threat actor we track as Star Blizzard sending their typical targets spear-phishing messages, this time offering the supposed opportunity to join a WhatsApp group.Microsoft Threat Intelligence (Microsoft Security Blog)
Mit der Kernel-Erweiterung SELinux sichern Admins Linux-Systeme umfassend ab. Der Workshop zeigt, wie man SELinux konfiguriert und richtig nutzt.
https://www.heise.de/news/Der-grosse-c-t-Workshop-Linux-Systeme-absichern-mit-SELinux-10241413.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Linux #OpenSource #Security #news
Kriminelle haben Daten bei der Verwaltungsplattform Otelier geklaut. Rund 437.000 Datensätze etwa von Hilton, Hyatt oder Marriott sind nun bei HIBP.
https://www.heise.de/news/Hilton-Hyatt-Marriott-437-000-Datensaetze-aus-Verwaltungsplattform-bei-HIBP-10248339.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Security #news
In fünf Terminen lernen Admins und IT-Security-Verantwortliche ab dem 10.02., wie sie mit Ethical Hacking Systeme absichern und Schwachstellen aufdecken.
https://www.heise.de/news/Proaktive-IT-Security-mit-Pentesting-Ethical-Hacking-fuer-Admins-10246220.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Hacking #Security #PenetrationTesting #news
Iran and Russia are Growing Military Ties in the Shadow of the Ukraine War
Relations between Iran and Russia continue to warm amidst an increasingly unstable geopolitical climate.BYTESEU (Bytes Europe)
[
 Sequoia 15.2]
Sequoia 15.2]Apple recently addressed a macOS vulnerability that allows attackers to bypass System Integrity Protection (SIP) and install malicious kernel drivers by loading third-party kernel extensions.
https://www.microsoft.com/en-us/security/blog/2025/01/13/analyzing-cve-2024-44243-a-macos-system-integrity-protection-bypass-through-kernel-extensions/
#apple #macos #update #it #security #privacy #engineer #media #tech #news
Analyzing CVE-2024-44243, a macOS System Integrity Protection bypass through kernel extensions | Microsoft Security Blog
Microsoft discovered a macOS vulnerability allowing attackers to bypass System Integrity Protection (SIP) by loading third party kernel extensions, which could lead to serious consequences, such as allowing attackers to install rootkits, create persi…Microsoft Threat Intelligence (Microsoft Security Blog)
Der Passwort-Manager Bitwarden ist unter Android nun als native App umgesetzt. Das soll ihn beschleunigen und besser integrieren.
https://www.heise.de/news/Bitwarden-als-native-App-fuer-Android-verfuegbar-10247083.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Android #Apps #iOS #Kotlin #Passwörter #Security #news
https://grapheneos.org/releases#2025011500
See the linked release notes for a summary of the improvements over the previous release.
Forum discussion thread:
https://discuss.grapheneos.org/d/19017-grapheneos-version-2025011500-released
#GrapheneOS #privacy #security
GrapheneOS releases
Official releases of GrapheneOS, a security and privacy focused mobile OS with Android app compatibility.GrapheneOS

Netanyahu: Gaza cease-fire deal is done and just needs Israeli government approval
Last-minute setbacks threatened to derail the agreement Thursday.Seb Starcevic (POLITICO)
Sicherheitsvorwürfe gegen GoDaddy + Wechsel des EU-Datenschützers + Raketenstart in Europa + EU-Rangliste der Glasfaser-Migration + Verbraucherschutz-Podcast
https://www.heise.de/news/Freitag-GoDaddy-mit-Sicherheitsdefiziten-kritischer-EU-Datenschuetzer-abgewaehlt-10246154.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Datenschutz #DeutscheTelekom #EU #Glasfaser #hoDaily #Hosting #Security #Verbraucherschutz #news
GoDaddy schützt gehostete Kunden-Websites nicht ausreichend und betreibt irreführende Werbung zum Datenschutz, sagt die FTC. Sie fordert robuste IT-Sicherheit.
https://www.heise.de/news/US-Verbraucherschuetzer-wollen-Webhoster-GoDaddy-zu-mehr-IT-Sicherheit-zwingen-10246138.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Cybersecurity #Datenschutz #Datensicherheit #FederalTradeCommission #Hosting #Internet #Security #Verbraucherschutz #news
Iran Update, January 16, 2025 - EUROPE SAYS
Iran Update, January 16, 2025 Siddhant Kishore, Andie Parry, Carolyn Moorman, Alexandra Braveman,EUROPE SAYS (EUROPESAYS.COM)
https://github.com/GrapheneOS/Vanadium/releases/tag/132.0.6834.79.2
See the linked release notes for a summary of the improvements over the previous release and a link to the full changelog.
Forum discussion thread:
https://discuss.grapheneos.org/d/19065-vanadium-version-13206834792-released
#GrapheneOS #privacy #security #browser
Release 132.0.6834.79.2 · GrapheneOS/Vanadium
Changes in version 132.0.6834.79.2: remove upstream code added in Chromium 132 generating debug information when memory tagging is disabled to avoid triggering a notification about an attempt to e...GitHub
Microsoft setzt Mitarbeiter vor die Tür. Neben weniger performanten Angestellten sind weitere betroffen. Der Umfang bleibt unklar.
https://www.heise.de/news/Microsoft-entlaesst-Mitarbeiter-in-mehreren-Abteilungen-10245328.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Spiele #Microsoft #Security #news
Netzwerktechnik von HPE Aruba ist verwundbar. Aktuelle Updates schließen insgesamt zwei Sicherheitslücken.
https://www.heise.de/news/Es-kann-Schadcode-auf-HPE-Aruba-Networking-AOS-Controllers-und-Gateways-gelangen-10244669.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Patchday #Security #Sicherheitslücken #Updates #news
Ivanti hat Sicherheitsupdates für Application Control Engine, Avalanche und EPM veröffentlicht. Sie bessern teils kritische Lecks aus.
https://www.heise.de/news/Ivanti-schliesst-Luecken-in-Application-Control-Engine-Avalanche-und-EPM-10244653.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Security #Sicherheitslücken #news

![[ImageSource: c/side]
After compromising a target, a malicious script loaded from the wp3[.]xyz domain creates the rogue admin account wpx_admin with credentials available in the code. The script then proceeds to install a malicious plugin (plugin.php) downloaded from the same domain, and activates it on the compromised website.
[⚠️Blocking the Attacks⚠️]
c/side recommends that website owners block the ‘wp3[.]xyz’ domain using firewalls and security tools. Moreover, admins should review other privileged accounts and the list of installed plugins, to identify unauthorized activity and remove them as soon as possible.
Finally, it is recommended that CSRF protections on WordPress sites be strengthened via unique token generation, server-side validation and periodic regeneration. Tokens should have a short expiration time to limit their validity period.
Implementing multi-factor authentication also adds protection to accounts with credentials that have already been compromised. [ImageSource: c/side]
After compromising a target, a malicious script loaded from the wp3[.]xyz domain creates the rogue admin account wpx_admin with credentials available in the code. The script then proceeds to install a malicious plugin (plugin.php) downloaded from the same domain, and activates it on the compromised website.
[⚠️Blocking the Attacks⚠️]
c/side recommends that website owners block the ‘wp3[.]xyz’ domain using firewalls and security tools. Moreover, admins should review other privileged accounts and the list of installed plugins, to identify unauthorized activity and remove them as soon as possible.
Finally, it is recommended that CSRF protections on WordPress sites be strengthened via unique token generation, server-side validation and periodic regeneration. Tokens should have a short expiration time to limit their validity period.
Implementing multi-factor authentication also adds protection to accounts with credentials that have already been compromised.](https://friendica-leipzig.de/photo/preview/600/489521)



![This first ransomware payload was secreted on a 5.25-inch floppy disk titled "AIDS Information — Introductory Diskette 2.0" [h/t Heise.de]. The pioneering ransomware was developed by one American biologist [Dr. Joseph Lewis Andrew Popp Jr.], and about 20.000 copies were distributed to subscribers of the magazine PC Business World, various mailing lists, and even to World Health Organization delegates during a conference on AIDS.
As one may be able to deduce by the years and names being thrown around, this attack's choice of target was highly intelligent and the method of delivery exploited people's existing fears of a terrifying new biological virus at a time when knowledge of regular computer viruses was at an all-time low — much less an all-new form of malware meant to extort its victims.
Compared to modern-day threat actor attacks, only file names [not the files themselves], were encrypted by this ransomware. Thanks to this, effective software countermeasures ("AIDSOUT" to remove it and "AIDSCLEAR" to check for hidden directories combined into "CLEARAID") were developed by John Sutcliffe and Jim Bates to rescue impacted parties. This first ransomware payload was secreted on a 5.25-inch floppy disk titled "AIDS Information — Introductory Diskette 2.0" [h/t Heise.de]. The pioneering ransomware was developed by one American biologist [Dr. Joseph Lewis Andrew Popp Jr.], and about 20.000 copies were distributed to subscribers of the magazine PC Business World, various mailing lists, and even to World Health Organization delegates during a conference on AIDS.
As one may be able to deduce by the years and names being thrown around, this attack's choice of target was highly intelligent and the method of delivery exploited people's existing fears of a terrifying new biological virus at a time when knowledge of regular computer viruses was at an all-time low — much less an all-new form of malware meant to extort its victims.
Compared to modern-day threat actor attacks, only file names [not the files themselves], were encrypted by this ransomware. Thanks to this, effective software countermeasures ("AIDSOUT" to remove it and "AIDSCLEAR" to check for hidden directories combined into "CLEARAID") were developed by John Sutcliffe and Jim Bates to rescue impacted parties.](https://friendica-leipzig.de/photo/preview/600/484378)







![It all starts with a spear-phishing email that purports to be from a U.S. government official to lend it a veneer of legitimacy and increase the likelihood that the victim would engage with them.
The message contains a quick response (QR) code that urges the recipients to join a supposed WhatsApp group on "the latest non-governmental initiatives aimed at supporting Ukraine NGOs." The code, is deliberately broken so as to trigger a response from the victim.
Should the email recipient reply, Star Blizzard sends a second message, asking them to click on a t[.]ly shortened link to join the WhatsApp group, while apologizing for the inconvenience caused. "When this link is followed, the target is redirected to a web page asking them to scan a QR code to join the group," Microsoft explained. "However, this QR code is actually used by WhatsApp to connect an account to a linked device and/or the WhatsApp Web portal."
<https://faq.whatsapp.com/1317564962315842/?cms_platform=web>
In the event the target follows the instructions on the site ("aerofluidthermo[.]org"), the approach allows the threat actor to gain unauthorized access to their WhatsApp messages and even exfiltrate the data via browser add-ons. It all starts with a spear-phishing email that purports to be from a U.S. government official to lend it a veneer of legitimacy and increase the likelihood that the victim would engage with them.
The message contains a quick response (QR) code that urges the recipients to join a supposed WhatsApp group on "the latest non-governmental initiatives aimed at supporting Ukraine NGOs." The code, is deliberately broken so as to trigger a response from the victim.
Should the email recipient reply, Star Blizzard sends a second message, asking them to click on a t[.]ly shortened link to join the WhatsApp group, while apologizing for the inconvenience caused. "When this link is followed, the target is redirected to a web page asking them to scan a QR code to join the group," Microsoft explained. "However, this QR code is actually used by WhatsApp to connect an account to a linked device and/or the WhatsApp Web portal."
<https://faq.whatsapp.com/1317564962315842/?cms_platform=web>
In the event the target follows the instructions on the site ("aerofluidthermo[.]org"), the approach allows the threat actor to gain unauthorized access to their WhatsApp messages and even exfiltrate the data via browser add-ons.](https://friendica-leipzig.de/photo/preview/1024/465350)




![[ImageSource: Microsoft]
Storagekitd SIP-related Entitlements.
"System Integrity Protection (SIP) serves as a critical safeguard against malware, attackers, and other cybersecurity threats, establishing a fundamental layer of protection for macOS systems," Microsoft said now in a report that provides more technical details on CVE-2024-44243.
"Bypassing SIP impacts the entire operating system's security and could lead to severe consequences, emphasizing the necessity for comprehensive security solutions that can detect anomalous behavior from specially entitled processes."
Microsoft security researchers have discovered multiple macOS vulnerabilities in recent years. A SIP bypass dubbed 'Shrootless' (CVE-2021-30892), reported in 2021, also allows attackers to perform arbitrary operations on compromised Macs and potentially install rootkits. [ImageSource: Microsoft]
Storagekitd SIP-related Entitlements.
"System Integrity Protection (SIP) serves as a critical safeguard against malware, attackers, and other cybersecurity threats, establishing a fundamental layer of protection for macOS systems," Microsoft said now in a report that provides more technical details on CVE-2024-44243.
"Bypassing SIP impacts the entire operating system's security and could lead to severe consequences, emphasizing the necessity for comprehensive security solutions that can detect anomalous behavior from specially entitled processes."
Microsoft security researchers have discovered multiple macOS vulnerabilities in recent years. A SIP bypass dubbed 'Shrootless' (CVE-2021-30892), reported in 2021, also allows attackers to perform arbitrary operations on compromised Macs and potentially install rootkits.](https://friendica-leipzig.de/photo/preview/600/454008)