Suche
Beiträge, die mit PRIVACY getaggt sind
Remplacez #Instagram par #Pixelfed et #Loops.
Remplacez #YouTube par #PeerTube.
Remplacez #Twitter / X par #Mastodon.
Remplacez #Facebook par #Diaspora ou #Pleroma.
Remplacez #Medium par #WriteFreely.
Ou mieux : arrêtez de raconter vos vies car on s’en fout.


#opensource #privacy #fediverse
cc
@pixelfed
@LemmyDev
@loops
@peertube
@Mastodon
@writefreely
Barrez-vous.

Albania’s TikTok ban raises rule of law questions – POLITICO
“In the EU,” the statement stressed, “any ban of digital services can be considered as a last resort and in relation to an infringement of the transparency and accountability obligations of the law, not in response to individual issues and pieces of …BYTESEU (Bytes Europe)
“When people pay for their family expenses using new forms of digital payments, they must be confident that their transactions are not tainted by harmful surveillance or errors,” said CFPB Director Rohit Chopra. “The CFPB is seeking public input on how to apply longstanding consumer and privacy protections to new and emerging payment mechanisms.”"
https://www.consumerfinance.gov/about-us/newsroom/cfpb-seeks-input-on-digital-payment-privacy-and-consumer-protections/
#USA #CFBP #DigitalPayments #Privacy #FinTech
https://blog.thenewoil.org/cybersecurity-and-privacy-for-beginners-ad-blocking
#blog

Cybersecurity & Privacy For Beginners: Ad Blocking
Many of us know we can do better on the internet. We know that we’re not using good security practices, and many of us know we’re being t...The New Oil
https://aliyesha.com/sub/articles/news/display/bh_nda_flags_off_rath_yatra_election_2025
#bihar #patna #india #news #press #politics #bjp #jdu #nda #elections2025 #RathYatra #Mission2025 #AssemblyElections #ElectionCampaign
Enjoy tracker free reading with us. #privacy #privacymatters

Patna: NDA Flags Off Rath Yatra Ahead of District-Level Worker's Conference.
In preparation for the 'NDA District-Level Worker's Conference', the ‘NDA Rath’ was ceremoniously flagged off from the Bihar JDU state office.Alok Sharma (Aliyesha)
https://aliyesha.com/sub/articles/news/display/nd_after_jat_card_bjp_brings_purvanchal
#newdelhi #delhi #india #news #press #politics #aap #bjp #elections #elections2025 #AssemblyElections #kejriwal #purvanchal #reservation #jat #JatCaste #CastePolitics #VoteBank
Enjoy tracker free reading with us. #privacy #privacymatters
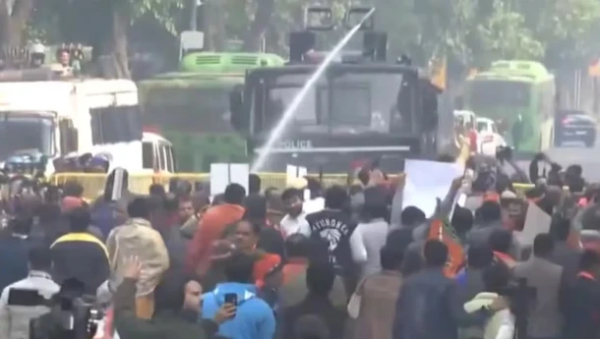
नई दिल्ली: दिल्ली चुनाव: जाट आरक्षण के बाद अब पूर्वांचल वोटर्स पर राजनीति गरमाई।
दिल्ली में आगामी चुनाव के मद्देनज़र जाट आरक्षण के बाद अब पूर्वांचल वोटर्स के मुद्दे पर राजनीतिक माहौल गरम है।दिल्ली ब्यूरो (Aliyesha)
At TEDIC, we are firmly committed to defending human rights, promoting transparency, and ensuring access to public information. We believe that, in a context where the state increasingly uses invasive surveillance te
https://www.tedic.org/landmark-court-ruling-in-paraguay-on-access-to-information-in-facial-recognition-case/
#Blog #InformationAccess #DigitalRights #litigation #PersonalData #Privacy
Sentencia histórica de la Corte en Paraguay sobre el acceso a la información en el caso de reconocimiento...
En TEDIC, nos mantenemos firmemente comprometidos con la defensa de los derechos humanos, la transparencia y el acceso a la información pública.TEDIC
In 2025, eight new state privacy laws will take effect, making a total of 25 around the country. A number of other states—like Vermont and Massachusetts—are considering passing their own privacy bills next year, and such laws could, in theory, force national legislation, says Woodrow Hartzog, a technology law scholar at Boston University School of Law. “Right now, the statutes are all similar enough that the compliance cost is perhaps expensive but manageable,” he explains. But if one state passed a law that was different enough from the others, a national law could be the only way to resolve the conflict. Additionally, four states—California, Texas, Vermont, and Oregon—already have specific laws regulating data brokers, including the requirement that they register with the state.
Along with new laws, says Justin Brookman, the director of technology policy at Consumer Reports, comes the possibility that “we can put some more teeth on these laws.”
Brookman points to Texas, where some of the most aggressive enforcement action at the state level has taken place under its Republican attorney general, Ken Paxton. Even before the state’s new consumer privacy bill went into effect in July, Paxton announced the creation of a special task force focused on enforcing the state’s privacy laws. He has since targeted a number of data brokers—including National Public Data, which exposed millions of sensitive customer records in a data breach in August, as well as companies that sell to them, like Sirius XM."
https://www.technologyreview.com/2025/01/07/1109301/privacy-protection-data-brokers-personal-information/
#USA #Privacy #DataProtection #DataBrokers #DataBrokerage
What’s next for our privacy?
The US still has no federal privacy law. But recent enforcement actions against data brokers may offer some new protections for Americans’ personal information.Eileen Guo (MIT Technology Review)
As scans from the IT-security threat monitoring platform Shadowserver show, 3.3 million hosts are running POP3/IMAP services without TLS encryption enabled and expose usernames & passwords in plain text when transmitted over the Internet.
https://www.shadowserver.org/what-we-do/network-reporting/vulnerable-pop3-report/
#pop3 #imap #mailservers #exposed #sniffing #tls #it #security #privacy #engineer #media #tech #news
HIGH: Vulnerable POP3 Report | The Shadowserver Foundation
This report identifies hosts that have a POP3 service running on port 110/TCP or 995/TCP without TLS support. This means that passwords used for mail access may be intercepted by a network sniffer.www.shadowserver.org
https://www.channelnewsasia.com/business/google-must-face-mobile-phone-privacy-class-action-possible-trial-4846396
#GOOGLE #LAWSUIT #PRIVACY #SMARTPHONES #KEWLNEWS #PRESS
https://www.404media.co/researcher-turns-insecure-license-plate-cameras-into-open-source-surveillance-tool/
#CAMERAS #PRIVACY #SURVEILLANCE #KEWLNEWS #PRESS
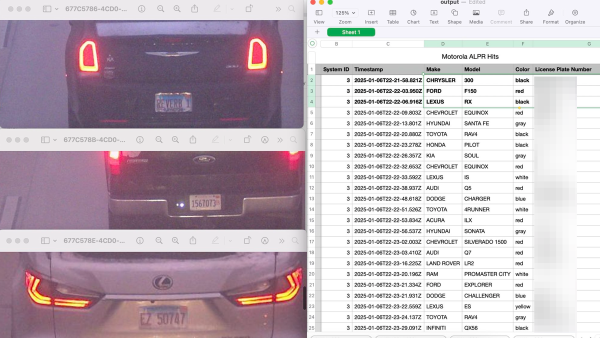
Researcher Turns Insecure License Plate Cameras Into Open Source Surveillance Tool
Privacy advocate draws attention to the fact that hundreds of police surveillance cameras are streaming directly to the open internet.Jason Koebler (404 Media)
https://aliyesha.com/sub/articles/news/display/hp_mswasth_kccbank_join_forces_rural_health
#himachal #dharamshala #india #news #press #health #rural #RuralHealth #Mswasth #KCCBank #Telemedicine #DigitalHealthcare
Enjoy tracker free reading with us. #privacy #privacymatters

Dharamshala: M-Swasth and KCC Bank Sign MoU to Enhance Healthcare in Rural Himachal Pradesh.
In a landmark partnership aimed at improving healthcare accessibility in rural Himachal, M-Swasth and KCC Bank join forces.Rajesh (Aliyesha)
The news is a crystalizing moment for the location data industry. For years, companies have harvested location information from smartphones, either through ordinary apps or the advertising ecosystem, and then built products based on that data or sold it to others. In many cases, those customers include the U.S. government, with arms of the military, DHS, the IRS, and FBI using it for various purposes. But collecting that data presents an attractive target to hackers.
“A location data broker like Gravy Analytics getting hacked is the nightmare scenario all privacy advocates have feared and warned about. The potential harms for individuals is haunting, and if all the bulk location data of Americans ends up being sold on underground markets, this will create countless deanonymization risks and tracking concerns for high risk individuals and organizations,” Zach Edwards, senior threat analyst at cybersecurity firm Silent Push, and who has followed the location data industry closely, told 404 Media. “This may be the first major breach of a bulk location data provider, but it won't be the last.”"
https://www.404media.co/hackers-claim-massive-breach-of-location-data-giant-threaten-to-leak-data/
#CyberSecurity #USA #Venntel #DataBreaches #LocationData #Surveillance #Privacy #DataProtection

Hackers Claim Massive Breach of Location Data Giant, Threaten to Leak Data
Gravy Analytics has been one of the most important companies in the location data industry for years, collating smartphone location data from around the world selling some to the U.S. government. Hackers say they stole a mountain of data.Joseph Cox (404 Media)
What do these privacy violations have in common? They share a source of data that’s shockingly pervasive and unregulated: the technology powering nearly every ad you see online.
Each time you see a targeted ad, your personal information is exposed to thousands of advertisers and data brokers through a process called “real-time bidding” (RTB). This process does more than deliver ads—it fuels government surveillance, poses national security risks, and gives data brokers easy access to your online activity. RTB might be the most privacy-invasive surveillance system that you’ve never heard of."
https://www.eff.org/deeplinks/2025/01/online-behavioral-ads-fuel-surveillance-industry-heres-how
#Privacy #Surveillance #CyberSecurity #AdTargeting #DataProtection #DataBrokers #DataBrokerage #RTB
https://tech.slashdot.org/story/25/01/04/2141224/how-ai-based-military-intelligence-powered-israels-attacks-on-gaza
#privacy #cybersecurtiy

How AI-Based Military Intelligence Powered Israel's Attacks on Gaza - Slashdot
It's "what some experts consider the most advanced military AI initiative ever to be deployed," reports the Washington Post. But the Israeli military's AI-powered intelligence practices are also "under scrutiny.tech.slashdot.org

Online Behavioral Ads Fuel the Surveillance Industry—Here’s How
Each time you see a targeted ad, your personal information is exposed to thousands of advertisers and data brokers through a process called “real-time bidding” (RTB).Electronic Frontier Foundation
https://asia.nikkei.com/Business/Technology/China-releases-draft-rules-on-cross-border-personal-data-transfer
#BIOMETRICS #CHINA #DATA #PRIVACY #KEWLNEWS #PRESS
He posted about it on social media.
He (like many) had negative experience w/#healthcare
Wrote review on controversal book - about tech dangers (as computer science grad - not unusual).
⭐ Main problem w/#MassSurveillance, & it's interdependent/symbiotic relationship w/#AI, is not merely #privacy - it's that *Anyone* can be made to appear guilty: w/enough #data collected.
Not claiming his innocence - I don't know. It's about the compromise of all. #luigiMangione
One of my goals for 2025 is to publish more regularly on the site, but the catch is I don’t always have things I want to blog about week after week. So, enter the Privacy Roundup.
Note: people who subscribe to the RSS feed and/or the newsletter get it hot off the press usually. 😇
#privacymatters #security #blog
https://avoidthehack.com/privacy-week1-2025
Newsletter, hosted by @buttondown, can be found at: https://buttondown.email/avoidthehack
The RSS feed is at: https://avoidthehack.com/home.rss

Privacy Roundup: Week 1 of Year 2025
Week 1 of 2025 of the Privacy Roundup. This edition includes news items covering: identity documents leaked to the public internet, Apple settling a privacy-related lawsuit concerning Siri, US Treasury hacked by China-connected APTs, and moreAvoid the Hack (avoidthehack!)
https://www.ilfattoquotidiano.it/in-edicola/articoli/2025/01/02/british-journalist-could-face-years-in-prison-for-refusing-to-hand-over-his-passwords-to-the-police/7822432/
#humanrights #infosec #privacy

British journalist could face years in prison for refusing to hand over his passwords to the police
Richard Medhurst is the first reporter arrested and under investigation under Section 12 of the Terrorism Act 2000. The UK police have sought to obtain the passwords to his phones, including a highly secure phone with a Graphene operating system.Stefania Maurizi (Il Fatto Quotidiano)
Before you dive in, know that there are many ways to shore up your safety and privacy. It’s OK to take them on slowly but surely, one at a time. If you run into any challenges, remember: the Digital Security Training team at Freedom of the Press Foundation (FPF) is here to help. Reach out here."
https://freedom.press/digisec/blog/journalists-digital-security-checklist/
#USA #PressFreedom #Journalism #CyberSecurity #Privacy #DataProtection

The 2025 journalist’s digital security checklist
Our digital security training team's checklist to help journalists secure their digital life.Freedom of the Press
https://aliyesha.com/sub/articles/news/display/hp_dalai_lama_departs_south_india_tour
#himachal #dharamshala #india #news #press #dalailama #buddhism #spirituality #winter #health
Enjoy tracker free reading with us. #privacy #privacymatters

Dharamshala: Dalai Lama Departs for South India: Followers Gather at Kangra Airport.
The Buddhist spiritual leader, the Dalai Lama, departed for South India today.Rahul (Aliyesha)
Microsoft is warning of an issue when using a media support to install Windows 11 [version 24H2], that causes the operating system to not accept further security updates.
http://learn.microsoft.com/en-us/windows/release-health/status-windows-11-24h2#issues-might-occur-with-media-which-installs-the-october-or-november-update
#microsoft #windows #update #failures #it #security #privacy #engineer #media #tech #news
Windows 11, version 24H2 known issues and notifications
View announcements and review known issues and fixes for Windows 11, version 24H2learn.microsoft.com
Follow updates across the web in a feed that only you control, even if the site does not offer an RSS feed
Open RSS offers feeds that are a much healthier alternative to the intrusive, algorithmic feeds on websites that harm and manipulate us. But several sites, including Tumblr and Craigslist, have removed their RSS feeds, so that you are forced into their algorithms and tracking.
This is annoying if you want to follow things without creating an account, the way you can with Bluesky and all the various Fediverse sites.
Instead of manually checking individual websites for updates, you can automatically get updates through a website’s RSS feed using an RSS Reader app. This allows you to build a single collection of updates across the web in a single feed, that only you control.
OpenRSS offers feeds for more than the apps listed on their feeds page. You can find others by adding the URL openrss.org to the beginning of any website on the web—if OpenRSS offers a feed for the site, it gives it to you (and if not, you’ll see a page explaining that).
To follow any site that does not have an RSS feeds, go to the site where you’d view the news, or the social profile where posts are shown, and then prepend
openrss.org/ to the beginning of the URL. For example my blog is at https://gadgeteer.co.za/blog, you’d then enter it as https://openrss.org/ gadgeteer.co.za/blog. The advantage here is that the OpenRSS service will even clean up and correct some errors for existing RSS feeds.Their site also directs you to some excellent RSS reader apps to use, with a table comparing their key features. But in many cases, quite a few browsers also have built in RSS reader capabilities such as Brave, Edge and Firefox I recall. Fluent Reader is an exceptional desktop app for RSS feeds too.
The whole point is that RSS is an open standard, so anyone can support and use it. This is why many closed corporations want to prevent their users from using RSS. They lose the ability to track you, push adverts, apply their algorithm, etc. It is also probably why Google shut down their RSS reader service. But RSS is everywhere, and gaining some ability to read RSS for sites that have disabled their RSS, is empowering for individuals.
See https://openrss.org/category/uncategorized/feed
#Blog, #adverts, #privacy, #RSS, #technology
The development was first reported by Reuters.
The settlement applies to U.S.-based individuals current or former owners or purchasers of a Siri-enabled device who had their confidential voice communications with the assistant "obtained by Apple and/or were shared with third-parties as a result of an unintended Siri activation" between September 17, 2014, and December 31, 2024.
Eligible individuals can submit claims for up to five Siri devices – iPhone, iPad, Apple Watch, MacBook, iMac, HomePod, iPod touch, or Apple TV – on which they claim to have experienced an accidental Siri activation during a conversation intended to be confidential or private. Class members who submit valid claims can receive $20 per device."
https://thehackernews.com/2025/01/apple-to-pay-siri-users-20-per-device.html
#Apple #Siri #Privacy #USA #DataProtection
https://www.engadget.com/social-media/telegram-introduces-third-party-verification-and-new-search-filters-140013424.html?src=rss
#TELEGRAM #PRIVACY #KEWLNEWS #PRESS
Telegram introduces third-party verification and new search filters
Telegram has introduced a new third-party account verification system as part of its latest app update.Steve Dent (Engadget)
https://www.theverge.com/2025/1/2/24334268/apple-siri-recording-privacy-lawsuit-settlement-proposed
#APPLE #PRIVACY #SIRI #KEWLNEWS #PRESS

Apple will pay $95 million to people who were spied on by Siri
Apple and plaintiffs have agreed on a $95 million settlement in a lawsuit over whether it violated privacy laws by recording conversations with Siri.Adi Robertson (The Verge)
https://aliyesha.com/sub/articles/news/display/bh_patna_protest_exam_bpsc_2025
#bihar #patna #india #news #press #government #governance #youth #jobs #employment #exam #examination #protest #corruption #BPSC #BPSC2025 #CPIML #AIPF
Enjoy tracker free reading with us. #privacy #privacymatters

Patna: Citizens Protest Against Repression of BPSC Aspirants, calls for immediate action.
Patna witnessed a strong protest today as civil society condemned the alleged repression faced by Bihar Public Service Commission (BPSC) aspirants.Alok Sharma (Aliyesha)
A attack campaign has compromised at least 16 Chrome browser extensions, exposing over 600k users to data & credential theft. This targeted extension publishers through phishing emails that mimicked official communications from the Chrome Web Store.
https://www.cyberhaven.com/blog/cyberhavens-chrome-extension-security-incident-and-what-were-doing-about-it
#google #chrome #it #security #privacy #engineer #media #tech #news
Cyberhaven’s Chrome extension security incident and what we’re doing about it
Our team has confirmed a malicious cyberattack that occurred on Christmas Eve, affecting Cyberhaven's Chrome extension.www.cyberhaven.com

Aplicativos de préstamos kenianos invaden la privacidad de los prestatarios para cobrar deudas
Un informe del Centro de Derecho de Propiedad Intelectual y Tecnologías de la Información (CIPIT) de la Universidad de Strathmore revela que la mayoría de los aplicativos de préstamo recopilan muchos más datos de los necesarios.Global Voices en Español
https://aliyesha.com/sub/articles/news/display/uk_new_year_voter_registration_count_2025
#uttarakhand #dehradun #india #news #press #elections #voter #voting #registration #VoterRegistration
Enjoy tracker free reading with us. #privacy #privacymatters

देहरादून: नए साल में उत्तराखंड के 1,23,250 नए मतदाता होंगे वोटर लिस्ट में शामिल।
5 साल में लगभग 11 लाख नाम मतदाता सूची में शामिल।प्रेम पंचोली (Aliyesha)

Vorratsdatenspeicherung: Eine zweifache Farce
Nach dem Anschlag auf den Magdeburger Weihnachtsmarkt will Rot-Grün die Vorratsdatenspeicherung einführen. Mit evidenzbasierter Sicherheitspolitik hat das nichts zu tun.netzpolitik.org
Our best hope for protection is that legislators in Massachusetts and other states who are concerned about these risks take steps now to upgrade their privacy laws."
https://teachprivacy.com/privacy-in-authoritarian-times/
#Privacy #CyberSecurity #Surveillance #Authoritarianism #DataProtection

Privacy in Authoritarian Times - TeachPrivacy
I just published an op-ed in the Boston Globe entitled "States can fight authoritarianism by shoring up privacy laws." Boston Globe (Dec. 23, 2024). It'sDaniel Solove (TeachPrivacy)
Terabytes of Volkswagen customer details in Amazon cloud storage remained unprotected for months, allowing anyone with little technical knowledge to track drivers movement or gather personal information.
https://www.ccc.de/de/updates/2024/wir-wissen-wo-dein-auto-steht
#volkswagen #electric #car #amazon #cloud #cariad #exposed #data #it #security #privacy #engineer #ccc #media #technology #38c3 #news
Why not choose #privacy over Big Tech⁉️
Here are some ideas. 👇 Which is on your list for #2025❓
And more tips to #deGoogle your life: https://tuta.com/blog/how-to-leave-google-gmail
How to De-Google your life: The ultimate list of best private Google alternatives. | Tuta
Start DeGoogling today and prevent Big G from exploiting your data! Learn how to replace Google apps with private ones in this detailed guide.Tuta
Perhaps the single most exciting media hit for EFF in 2024 was “Secrets in Your Data,” the NOVA PBS documentary episode exploring “what happens to all the data we’re shedding and explores the latest efforts to maximize benefits – without compromising personal privacy.” EFFers Hayley Tsukayama, Eva Galperin, and Cory Doctorow were among those interviewed."
https://www.eff.org/deeplinks/2024/12/eff-press-2024-review
#DigitalRights #USA #Privacy #DigitalActivism
From my own perspective, computing privacy is simple: if something happens entirely on my computer, then it's private, whereas if my computer sends data to the manufacturer of the computer, then it's not private, or at least not entirely private. Thus, the only way to guarantee computing privacy is to not send data off the device.
I don't understand most of the technical details of Apple's blog post. I have no way to personally evaluate the soundness of Apple's implementation of Enhanced Visual Search. One thing I do know, however, is that Apple computers are constantly full of privacy and security vulnerabilities, as proved by Apple's own security release notes. You don't even have to hypothesize lies, conspiracies, or malicious intentions on the part of Apple to be suspicious of their privacy claims. A software bug would be sufficient to make users vulnerable, and Apple can't guarantee that their software includes no bugs. (To the contrary, Apple's QA nowadays is atrocious.)
It ought to be up to the individual user to decide their own tolerance for the risk of privacy violations. In this specific case, I have no tolerance for risk, because I simply have no interest in the Enhanced Visual Search feature, even if it happened to work flawlessly. There's no benefit to outweigh the risk. By enabling the "feature" without asking, Apple disrespects users and their preferences. I never wanted my iPhone to phone home to Apple.
Remember this advertisement? "What happens on your iPhone, stays on your iPhone.""
https://lapcatsoftware.com/articles/2024/12/3.html
#Apple #ApplePhotos #Privacy #DataProtection #Encryption #iOS #iPhone





![[ImageSource: ShadowServer]
The map shows IMAP and POP3 mail servers without TLS.
Over three million POP3 and IMAP mail servers without TLS encryption are currently exposed on the Internet and vulnerable to network sniffing attacks. Almost 900,000 are based in the U.S., another 560,000 and 380,000 in Germany and Poland, the organization found and adding: “We see around 3.3M such cases with POP3 & a similar amount with IMAP (most overlap). It's time to retire those!” You can check out vulnerability reports for both POP3 email servers and IMAP email hosts on the Shadowserver Foundation site.
IMAP and POP3 are two methods for accessing email on mail servers. IMAP is recommended for checking emails from multiple devices, such as phones and laptops because it keeps your messages on the server and synchronizes them between devices. POP3, on the other hand, downloads emails from the server, making them accessible only from the device where they were downloaded.
The TLS secure communication protocol helps secure users information while exchanging and accessing their emails over the Internet through client/server applications. However, when TLS encryption is not enabled, their messages contents and credentials are sent in clear text, exposing them to eavesdropping network sniffing attacks.
ShadowServer advised all email users to check with their email service provider to be sure that TLS is enabled and the latest version of the protocol is being used. [ImageSource: ShadowServer]
The map shows IMAP and POP3 mail servers without TLS.
Over three million POP3 and IMAP mail servers without TLS encryption are currently exposed on the Internet and vulnerable to network sniffing attacks. Almost 900,000 are based in the U.S., another 560,000 and 380,000 in Germany and Poland, the organization found and adding: “We see around 3.3M such cases with POP3 & a similar amount with IMAP (most overlap). It's time to retire those!” You can check out vulnerability reports for both POP3 email servers and IMAP email hosts on the Shadowserver Foundation site.
IMAP and POP3 are two methods for accessing email on mail servers. IMAP is recommended for checking emails from multiple devices, such as phones and laptops because it keeps your messages on the server and synchronizes them between devices. POP3, on the other hand, downloads emails from the server, making them accessible only from the device where they were downloaded.
The TLS secure communication protocol helps secure users information while exchanging and accessing their emails over the Internet through client/server applications. However, when TLS encryption is not enabled, their messages contents and credentials are sent in clear text, exposing them to eavesdropping network sniffing attacks.
ShadowServer advised all email users to check with their email service provider to be sure that TLS is enabled and the latest version of the protocol is being used.](https://friendica-leipzig.de/photo/preview/600/416546)





![Volkswagen’s automotive software company [Cariad], exposed data collected from around 800,000 electric cars. The info could be linked to drivers names and reveal precise vehicle locations [for some of them being as precise as a few centimeters]. The exposed databases include details for VW, Seat, Audi and Skoda vehicles.
Cariad was informed on November 26 of the issue by the Chaos Computer Club (CCC), the largest organization of ethical hackers in Europe that for more than 30 years has promoted security, privacy, and free access to information.
<https://www.ccc.de/en/>
Access to the car data was possible due to Cariad’s incorrect configuration in two IT applications, a company representative said.
The CCC hackers could access the data only after bypassing several security mechanisms that required significant time and technical expertise. Additionally, because individual vehicle data was pseudonymized for privacy purposes, the CCC hackers had to combine different data sets to associate the details with a particular user. Volkswagen’s automotive software company [Cariad], exposed data collected from around 800,000 electric cars. The info could be linked to drivers names and reveal precise vehicle locations [for some of them being as precise as a few centimeters]. The exposed databases include details for VW, Seat, Audi and Skoda vehicles.
Cariad was informed on November 26 of the issue by the Chaos Computer Club (CCC), the largest organization of ethical hackers in Europe that for more than 30 years has promoted security, privacy, and free access to information.
<https://www.ccc.de/en/>
Access to the car data was possible due to Cariad’s incorrect configuration in two IT applications, a company representative said.
The CCC hackers could access the data only after bypassing several security mechanisms that required significant time and technical expertise. Additionally, because individual vehicle data was pseudonymized for privacy purposes, the CCC hackers had to combine different data sets to associate the details with a particular user.](https://friendica-leipzig.de/photo/preview/1024/394468)


