Suche
Beiträge, die mit CYBERSECURITY getaggt sind
Read more here: https://www.techradar.com/vpn/vpn-services/independent-auditors-confirm-mullvad-vpn-as-secure

Independent auditors confirm Mullvad VPN as secure
This is the fourth time the VPN provider put its software under third-party scrutinyChiara Castro (TechRadar pro)

Ransomware defenses are being weakened by outdated backup technology, limited backup data encryption, and failed data backups
Immutable storage solutions recommended to boost cybersecurityEfosa Udinmwen (TechRadar pro)
💡 Try My Idea: USBSTICK "Pull The Plug" Bracelet (ideal for Tails)
This idea allows you to attach yourself to the inserted Tails disk, by bracelet (on demand)
If your arm ever gets too far from the computer: *POOF* there goes forensics! 😁
#HumanRights #Journalism #Tails #Linux #privacy #forensics #ideas #tech #GNU #fun #bracelet #jewelry #RAM #coldbootattack #infosec #cybersecurity #TorProject
https://tube.tchncs.de/w/q2Vdv11aTrmgAjKrrAULw2

Tails Amnesiac "Pull The Plug" Coldboot Protection Bracelet
Today sharing my new tails on bracelet concept / idea with everyone - Tails on bracelet I call the "RightToPrivacy Pull The Plug Tails Bracelet". My idea for wearing Tails usbstick detachable brace...tchncs
And many details about the hack — when it happened, who was impacted, the extent of the damage — are slowly emerging and are still not totally clear, making it difficult for the layperson to follow.
But Beijing is taking notes on the sluggish U.S. response. At the one Senate Commerce hearing on the topic held Wednesday, JAMES LEWIS, director of the Strategic Technologies Program at the Center for Strategic and International Studies, testified about the need for the U.S. to counter Chinese hacking operations by giving Beijing a taste of its own medicine through U.S. offensive hacking. Otherwise, he warned, China would just keep going."
https://www.politico.com/newsletters/national-security-daily/2024/12/12/we-need-to-talk-about-salt-typhoon-00183727
#CyberSecurity #China #USA #SaltTyphoon #StateHacking
https://www.bleepingcomputer.com/news/security/new-iocontrol-malware-used-in-critical-infrastructure-attacks/
#cybersecurity #IoT #SCADA #Israel #US
https://www.securityweek.com/iranian-hackers-use-iocontrol-malware-to-target-ot-iot-devices-in-us-israel/
#Infosec #Security #Cybersecurity #CeptBiro #IranianHackers #IOCONTROL #Malware #OT #IoTDevices #US #Israel

What is phishing and how dangerous is it?
This is a threat that should not be underestimated.Darren Allan (TechRadar pro)

This devious new malware technique looks to hijack Windows itself to avoid detection
There is a way to abuse accessibility features on Windows to hide malwareSead Fadilpašić (TechRadar pro)
About 50 cyber attacks
 motivated by geopolitics were recorded each day in India during 2024.
motivated by geopolitics were recorded each day in India during 2024.https://timesofindia.indiatimes.com/city/hyderabad/pro-palestine-hacktivist-groups-target-india-amid-gaza-conflict/articleshow/116184519.cms
#palestine #gaza #hamas #israel #cyberattack #cybersecurity #terrorism #india #news #war

Gaza war: Why pro-Palestine hacktivists are targeting India
In the wake of the Israel-Hamas war, India has faced a wave of cyberattacks from pro-Palestine hacktivist groups, testing the country's cybersecurity measures and prompting retaliatory actions from Indian hackers.Amrita Didyala (Times Of India)
1960s edition here: https://auntieimperial.tumblr.com/post/147731249619 (includes the complete secret plan to levitate the pentagon ...😎)
"I spend a nontrivial amount of time wondering if spies spend a much time juggling .csv spreadsheets as marketing people do." #Altoona #unitedhealthcare #DeadCEOGoodCEO #CyberSec #CyberSecurity #CyberStalking
Anarchic Tendencies
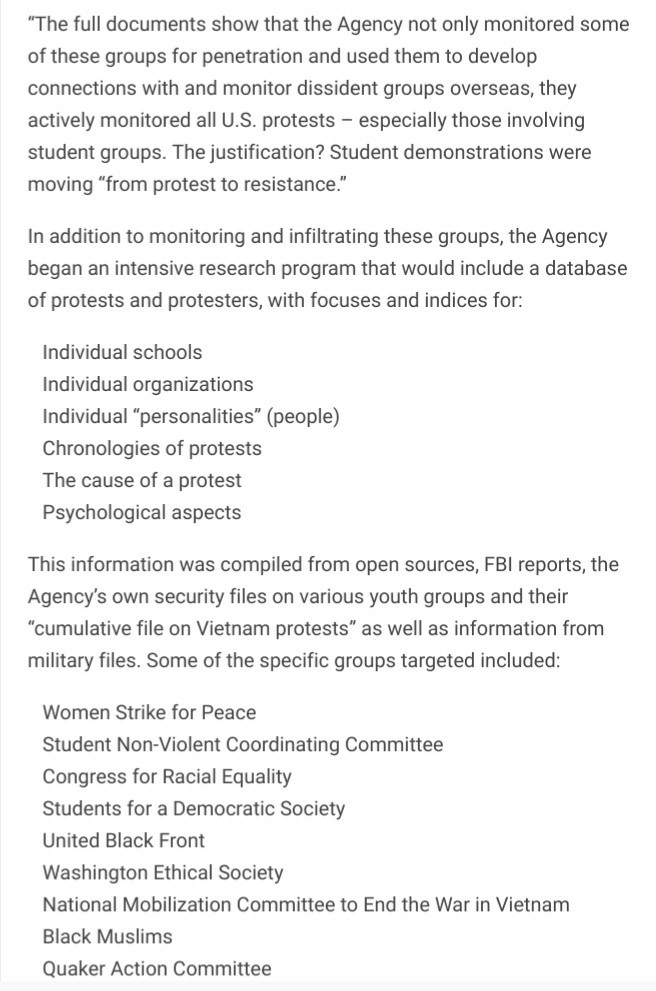
"The full documents show that the Agency not only monitored some of these groups for penetration and used them to develop connections with and monitor dissident groups overseas, they actively...auntieimperial (Tumblr)
These companies include CyberArk, Crowdstrike, CyberReason, Noname Security, Claroty, Cato Networks, Zero Networks, etc. There are a lot. What will you do about it?
#gaza #genocide
The list goes on.
But now there’s rising interest in hacking other kinds of devices people use, like Wi-Fi-connected security cameras and other IoT products.
Toka, an Israeli startup backed by Andreessen Horowitz, specializes in this type of work. It previously gained attention for a 2022 Haaretz article detailing its claims about being able to obtain and even delete security camera footage.
The company is now looking to hire a “Client Director USA” to “support new business growth within the US government market.” The position requires a “strong history of technology sales within DoD and national security agencies.”"
https://techcrunch.com/2024/12/06/a16z-backed-toka-wants-to-help-us-agencies-hack-into-security-cameras-and-other-iot-devices/
#USA #Surveillance #PoliceState #StateHacking #Hacking #CyberSecurity #IoT

a16z-backed Toka wants to help US agencies hack into security cameras and other IoT devices | TechCrunch
An Israeli startup specializing in penetrating IoT devices says it's hiring to "support new business growth" in the US government market.Charles Rollet (TechCrunch)
- He describes being subjected to beatings and an intense effort to recruit him as an informant for the Russian Federal Security Service (FSB).
- Our analysis finds that the spyware placed on his device allows the operator to track a target device’s location, record phone calls, keystrokes, and read messages from encrypted messaging apps, among other capabilities.
- The spyware bears many similarities to the Monokle family of spyware, previously reported on by Lookout Mobile Security, which they attribute to the “Special Technology Center,” a contractor to the Russian government.
- Our analysis also finds certain differences from previously-reported samples of Monokle spyware, suggesting that it is either an updated version of Monokle or new software created by reusing much of the same code."
https://citizenlab.ca/2024/12/device-confiscated-by-russian-authorities-returned-with-monokle-type-spyware-installed/
#CyberSecurity #Russia #Spyware #Monokle

Something to Remember Us By: Device Confiscated by Russian Authorities Returned with Monokle-Type Spyware
In a joint investigation with The First Department, The Citizen Lab uncovered spyware covertly implanted on the phone of a Russian programmer following his release from Russian custody.Cooper Quintin (The Citizen Lab)
https://arstechnica.com/security/2024/12/1-phone-scanner-finds-seven-pegasus-spyware-infections/
#CyberSecurity #Spyware #iVerify #iOS #Android #Pegasus

$1 phone scanner finds seven Pegasus spyware infections
iVerify’s detection tool was launched in May and is turning up victims.WIRED (Ars Technica)
Email services such as Gmail and Outlook generally offer encryption in transit, which means they can be read on the companies’ servers and by the end users. Messages that are encrypted in transit can’t be nabbed from a telecom network in an accessible format, but they could be accessed through an email service provider or a law enforcement request to that company.
End-to-end encryption—the kind offered by services like WhatsApp and Signal—is considered the best bet for privacy, particularly when paired with the option to auto-delete messages after a set period of time, says Mullin."
https://www.inc.com/jennifer-conrad/why-you-should-start-using-encrypted-communications-today/91034632
#CyberSecurity #Privacy #Encryption #E2EEncryption #Signal
While journalists, human rights defenders, lawmakers, and political officials are frequent targets of state surveillance, reports of spyware compromising the phones of business leaders are rare, but not unheard of. The findings come as a fresh warning that spyware typically used by governments under the guise of preventing serious crime and terrorism can also be misused for commercial espionage.
In a call with TechCrunch this week, iVerify chief executive Rocky Cole declined to name who was targeted, but said that the spyware targeted a business “that you’ve heard about.” Cole, a former analyst at the National Security Agency, said the business leader, who iVerify is in contact with, was “completely surprised” by the attempt to compromise their phone."
https://techcrunch.com/2024/12/04/business-leaders-among-pegasus-spyware-victims-says-security-firm/
#CyberSecurity #NSOGroup #Spyware #Pegasus #iPhone

Business leaders among Pegasus spyware victims, says security firm | TechCrunch
The mobile security company said it detected Pegasus spyware attacks on seven iPhone owners, including government officials and a business leader.Zack Whittaker (TechCrunch)
Make a transition to memory safety part of your #CyberCivilDefense plan.
Read about orgs doing that today: https://www.memorysafety.org/blog/rustls-adoption-grows/

Security-Sensitive Industries Move to Memory Safety
Prossimo has been investing in the memory safe, high performance TLS library called Rustls for nearly four years. During that time, we've seen Rustls improve and we've seen growing adoption. Organizations like 1Password, Google Fuschia, and Fly.www.memorysafety.org
https://defensemirror.com/news/38303/Argentina__Israel_Plan_Defense_Collaboration_on_UAVs__Small_Arms…
#Argentina #Israel #UAV #smallarms #ammunition #cybersecurity #drone #loiteringmunition #satcom #borderprotection #ammo #cyberdefense
https://defensemirror.com/news/38303/Argentina__Israel_Plan_Defense_Collaboration_on_UAVs__Small_Arms…
#Argentina #Israel #UAV #smallarms #ammunition #cybersecurity #drone #loiteringmunition #satcom #borderprotection #ammo #cyberdefense
https://blog.thenewoil.org/cybersecurity-101-a-guide-to-staying-safe-online
#blog

Cybersecurity 101: A Guide to Staying Safe Online
Today is Computer Security Day. While not a high profile holiday, I of course can’t miss the opportunity to bring it up because in our in...The New Oil
https://www.bleepingcomputer.com/news/security/hackers-exploit-projectsend-flaw-to-backdoor-exposed-servers/
#cybersecurity
As the memo says, “AI has emerged as an era-defining technology and has demonstrated significant and growing relevance to national security. The United States must lead the world in the responsible application of AI to appropriate national security functions.” As the US national security state attempts to leverage powerful commercial AI to give it an edge, there are a number of questions that remain unanswered about how much that ever-tightening relationship will impact much needed transparency and accountability for private AI and for-profit automated decision making systems."
https://www.eff.org/deeplinks/2024/11/us-national-security-state-here-make-ai-even-less-transparent-and-accountable
#USA #CyberSecurity #Surveillance #AI #AlgorithmicTransparency

The U.S. National Security State is Here to Make AI Even Less Transparent and Accountable
As the US national security state attempts to leverage powerful commercial AI to give it an edge, there are a number of questions that remain unanswered about how much that ever-tightening relationship will impact much needed transparency and account…Electronic Frontier Foundation
(...)
As for the targets, the Post reports fewer than 150 people have been identified as having their text messages or phone calls monitored and the FBI has been in contact with them. Most of the people are in the Washington DC area, which makes sense if the hackers were interested in political targets. But 150 people can communicate with a lot of people, even in a short period, so the number of targets could be in the “millions,” according to Warner. You get the sense U.S. authorities have no real idea how many people have been impacted, given the scope of the intrusion.
The details about how the hackers were able to push so deeply into U.S. systems are still scarce, but it has something to do with the ways in which U.S. authorities wiretap suspects in this country with a court order. The monitoring of phone calls wasn’t 24/7, according to Warner, but he didn’t seem to elaborate on what that meant to the Times."
https://gizmodo.com/china-wiretaps-americans-in-worst-hack-in-our-nations-history-2000528424
#USA #CyberSecurity #StateHacking #Surveillance #PoliceState #China

China Wiretaps Americans in 'Worst Hack in Our Nation's History'
America's aging infrastructure seems to be the culprit.Matt Novak (Gizmodo)
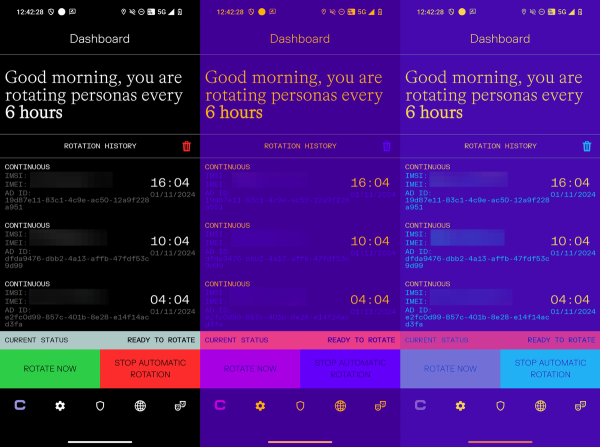
Cape lets users create bundles of these identifiers, called “personas,” then cycle through them at different points. This means that during some attacks, a Cape phone may look like a different phone each time. The device can do this in a few ways. In the first, users can set geofences around a particular area, meaning that when they enter that location—such as their home, place of work, or commute—the device automatically switches to a particular IMSI, IMEI, and MAID. Secondly, users can set it to switch between these sets of identifiers after an approximate period of time has passed, between one hour and one day, with an option to add some percentage of variation between each rotation."
https://www.404media.co/i-dont-own-a-cellphone-can-this-privacy-focused-network-change-that/
#CyberSecurity #Mobile #Privacy #Cellphones #MobileSecurity #Cape
I Don't Own a Cellphone. Can This Privacy-Focused Network Change That?
A small tech company called Cape has been selling a privacy-focused cellphone service to the U.S. military. Now Cape will be offering its product to high-risk members of the public.Joseph Cox (404 Media)
#cybersecurity #Israel #Palestine #USA #Ukraine https://t.co/P4SF5aRycq
https://twitter.com/Cyberknow20/status/1859547448248762400
#CyberKnow #cysec
#cybersecurity #Israel #Palestine https://t.co/EFEeXymtm5
https://twitter.com/Cyberknow20/status/1859544430572921051
#CyberKnow #cysec
#cybersecurity #infosec #incident #databreach
https://beyondmachines.net/event_details/the-us-library-of-congress-reports-breach-of-email-communications-r-3-3-c-6/gD2P6Ple2L
#cybersecurity #infosec #incident #databreach
https://beyondmachines.net/event_details/ransomhub-gang-claims-breach-of-mexican-government-s-official-federal-website-m-3-n-k-0/gD2P6Ple2L
https://www.propublica.org/article/microsoft-solarwinds-golden-saml-data-breach-russian-hackers
#Tech #News #Cybersecurity #Hacking #Data #Technology
On Wednesday, the Barcelona-based human rights nonprofit Iridia announced that it had filed a complaint in a Catalan court earlier this week accusing NSO’s founders Omri Lavie and Shalev Hulio, as well as Yuval Somekh, an executive of two affiliate companies, of hacking crimes.
Iridia represents lawyer Andreu Van den Eynde, an attorney and university professor who specializes in cybersecurity. According to a 2022 investigation by Citizen Lab, a nonprofit that has been investigating government spyware for more than a decade, Van den Eynde was among the victims of a wide-ranging hacking campaign against at least 65 Catalans linked to the region’s attempts to become independent from Spain, which was carried out using NSO’s Pegasus software. Amnesty International independently confirmed Citizen Lab’s findings."
https://techcrunch.com/2024/11/13/lawyer-allegedly-hacked-with-spyware-names-nso-founders-in-lawsuit/
#CyberSecurity #NSOGroup #Pegasus #Spyware #Spain #Hacking

Lawyer allegedly hacked with spyware names NSO founders in lawsuit | TechCrunch
Spanish lawyer Andreu Van den Eynde is suing NSO Group and its founders Omri Lavie and Shalev Hulio, accusing them of illegal hacking.Lorenzo Franceschi-Bicchierai (TechCrunch)
#Palestine #hack #Israel #dataleak #CyberSecurity
https://cnews.link/israel-ministry-national-security-alleged-breach-1/
The data includes the employees’ name, work contact information, and what location they work at, and has more than 2.8 million lines of data, according to the post on Breach Forums. The post says the source of the data was MOVEit, which is suite of cloud data management tools.
“Amazon and AWS systems remain secure, and we have not experienced a security event. We were notified about [a] security event at one of our property management vendors that impacted several of its customers including Amazon. The only Amazon information involved was employee work contact information, for example work email addresses, desk phone numbers, and building locations,” an Amazon spokesperson told 404 Media in an email."
https://www.404media.co/amazon-confirms-breach-of-employee-data/
#Amazon #DataBreach #DataProtection #Privacy #Hacking #CyberSecurity

Amazon Confirms Breach of Employee Data
The breach includes the employees’ name, work contact information, and what location they work at.Joseph Cox (404 Media)
#northkorea #flashdrivesforfreedom #tech #linux #media #follow #boost #social #mastodon #peace #help #donate #cybersecurity #trending #freedom
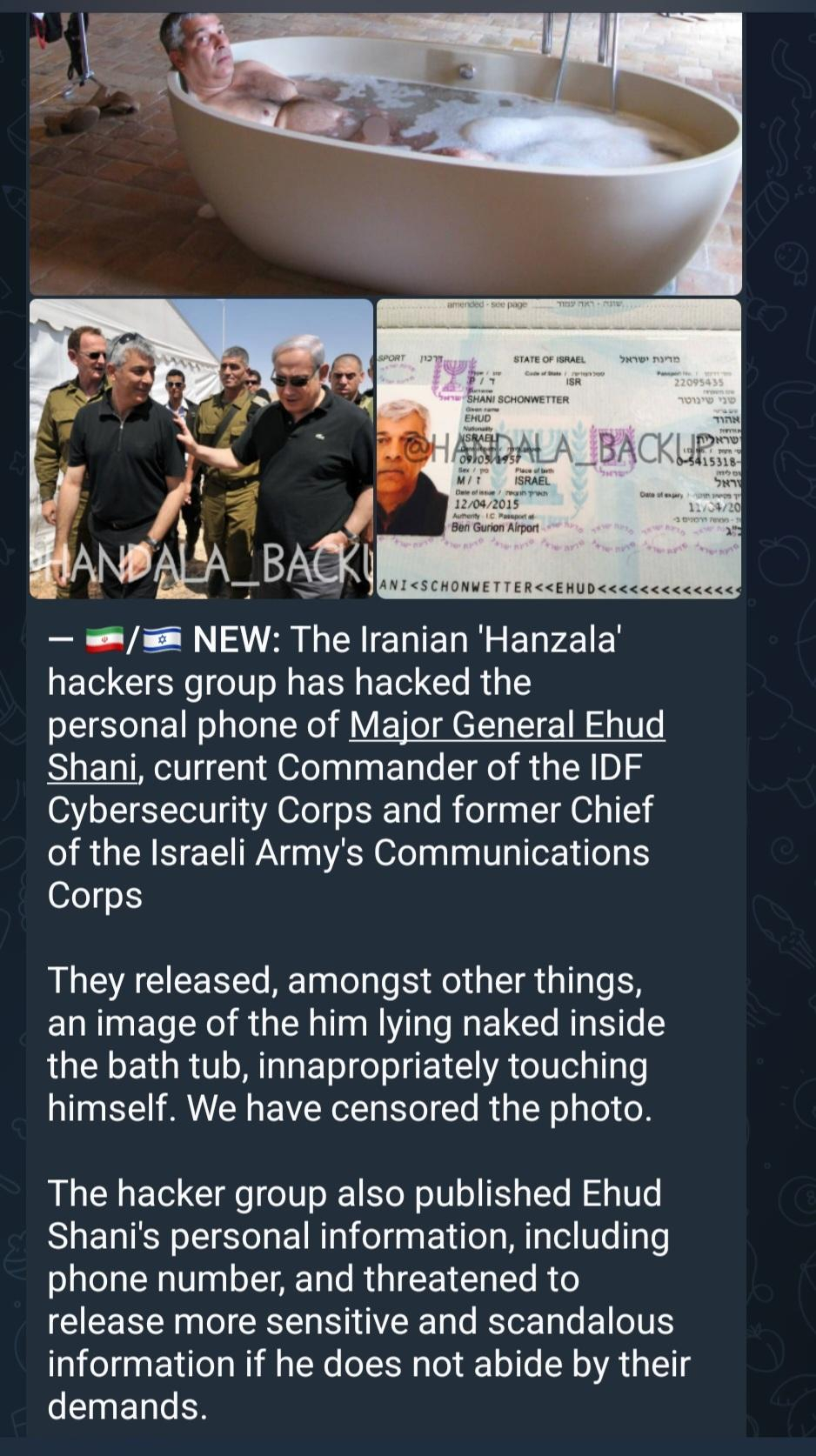
The #Iranian #Hanzala #hackers group has #hacked the personal phone of Major General Ehud Shani, current Commander of the #IDF #Cybersecurity Corps and former Chief of the #Israeli Army's Communications Corps
They released, amongst other things, an image of the him lying naked inside the bath tub, innapropriately touching himself. We have censored the photo.
The hacker group also published Ehud Shani's personal information, including phone number, and threatened to release more sensitive and scandalous information if he does not abide by their demands.
From the Middle_East_Spectator channel on Telegram.
#ThankYouHacktivists
#Terrorist
#FreePalestine
#IsraelIsATerroristState
#IsraelWarCrimes
#RacistIsrael
#IsraelRogueState
#ArmsEmbargoOnIsrael
#USAFundsGenocide
#BoycottIsrael
#BDSMovement
#BoycottIsraeliApartheid
#StopGenocide
#ApartheidIsrael
#SanctionIsrael
#ExposeIsraeliTerrorists
#ZionismIsACult
#FAFO