Suche
Beiträge, die mit SECURITY getaggt sind
Microsoft-Ersatzteile für Xbox + Klage gegen Traktorhersteller + Digitale Souveränität gefordert + IT-Sicherheit für Klinken + DJI ohne Geofencing + #heiseshow
https://www.heise.de/news/Donnerstag-Recht-auf-Reparatur-von-Xbox-Konsolen-und-John-Deere-Landmaschinen-10244540.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Bitkom #DonaldTrump #Drohnen #EU #Gesundheit #hoDaily #Landwirtschaft #Microsoft #Reparatur #Security #Xbox #news

Donnerstag: Recht auf Reparatur von Xbox-Konsolen und John-Deere-Landmaschinen
Microsoft-Ersatzteile für Xbox + Klage gegen Traktorhersteller + Digitale Souveränität gefordert + IT-Sicherheit für Klinken + DJI ohne Geofencing + #heiseshowFrank Schräer (heise online)
Greenland should decide on its own independence – POLITICO
The Danish premier said last week that she had requested to speak to Trump but hadn’t yet heard back. At the time, she assured there was “no reason to believe” Trump actually plans to invade Greenland.BYTESEU (Bytes Europe)
Greenland should decide on its own independence – POLITICO - EUROPE SAYS
The Danish premier said last week that she had requested to speak to Trump but hadn’t yet heardEUROPE SAYS (EUROPESAYS.COM)

Denmark tells Trump Greenland should decide on its own independence
The Danish PM and incoming U.S. president had a 45-minute phone call on Wednesday.Giselle Ruhiyyih Ewing (POLITICO)
Verstärkte Prävention und rasche Reaktion auf Attacken stehen im Zentrum eines EU-Plans für IT-Sicherheit von Krankenhäusern und Gesundheitsdienstleistern.
https://www.heise.de/news/IT-Attacken-So-will-die-EU-Kommission-den-Gesundheitssektor-besser-schuetzen-10244385.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#EU #Gesundheit #Security #KRITIS #Medizin #Ransomware #news
#infosec #security #linux #unix
Ein kürzliches Datenleck bei Gravy Analytics gab erste Hinweise, nun ist klar: mehr als 40.000 Apps sammeln Positionsdaten.
https://www.heise.de/news/Standort-Tracking-weit-verbreitet-Mehr-als-40-000-Apps-sammeln-Positionsdaten-10243629.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Datenschutz #DSGVO #Security #news
Changelog
- CalyxOS 6.3.0
- Android 15, January 2025 Security update
- Chromium: 131.0.6778.260
- Update all included apps
You can read more about it here:
Link: https://calyxos.org/news/2025/01/08/15-january-security-update/
#Android
This voice phishing gang calls the actual Apple customer support phone number 800-275-2273 and tricks that system into sending the alert below to your phone.
A great read, feels like a hole in Apple's security, no?
https://krebsonsecurity.com/2025/01/a-day-in-the-life-of-a-prolific-voice-phishing-crew/Applee #Security
My short (uninformed) take: Passkeys have great potential, but the implementation is often flawed.
If you care about passwords vs passkeys, this is an interesting read, filled with useful links.
https://mjtsai.com/blog/2025/01/10/passkey-usability/
Apple #Security
As scans from the IT-security threat monitoring platform Shadowserver show, 3.3 million hosts are running POP3/IMAP services without TLS encryption enabled and expose usernames & passwords in plain text when transmitted over the Internet.
https://www.shadowserver.org/what-we-do/network-reporting/vulnerable-pop3-report/
#pop3 #imap #mailservers #exposed #sniffing #tls #it #security #privacy #engineer #media #tech #news
HIGH: Vulnerable POP3 Report | The Shadowserver Foundation
This report identifies hosts that have a POP3 service running on port 110/TCP or 995/TCP without TLS support. This means that passwords used for mail access may be intercepted by a network sniffer.www.shadowserver.org
Don’t panic about Trump’s refusal to rule out Greenland invasion, Denmark says – POLITICO - EUROPE SAYS
Trump declared Tuesday he would not exclude using economic or military coercion to gain control of Greenland, aEUROPE SAYS (EUROPESAYS.COM)
‘Protect Our People’: Armed Syrian Volunteers Watch Over Damascus
We are offering the following story that has been selected by AFP's chief editors for re-publication as among the best of the week. Pictures by Anwar Amro.BYTESEU (Bytes Europe)
In 2025, Israel’s Gaza Campaign Is Not Over
As the new year begins, Israel will need to find a strategy for the war in Gaza. Several factors are at play in this decision. First, the war has gone on for more than fifteen months since it began with the Hamas attack on Israel on October 7, 2023.BYTESEU (Bytes Europe)
The Future of Iran's Foreign Policy in the Complex Geopolitics of the Post-Assad Middle East - EUROPE SAYS
Iran’s presence in the Middle East has been greatly diminished with the fall of Assad. Now the questionEUROPE SAYS (EUROPESAYS.COM)
One of my goals for 2025 is to publish more regularly on the site, but the catch is I don’t always have things I want to blog about week after week. So, enter the Privacy Roundup.
Note: people who subscribe to the RSS feed and/or the newsletter get it hot off the press usually. 😇
#privacymatters #security #blog
https://avoidthehack.com/privacy-week1-2025
Newsletter, hosted by @buttondown, can be found at: https://buttondown.email/avoidthehack
The RSS feed is at: https://avoidthehack.com/home.rss

Privacy Roundup: Week 1 of Year 2025
Week 1 of 2025 of the Privacy Roundup. This edition includes news items covering: identity documents leaked to the public internet, Apple settling a privacy-related lawsuit concerning Siri, US Treasury hacked by China-connected APTs, and moreAvoid the Hack (avoidthehack!)
Microsoft is warning of an issue when using a media support to install Windows 11 [version 24H2], that causes the operating system to not accept further security updates.
http://learn.microsoft.com/en-us/windows/release-health/status-windows-11-24h2#issues-might-occur-with-media-which-installs-the-october-or-november-update
#microsoft #windows #update #failures #it #security #privacy #engineer #media #tech #news
Windows 11, version 24H2 known issues and notifications
View announcements and review known issues and fixes for Windows 11, version 24H2learn.microsoft.com
A attack campaign has compromised at least 16 Chrome browser extensions, exposing over 600k users to data & credential theft. This targeted extension publishers through phishing emails that mimicked official communications from the Chrome Web Store.
https://www.cyberhaven.com/blog/cyberhavens-chrome-extension-security-incident-and-what-were-doing-about-it
#google #chrome #it #security #privacy #engineer #media #tech #news
Cyberhaven’s Chrome extension security incident and what we’re doing about it
Our team has confirmed a malicious cyberattack that occurred on Christmas Eve, affecting Cyberhaven's Chrome extension.www.cyberhaven.com
The last year, 37C3 covered how a group of hackers discovered code that allegedly bricked public trains in Poland when they went into service at a competitor’s workshop. This year, the same group is back with tales of success, lawsuits and appearances in the Polish Parliament.
https://media.ccc.de/v/38c3-we-ve-not-been-trained-for-this-life-after-the-newag-drm-disclosure
#polish #trains #bricked #it #security #engineer #media #tech #38c3 #news
We've not been trained for this: life after the Newag DRM disclosure
You've probably already heard the story: we got contracted to analyze a bunch of trains breaking down after being serviced by independent...media.ccc.de
The Kurds Are America’s Best Bet In Syria
The fall of Bashar al-Assad’s regime has left a variety of factions fighting for power in Syria. Although none yet presents a clear threat of terrorism to the United States, the lack of stability leaves the country vulnerable to terror groups in the …BYTESEU (Bytes Europe)
Terabytes of Volkswagen customer details in Amazon cloud storage remained unprotected for months, allowing anyone with little technical knowledge to track drivers movement or gather personal information.
https://www.ccc.de/de/updates/2024/wir-wissen-wo-dein-auto-steht
#volkswagen #electric #car #amazon #cloud #cariad #exposed #data #it #security #privacy #engineer #ccc #media #technology #38c3 #news

Moscow may be behind Azerbaijan plane crash, US says
White House cites “early indications” of possible Russian involvement in the crash on Christmas Day.Ketrin Jochecová (POLITICO)
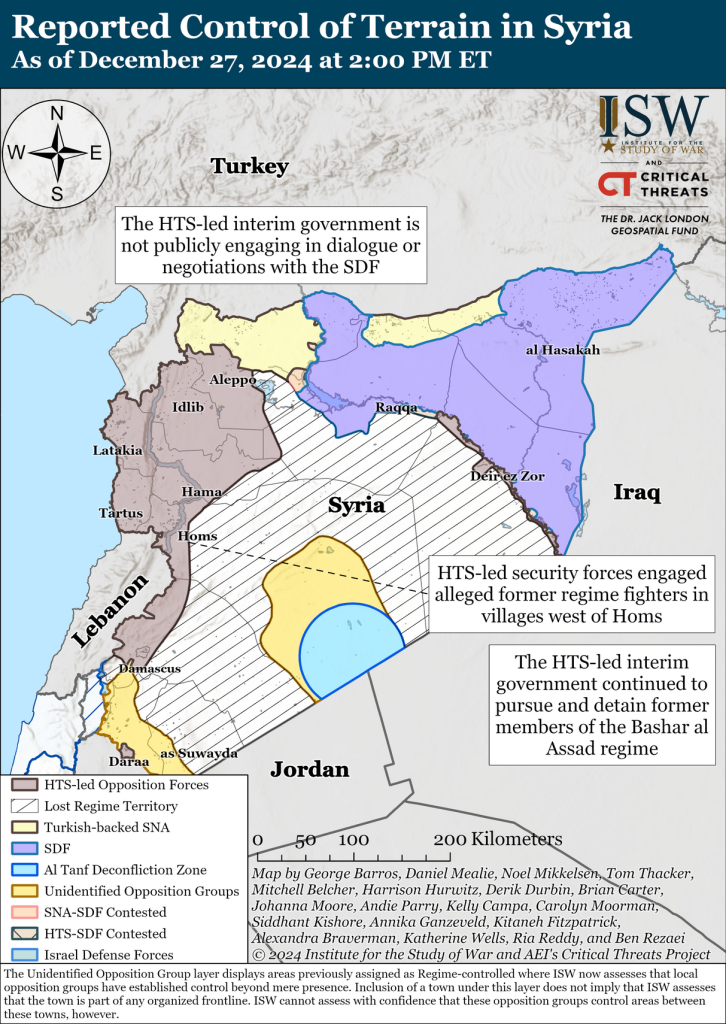
Iran Update, December 27, 2024 - EUROPE SAYS
Iran Update, December 27, 2024 Kelly Campa, Annika Ganzeveld, Carolyn Moorman, Alexandra Braverman, BenEUROPE SAYS (EUROPESAYS.COM)
Magdeburg attack fuels disinformation and mistrust in German leaders – POLITICO
“Federal authorities are turning over every stone,” said German Interior Minister Nancy Faeser of the Social Democratic Party (SPD).BYTESEU (Bytes Europe)
Magdeburg attack fuels disinformation and mistrust in German leaders – POLITICO - EUROPE SAYS
“Federal authorities are turning over every stone,” said German Interior Minister Nancy Faeser of the Social Democratic PartyEUROPE SAYS (EUROPESAYS.COM)
by James Redbanks in UnHerd
“A lot of people assume that somewhere in Britain there are sheds full of food that we’d distribute in a disaster. Surely there is a grain or butter mountain somewhere? Surely the UK govt has a plan for such a crisis?
Nope. No sheds. No stores. No mountains of food. No plan.”
https://unherd.com/2024/12/a-food-apocalypse-is-coming/
#Press #UK #Food #Security #Crisis #Resilience #War #Pandemic #ClimateCrisis #Farming
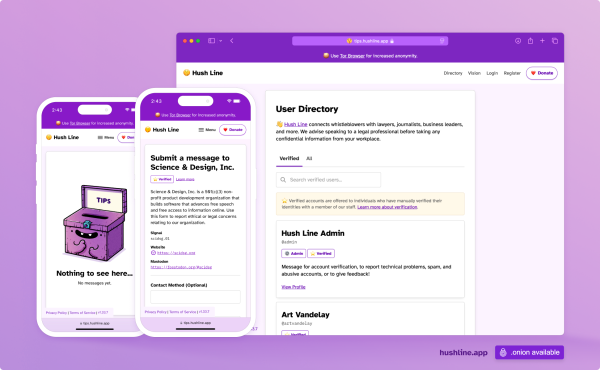
Our tip line platform is free, open-source, anonymous, and end-to-end encrypted. We work seamlessly with @protonprivacy Mail and any webmail when you use @mailvelope.
https://hushline.app
#journalism #business #product #security #privacy #anonymous
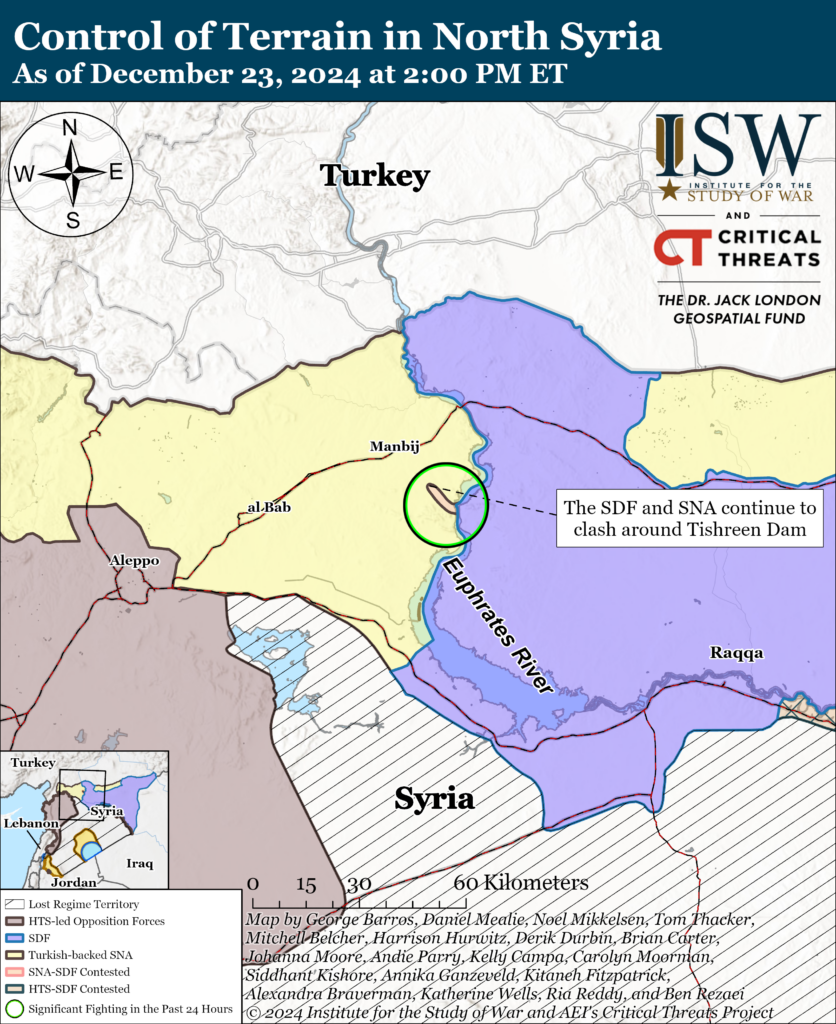
Iran Update, December 23, 2024
Iran Update, December 23, 2024 Johanna Moore, Ria Reddy, Annika Ganzeveld, Kelly Campa, Carolyn Moorman, and Nicholas Carl Information Cutoff: 2:00pm ET The Critical Threats Project (CTP) at the American Enterprise Institute and the Institute for t…BYTESEU (Bytes Europe)
https://www.numerama.com/cyberguerre/1869958-un-cybercriminel-membre-du-celebre-gang-de-hackers-lockbit-se-cachait-en-israel.html
#Infosec #Security #Cybersecurity #CeptBiro #Cybercriminel #Lockbit #Israel

Un cybercriminel membre du célèbre gang de hackers Lockbit se cachait en Israël - Numerama
Un membre du groupe de hackers Lockbit, responsable de cyberattaques contre la France, a été arrêté en Israël. Il était chargé de développer des moyens de pression pour forcer à payer la rançon.Bogdan Bodnar (Numerama)
IT-Security researchers have discovered multiple vulnerabilities in the infotainment units used in some Skoda cars that could allow malicious actors to remotely trigger certain controls and track the car’s location in real time.
https://pcautomotive.com/vulnerabilities-in-skoda-and-volkswagen-vehicles
#skoda #mib3 #vulnerabilities #car #it #security #privacy #engineering #media #tech #news
Vulnerabilities in Skoda and Volkswagen vehicles
Vulnerabilities affecting Skoda and Volkswagen Group vehicles were originally identified in Skoda Superb III (3V3) - 2.0 TDI manufactured in 2022.pcautomotive.com









![[ImageSource: ShadowServer]
The map shows IMAP and POP3 mail servers without TLS.
Over three million POP3 and IMAP mail servers without TLS encryption are currently exposed on the Internet and vulnerable to network sniffing attacks. Almost 900,000 are based in the U.S., another 560,000 and 380,000 in Germany and Poland, the organization found and adding: “We see around 3.3M such cases with POP3 & a similar amount with IMAP (most overlap). It's time to retire those!” You can check out vulnerability reports for both POP3 email servers and IMAP email hosts on the Shadowserver Foundation site.
IMAP and POP3 are two methods for accessing email on mail servers. IMAP is recommended for checking emails from multiple devices, such as phones and laptops because it keeps your messages on the server and synchronizes them between devices. POP3, on the other hand, downloads emails from the server, making them accessible only from the device where they were downloaded.
The TLS secure communication protocol helps secure users information while exchanging and accessing their emails over the Internet through client/server applications. However, when TLS encryption is not enabled, their messages contents and credentials are sent in clear text, exposing them to eavesdropping network sniffing attacks.
ShadowServer advised all email users to check with their email service provider to be sure that TLS is enabled and the latest version of the protocol is being used. [ImageSource: ShadowServer]
The map shows IMAP and POP3 mail servers without TLS.
Over three million POP3 and IMAP mail servers without TLS encryption are currently exposed on the Internet and vulnerable to network sniffing attacks. Almost 900,000 are based in the U.S., another 560,000 and 380,000 in Germany and Poland, the organization found and adding: “We see around 3.3M such cases with POP3 & a similar amount with IMAP (most overlap). It's time to retire those!” You can check out vulnerability reports for both POP3 email servers and IMAP email hosts on the Shadowserver Foundation site.
IMAP and POP3 are two methods for accessing email on mail servers. IMAP is recommended for checking emails from multiple devices, such as phones and laptops because it keeps your messages on the server and synchronizes them between devices. POP3, on the other hand, downloads emails from the server, making them accessible only from the device where they were downloaded.
The TLS secure communication protocol helps secure users information while exchanging and accessing their emails over the Internet through client/server applications. However, when TLS encryption is not enabled, their messages contents and credentials are sent in clear text, exposing them to eavesdropping network sniffing attacks.
ShadowServer advised all email users to check with their email service provider to be sure that TLS is enabled and the latest version of the protocol is being used.](https://friendica-leipzig.de/photo/preview/600/416546)





![You’re not going to believe this, but it’s hilarious.
The short version of the story is that [Mr. Tick], [q3k] and [Redford] became minor stars in Poland, have caused criminal investigations to begin against the train company, and even made the front page of the New York Times. Newag, the train manufacturer in question has opened several lawsuits against them.
The lawsuit alleges the team is infringing on a Newag copyright — by publishing the code that locked the trains, no less! If that’s not enough, Newag goes on to claim that the white hat hackers are defaming the company. You’re not going to believe this, but it’s hilarious.
The short version of the story is that [Mr. Tick], [q3k] and [Redford] became minor stars in Poland, have caused criminal investigations to begin against the train company, and even made the front page of the New York Times. Newag, the train manufacturer in question has opened several lawsuits against them.
The lawsuit alleges the team is infringing on a Newag copyright — by publishing the code that locked the trains, no less! If that’s not enough, Newag goes on to claim that the white hat hackers are defaming the company.](https://friendica-leipzig.de/photo/preview/1024/396396)
![[ImageSource: media.ccc.de]
What I found fantastically refreshing was how the three take all of this in stride, as the ridiculous but incredibly inconvenient consequences of daring to tell the truth. Along the way they’ve used their platform to speak out for open-sourcing publicly funded code, and the right to repair — not just for consumers but also for large rail companies. They are truly fighting the good fight here, and it’s inspirational to see that they’re doing so with humor and dignity.
If you missed their initial, more technical, talk last year, go check it out on media.ccc.de. And if you ever find yourself in their shoes, don’t be afraid to do the right thing. Just get a good lawyer. [ImageSource: media.ccc.de]
What I found fantastically refreshing was how the three take all of this in stride, as the ridiculous but incredibly inconvenient consequences of daring to tell the truth. Along the way they’ve used their platform to speak out for open-sourcing publicly funded code, and the right to repair — not just for consumers but also for large rail companies. They are truly fighting the good fight here, and it’s inspirational to see that they’re doing so with humor and dignity.
If you missed their initial, more technical, talk last year, go check it out on media.ccc.de. And if you ever find yourself in their shoes, don’t be afraid to do the right thing. Just get a good lawyer.](https://friendica-leipzig.de/photo/preview/600/396398)

![Volkswagen’s automotive software company [Cariad], exposed data collected from around 800,000 electric cars. The info could be linked to drivers names and reveal precise vehicle locations [for some of them being as precise as a few centimeters]. The exposed databases include details for VW, Seat, Audi and Skoda vehicles.
Cariad was informed on November 26 of the issue by the Chaos Computer Club (CCC), the largest organization of ethical hackers in Europe that for more than 30 years has promoted security, privacy, and free access to information.
<https://www.ccc.de/en/>
Access to the car data was possible due to Cariad’s incorrect configuration in two IT applications, a company representative said.
The CCC hackers could access the data only after bypassing several security mechanisms that required significant time and technical expertise. Additionally, because individual vehicle data was pseudonymized for privacy purposes, the CCC hackers had to combine different data sets to associate the details with a particular user. Volkswagen’s automotive software company [Cariad], exposed data collected from around 800,000 electric cars. The info could be linked to drivers names and reveal precise vehicle locations [for some of them being as precise as a few centimeters]. The exposed databases include details for VW, Seat, Audi and Skoda vehicles.
Cariad was informed on November 26 of the issue by the Chaos Computer Club (CCC), the largest organization of ethical hackers in Europe that for more than 30 years has promoted security, privacy, and free access to information.
<https://www.ccc.de/en/>
Access to the car data was possible due to Cariad’s incorrect configuration in two IT applications, a company representative said.
The CCC hackers could access the data only after bypassing several security mechanisms that required significant time and technical expertise. Additionally, because individual vehicle data was pseudonymized for privacy purposes, the CCC hackers had to combine different data sets to associate the details with a particular user.](https://friendica-leipzig.de/photo/preview/1024/394468)