Suche
Beiträge, die mit Security getaggt sind
U.N. Security Council meets on humanitarian situation in Gaza U.N. Security Council meets on humanitarian situation in Gaza #UN #security #gaza from Islam Channel اهد الفيديو الخاص بهذا المقال هنا "
https://www.shibuyaworldnews.online/islamchannel-u-n-security-council-meets-on-humanitarian-situation-in-gaza/

#IslamChannel U.N. Security Council meets on humanitarian situation in Gaza - SHIBUYA World News
https://www.youtube.com/watch?v=RjPM9_Brf-A U.N. Security Council meets on humanitarian situation in Gaza U.N. Security Council meets on humanitarian situation in Gaza #UN #security #gaza from Islam Channel اهد الفيديو الخاص بهذا المقال هنا "🐈 (SHIBUYA World News)
UK rows back on claim Israel’s Gaza aid blockade is illegal – POLITICO - EUROPE SAYS
“But we find the lack of aid — it’s now been 15 days since aid got into Gaza — unacceptable,EUROPE SAYS (EUROPESAYS.COM)
Ein Cyberangriff legt die IT der städtischen Altenheime in Mönchengladbach lahm. Aerticket und die Schweizer Supermarktkette Spar bauen ihre Dienste wieder auf.
https://www.heise.de/news/Cyberangriff-auf-staedtische-Seniorenheime-in-Moenchengladbach-Aerticket-und-mehr-10318890.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Cyberangriff #Security #news
Israeli leaders call urgent meeting over fears of imminent 'Hamas ground invasion' - World News - News - EUROPE SAYS
Israel carried out airstrikes in the Gaza Strip, southern Lebanon and southern Syria on Monday, killing at leastEUROPE SAYS (EUROPESAYS.COM)
 GitHub uncovers new Ruby-SAML Vulnerabilities allowing Account Takeover Attacks.
GitHub uncovers new Ruby-SAML Vulnerabilities allowing Account Takeover Attacks.Two high-severity security flaws have been disclosed in the open-source ruby-saml library that could allow malicious actors to bypass Security Assertion Markup Language (SAML) authentication protections.
https://github.blog/security/sign-in-as-anyone-bypassing-saml-sso-authentication-with-parser-differentials/
#github #ruby #saml #library #it #security #privacy #engineer #media #programming #tech #news
Sign in as anyone: Bypassing SAML SSO authentication with parser differentials - The GitHub Blog
Critical authentication bypass vulnerabilities were discovered in ruby-saml up to version 1.17.0. See how they were uncovered.Peter Stöckli (The GitHub Blog)
Has anyone come across any businesses that have made the leap recently? Feel free to DM or message on Signal, mattburgess.20
#infosec #privacy #cloud #security
Stop buying American, buy European – POLITICO
'Those who buy Patriot should be offered the new-generation Franco-Italian SAMP/T. Those who buy the F-35, should be offered the Rafale. That's the way to increase the rate of production,' he said.BYTESEU (Bytes Europe)
Stop buying American, buy European – POLITICO - EUROPE SAYS
'Those who buy Patriot should be offered the new-generation Franco-Italian SAMP/T. Those who buy the F-35, should beEUROPE SAYS (EUROPESAYS.COM)
‘Critical concerns’ about internet of things security

“GlobalData’s Internet of Things report outlines that the fragmented security standards landscape and the weak security of many internet of things (IoT) devices could hold back further adoption of the technology. Furthermore, it suggests that existing IoT deployments could become a security risk due to the current state of affairs.”
Way too many IoT devices have no real security (they don’t get updates and patches, they freely call out onto the Internet, sometimes have no login security, use weak security standards, etc).
It’s partly because they are cheap devices and do not adhere to any strict security compliance.
So whilst many users have a firewall turned on for their router, that usually only blocks incoming traffic. These IoT devices can still freely establish links with the outside world, and if compromised, could end up creating a bridge to everything else on the LAN behind the firewall.
Which is why I went to quite a bit of trouble to isolate my IoT devices onto their own VLANs. If you do not have the hardware to configure VLANs for them, at least ensure they are connected to your guest network, and that the guest network is isolated from the main LAN network (there is typically a toggle setting for that).
See https://www.verdict.co.uk/critical-concerns-about-internet-of-things-security
#Blog, #IoT, #security, #technology
UNDP Report on Syria’s Economic Losses - EUROPE SAYS
The United Nations Development Program (UNDP) report, “The Impact of the Conflict in Syria,” released on February 20, 2025, paintsEUROPE SAYS (EUROPESAYS.COM)
Moldova accuses Russia of trying to rig its EU referendum – POLITICO - EUROPE SAYS
According to Secrieru, pro-European President Maia Sandu is the central target of a “brazen digital blitz” designed toEUROPE SAYS (EUROPESAYS.COM)
Die deutschen Online-Casinos der Merkur-Gruppe haben am Samstag ihre Spiele abgeschaltet. Zuvor waren privateste Daten von Hunderttausenden zugänglich.
https://www.heise.de/news/Online-Casinos-wie-Slotmagie-nach-Datenverlust-offline-10317075.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Datenschutz #Glücksspiel #Security #news
 240 Million Windows 10 Users are vulnerable to six different Exploits.
240 Million Windows 10 Users are vulnerable to six different Exploits.⚠️Protect yourself Now!!!⚠️
If you’re running a Windows 10 PC, make sure you download the latest update right now. Microsoft patched 57 vulnerabilities affecting its foundational systems and core products, including six actively exploited zero-day vulnerabilities.
https://msrc.microsoft.com/update-guide/releaseNote/2025-Mar
#microsoft #windows #update #it #security #privacy #engineer #media #tech #news
ORG, Big Brother Watch and Index on Censorship call for the Tribunal into the UK government's secret order for Apple to break encryption to be held in public.
The case happens TOMORROW.
Read more ⬇️
https://techcrunch.com/2025/03/13/apples-appeal-against-uks-secret-icloud-backdoor-order-must-be-held-in-public-rights-groups-urge/
#encryption #e2ee #privacy #security #ukpolitics #ukpol #cybersecurity #apple

Apple’s appeal against UK’s secret iCloud backdoor order must be held in public, rights groups urge | TechCrunch
Privacy rights groups have called on Apple's legal challenge to a secret U.K. government order asking it to backdoor an end-to-end encrypted (E2EE)Natasha Lomas (TechCrunch)
 Apple releases Emergency Security Patch for WebKit Zero-Day Vulnerability.
Apple releases Emergency Security Patch for WebKit Zero-Day Vulnerability.The vulnerability is tracked as CVE-2025-24201 and was found in the WebKit cross-platform browser engine used by Apple's Safari and many other apps.
⚠️Install the Update immediately!!!⚠️
[For your device security, it’s a good practice to install updates within 36 hours of becoming available.]
https://support.apple.com/en-us/100100
#apple #ios #macos #update #it #security #privacy #engineer #media #tech #news
Apple security releases - Apple Support
This document lists security updates and Rapid Security Responses for Apple software.Apple Support
Mehrere Produkte von Fortinet sind attackierbar. Sicherheitspatches schaffen Abhilfe.
https://www.heise.de/news/Schadcode-Sicherheitsluecken-bedrohen-FortiOS-FortiSandbox-Co-10314664.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Patchday #Security #Sicherheitslücken #Updates #news
Der Netzwerkausrüster Cisco hat mehrere Schwachstellen geschlossen, über die Angreifer etwa ASR-Router attackieren können.
https://www.heise.de/news/Sicherheitsupdates-Root-Sicherheitsluecke-bedroht-Cisco-ASR-Router-10314262.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Cisco #Patchday #Router #Security #Sicherheitslücken #Updates #news
US dominates European weapons purchases: report – POLITICO
Europeans are taking steps to boost their own industries, said Pieter Wezeman, a senior researcher with SIPRI, 'but the transatlantic arms-supply relationship has deep roots.BYTESEU (Bytes Europe)
https://www.kuketz-blog.de/truegerische-sicherheit-virenscanner-apps-sind-schlichtweg-ueberfluessig/
#android #security #google #tracking #virus #antivirus #app

Trügerische Sicherheit: Virenscanner-Apps sind schlichtweg überflüssig
Die Sicherheitsarchitektur von Android/iOS schränkt die Funktionsweise von Virenscanner-Apps stark ein und macht sie im Grunde nutzlos. Schlimmer: Die vermeintlichen Sicherheits-Apps sind Datenschleudern.www.kuketz-blog.de
Aktuell gibt es bei der IT-Sicherheit von Kommunen noch viele Mängel. Eine Studie klärt über die Defizite und mögliche Maßnahmen auf.
https://www.heise.de/news/Uneinheitliche-Cybersicherheitsstandards-Kommunen-ohne-klare-Strategie-10313195.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#KRITIS #NIS #Security #news
Die Hosts besprechen Lücken bei der automatischen Zertifikatsvergabe, politische Angriffe auf Verschlüsselung, technische Angriffe auf Bybit und einiges mehr.
https://www.heise.de/news/Passwort-Folge-27-News-von-Verschluesselungsangriffen-bis-Kryptodiebstahl-10309523.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Apple #Domain #Verschlüsselung #EU #iCloud #Security #Kryptowährung #news
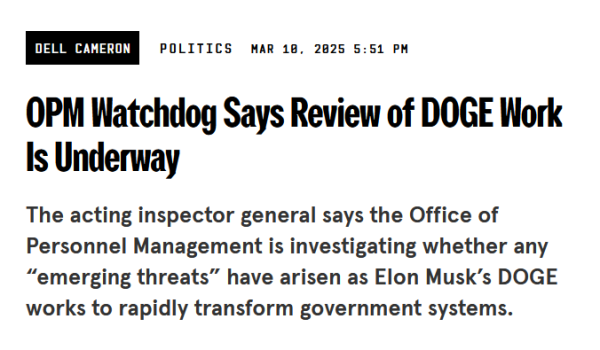
The acting inspector general says the Office of Personnel Mgmt is investigating whether any “emerging threats” have arisen as Elon Musk’s #DOGE works to rapidly transform #government systems.
https://www.wired.com/story/opm-doge-review-underway/
"In addition to #OPM, #Democrats have pressed for similar #security assessments at five other agencies...
Congressional #Republicans have committed to little, if any, formal oversight of DOGE’s work"
#Musk #Coup #GOP #USPol #News
 Strap in, get ready for more Rust Drivers in Linux Kernel.
Strap in, get ready for more Rust Drivers in Linux Kernel.Rust is alive and well in the Linux kernel and is expected to translate into noticeable benefits shortly, though its integration with the largely C-oriented codebase still looks uneasy. [The Linux and Rust communities still have some issues to work out.]
https://rust-for-linux.com/rust-kernel-policy
#linux #kernel #memory #safety #rust #drivers #it #security #privacy #engineer #media #programming #tech #news
Author: Ben Tasker
https://www.bentasker.co.uk/posts/blog/security/seducing-a-romance-scammer.html?utm_source=rss
#infosec #osint #scams #security
My Scammer Girlfriend: Baiting A Romance Fraudster
Romance fraud has been growing as an issue for years. It's not uncommon to see news stories with bewildered victims explaining just how deeply they'd been sucked in. After receiving a number of openerwww.bentasker.co.uk
"Creating four backdoors facilitates the attackers having multiple points of re-entry should one be detected and removed," c/side researcher Himanshu Anand said in a analysis last week.
https://cside.dev/blog/thousands-of-websites-hit-by-four-backdoors-in-3rd-party-javascript-attack
#wordpress #javascript #backdoors #it #security #privacy #engineer #media #tech #news
Thousands of websites hit by four backdoors in 3rd party JavaScript attack
While analyzing threats targeting WordPress frameworks, we found an attack where a single 3rd party JavaScript file was used to inject four separate backdoors into 1,000 compromised websites using cdn.csyndication[.]com/.c/side
This reveals that two thirds of all military imports used by European states come from America.
If Military Keynsianism (implied or explicit) is about ramping up domestic capacity, pivoting away from US-made weapons systems looks like being a major priority.
In the short(ish) term that may be pretty difficult
#security
h/t FT
Israeli-U.S. Joint Exercise Serves as Warning to Iran
Iran is certain to notice the American-Israeli collaboration over Middle Eastern skies. The U.S. and Israeli Air Forces carried out a joint exercise over the Mediterranean earlier this week, marking the most significant collaboration between the two …BYTESEU (Bytes Europe)
Israeli-U.S. Joint Exercise Serves as Warning to Iran - EUROPE SAYS
Iran is certain to notice the American-Israeli collaboration over Middle Eastern skies. The U.S. and Israeli Air ForcesEUROPE SAYS (EUROPESAYS.COM)
Die EU-Staaten sollen das um Jahre verzögerte Ein-/Ausreisesystem fürs Grenzmanagement nun über einen Zeitraum von sechs Monaten stufenweise einführen können.
https://www.heise.de/news/Biometrische-Kontrolle-Ein-und-Ausreisesystem-der-EU-soll-schrittweise-starten-10309153.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Biometrie #EU #Security #news
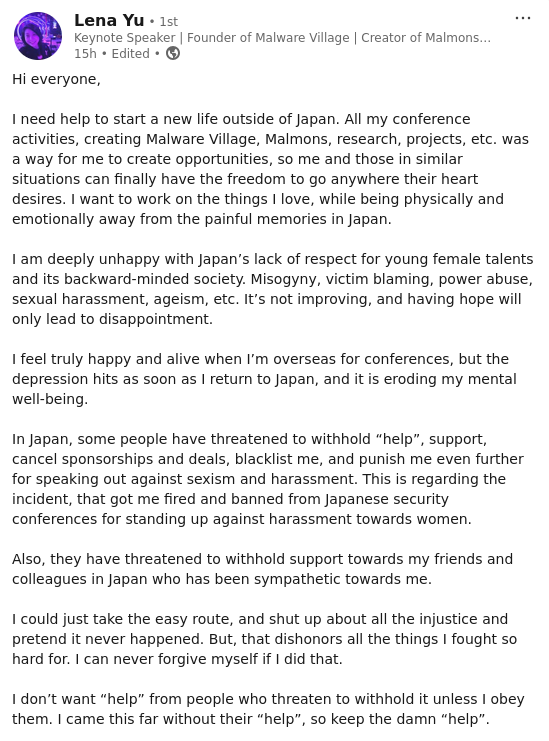
sadly, it wasn't valued in Japanese #InfoSec society, esp. when calling out sexual harassment & because of that Lena was ostracised. she deserves better than this
sharing her msg in hope someone in #Fediverse would be interested in hiring her outside of Japan. reposts appreciated
https://lambdamamba.com/index.html
#FediHired #GetFediHired #Malware #CyberSecurity #Job #JobSearch #Hiring #Security
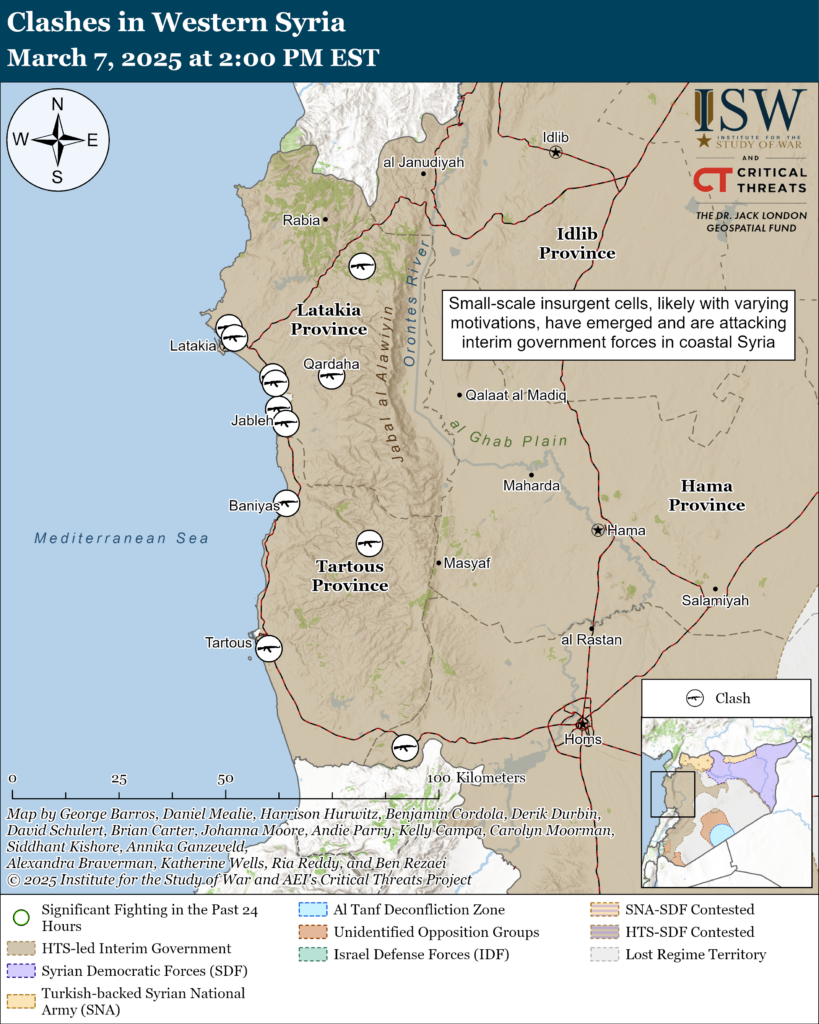
Iran Update, March 7, 2025
Iran Update, March 7, 2025 Kelly Campa, Andie Parry, Alexandra Braverman, Ria Reddy, Katherine Wells, Carolyn Moorman, Siddhant Kishore, Ben Rezaei and Brian Carter Information Cutoff: 2:00 pm ET The Critical Threats Project (CTP) at the American E…BYTESEU (Bytes Europe)
Im stationären Handel sind Angaben zur IT-Security bei Routern & Co. kaum vorhanden, hat eine Analyse fürs BSI ergeben. Im E-Commerce sieht es kaum besser aus.
https://www.heise.de/news/BSI-Studie-Mangelhafte-Information-ueber-IT-Sicherheit-bei-vernetzten-Geraeten-10308898.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#BSI #Cybersecurity #eCommerce #Security #Router #news

BSI-Studie: Mangelhafte Information über IT-Sicherheit bei vernetzten Geräten
Im stationären Handel sind Angaben zur IT-Security bei Routern & Co. kaum vorhanden, hat eine Analyse fürs BSI ergeben. Im E-Commerce sieht es kaum besser aus.Stefan Krempl (heise online)
Wer ein Active Directory betreibt, sollte Ebenen trennen und gesicherte Admin-Workstations nutzen. Dieses Webinar gibt praktische Hilfe bei der Umsetzung.
https://www.heise.de/news/Am-Dienstag-Das-Active-Directory-Webinar-von-heise-security-10278105.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#ActiveDirectory #Security #news
Attackers are exploiting this flaw to run malicious code and install Cobalt Strike (yeah, that penetration testing tool – go figure 🙄). And that's when things get really nasty: password theft, lateral movement within the network... 🤬
The bottom line is this: vulnerabilities like these are like striking gold for cybercriminals. A quick update is absolutely essential! But what's even more critical? Regular, hands-on penetration tests! Automated tools often miss these types of vulnerabilities. ☝️
I'm curious to know: What steps do you take to secure your PHP applications? What penetration testing methods do you find most effective? 🤔
#Security #Pentesting #PHP
Höhere Preise für schlechtere Leistung frustrieren Streaming-Abonnenten, illegale Angebote bekommen Zuspruch. c't zeigt Techniken und rechtliche Konsequenzen
https://www.heise.de/meinung/Blick-ins-Heft-c-t-6-2025-Videostreaming-zwischen-Abofrust-und-Illegalitaet-10306759.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Digitalisierung #Drucker #FotoTool #Kaufberatung #MicrosoftTeams #MiniPC #Multifunktionsgeräte #Piraterie #Security #Smartphone #Streaming #USBStick #Video #news



![[ImageSource: GitHub]
"Attackers who are in possession of a single valid signature that was created with the key used to validate SAML responses or assertions of the targeted organization can use it to construct SAML assertions themselves and are in turn able to log in as any user," GitHub Security Lab researcher Peter Stöckli said in a post.
The Microsoft-owned subsidiary also noted that the issue boils down to a "disconnect" between verification of the hash and verification of the signature, opening the door to exploitation via a parser differential.
Versions 1.12.4 and 1.18.0 also plug a remote denial-of-service (DoS) flaw when handling compressed SAML responses (CVE-2025-25293, CVSS score: 7.7).
⚠️Users are recommended to update to the latest version to safeguard against potential threats.⚠️
The findings come nearly six months after GitLab and ruby-saml moved to address another critical vulnerability (CVE-2024-45409, CVSS score: 10.0) that could also result in an authentication bypass. [ImageSource: GitHub]
"Attackers who are in possession of a single valid signature that was created with the key used to validate SAML responses or assertions of the targeted organization can use it to construct SAML assertions themselves and are in turn able to log in as any user," GitHub Security Lab researcher Peter Stöckli said in a post.
The Microsoft-owned subsidiary also noted that the issue boils down to a "disconnect" between verification of the hash and verification of the signature, opening the door to exploitation via a parser differential.
Versions 1.12.4 and 1.18.0 also plug a remote denial-of-service (DoS) flaw when handling compressed SAML responses (CVE-2025-25293, CVSS score: 7.7).
⚠️Users are recommended to update to the latest version to safeguard against potential threats.⚠️
The findings come nearly six months after GitLab and ruby-saml moved to address another critical vulnerability (CVE-2024-45409, CVSS score: 10.0) that could also result in an authentication bypass.](https://friendica-leipzig.de/photo/preview/600/777841)




![[ImageSource: Shutterstock]
However, these are the actively exploited vulnerabilities to worry about right now:
• CVE-2025-24993: This is a common buffer overflow exploit. In simple terms, criminals take advantage of a coding error and overload your system memory with more, which overwrites your current system memory.
• CVE-2025-24991: If an unsuspecting user mounts a nefarious virtual hard disk (VHD), this bug allows a hacker to read all of your data (even all the out-of-bounds stuff).
• CVE-2025-24984: This exploit allows an attacker to record all sensitive information into a log file for them to take. While it’s a concerning one, it does require the malicious actor to physically access your computer.
• CVE-2025-26633: A simple (but risky) bypass flaw in the Microsoft Management Console.
• CVE-2025-24985: This one also requires the attacker to convince a user to mount a VHD of their own volition. But once done, there is a privilege escalation flaw that can be exploited to take over the victim’s entire computer.
• CVE-2025-24983: This is a system-level exploit where a malicious actor can run a specially crafted program that exploits the Kernel Subsystem of Windows to give an attacker top privileges to your system. [ImageSource: Shutterstock]
However, these are the actively exploited vulnerabilities to worry about right now:
• CVE-2025-24993: This is a common buffer overflow exploit. In simple terms, criminals take advantage of a coding error and overload your system memory with more, which overwrites your current system memory.
• CVE-2025-24991: If an unsuspecting user mounts a nefarious virtual hard disk (VHD), this bug allows a hacker to read all of your data (even all the out-of-bounds stuff).
• CVE-2025-24984: This exploit allows an attacker to record all sensitive information into a log file for them to take. While it’s a concerning one, it does require the malicious actor to physically access your computer.
• CVE-2025-26633: A simple (but risky) bypass flaw in the Microsoft Management Console.
• CVE-2025-24985: This one also requires the attacker to convince a user to mount a VHD of their own volition. But once done, there is a privilege escalation flaw that can be exploited to take over the victim’s entire computer.
• CVE-2025-24983: This is a system-level exploit where a malicious actor can run a specially crafted program that exploits the Kernel Subsystem of Windows to give an attacker top privileges to your system.](https://friendica-leipzig.de/photo/preview/600/765458)