Suche
Beiträge, die mit CYBERSECURITY getaggt sind
Because of the Signal chat leak, it’s less likely that they’ll use vulnerabilities in Signal to do that. Equally, bad actors such as drug cartels may also feel safer using Signal. Their security against the US government lies in the fact that the US government shares their vulnerabilities. No one wants their secrets exposed.
I have long advocated for a "defense dominant" cybersecurity strategy. As long as smartphones are in the pocket of every government official, police officer, judge, CEO, and nuclear power plant operator—and now that they are being used for what the White House now calls calls "sensitive," if not outright classified conversations among cabinet members—we need them to be as secure as possible. And that means no government-mandated backdoors.
We may find out more about how officials—including the vice president of the United States—came to be using Signal on what seem to be consumer-grade smartphones, in a apparent breach of the laws on government records. It’s unlikely that they really thought through the consequences of their actions.
Nonetheless, those consequences are real. Other governments, possibly including US allies, will now have much more incentive to break Signal’s security than they did in the past, and more incentive to hack US government smartphones than they did before March 24.
For just the same reason, the US government has urgent incentives to protect them."
https://www.schneier.com/blog/archives/2025/03/the-signal-chat-leak-and-the-nsa.html
#USA #CyberSecurity #Signal #Encryption #Backdoors #Privacy #NSA #StateHacking
The Signal Chat Leak and the NSA - Schneier on Security
US National Security Advisor Mike Waltz, who started the now-infamous group chat coordinating a US attack against the Yemen-based Houthis on March 15, is seemingly now suggesting that the secure messaging service Signal has security vulnerabilities.Bruce Schneier (Schneier on Security)
#PostQuantum #CyberSecurity #Forschung
https://nachrichten.idw-online.de/2025/03/31/forschungsprogramm-sca4pqc-soll-seitenkanalresistente-post-quanten-kryptologie-entwickeln
Post-Quanten-Sicherheit als Herausforderung der Zukunft - Cyberagentur
Forschungsprogramm SCA4PQC soll seitenkanalresistente Post-Quanten Kryptologie entwickeln Die Agentur für Innovation in der Cybersicherheit GmbH (Cyberagentur) startet das Forschungsprogramm zur Seitenkanalresistenz in der Post-Quanten Kryptologie.ML (Cyberagentur)
It includes the following and much more:
➝ DNA of 15 Million People for Sale in #23andMe Bankruptcy,
➝ #Trump administration accidentally texted a journalist its war plans,
➝ Critical Ingress #NGINX controller vulnerability allows RCE without authentication,
➝ #Cyberattack hits Ukraine's state railway,
➝ Troy Hunt's Mailchimp account was successfully phished,
➝ #OpenAI Offering $100K Bounties for Critical #Vulnerabilities,
➝ #Meta AI is now available in #WhatsApp for users in 41 European countries... and cannot be turned off
Subscribe to the #infosecMASHUP newsletter to have it piping hot in your inbox every week-end ⬇️
https://infosec-mashup.santolaria.net/p/infosec-mashup-13-2025
![🕵🏻♂️ [InfoSec MASHUP] 13/2025](https://friendica-leipzig.de/photo/preview/600/850406)
🕵🏻♂️ [InfoSec MASHUP] 13/2025
DNA of 15 Million People for Sale in 23andMe Bankruptcy, Trump administration accidentally texted a journalist its war plans, Critical Ingress NGINX controller vulnerability allows RCE without authentication, Cyberattack hits Ukraine's state railway,…X’s InfoSec Newsletter

Private Fotos aus speziellen Dating-Apps ungeschützt online sichtbar
Sicherheitsforscher haben herausgefunden, dass Millionen privater Bilder aus spezialisierten Dating-Apps ungeschützt aus dem Internet abrufbar waren. Da es sich vielfach um explizite Aufnahmen handelt, kann dies für die Nutzer gefährlich werden.Christian Kahle (WinFuture.de)
The most recent data breach report, published Friday by Bleeping Computer, said that Oracle Health—a health care software-as-a-service business the company acquired in 2022—had learned in February that a threat actor accessed one of its servers and made off with patient data from US hospitals. Bleeping Computer said Oracle Health customers have received breach notifications that were printed on plain paper rather than official Oracle letterhead and were signed by Seema Verma, the executive vice president & GM of Oracle Health.
The other report of a data breach occurred eight days ago, when an anonymous person using the handle rose87168 published a sampling of what they said were 6 million records of authentication data belonging to Oracle Cloud customers. Rose87168 told Bleeping Computer that they had acquired the data a little more than a month earlier after exploiting a vulnerability that gave access to an Oracle Cloud server."
https://arstechnica.com/security/2025/03/oracle-is-mum-on-reports-it-has-experienced-2-separate-data-breaches/
#CyberSecurity #Oracle #DataBreaches #DataProtection

Oracle has reportedly suffered 2 separate breaches exposing thousands of customers‘ PII
Alleged breaches affect Oracle Cloud and Oracle Health.Dan Goodin (Ars Technica)
Kunden der Bundesagentur für Arbeit wurden Ziel von Kriminellen. Mit geänderten Kontonummern wurde offenbar versucht, Leistungen der Agentur abzuzweigen.
https://www.heise.de/news/Kriminelle-wollten-Leistungen-der-Bundesagentur-ergaunern-10333185.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Arbeitswelt #Cybercrime #Cybersecurity #Datenschutz #IT #news
Now, there are a lot of ways that you can get access to somebody's phone. You can look over their shoulder while they're reading their messages, right? You can find out their password and unlock their phone, right? You can use forensic tools that police have like a Cellebrite or a break-in device to unlock phones, and then you can read the messages that way. You can also use malware. Installing malware on somebody's phone is a way that governments often gain access to people's private encrypted communications. Things like Pegasus malware or they're recently written about malware from Paragon Solutions that was going after WhatsApp messages, which was also end-to-end encrypted.
A concern about national security folks using these devices for the communications is that it makes it much more likely that their devices will get targeted by malware. And there's a lot of countries that have espionage capabilities that have the capability to target people's phones that would be very interested in knowing what Pete Hegseth is talking about, or what other high-level cabinet officials are talking about. So that makes for a very juicy intelligence target for foreign intelligence, and I think it's safe to assume that's something that many countries are now going to be going after."
https://www.techpolicy.press/about-that-signal-chat/
#USA #Trump #CyberSecurity #Signal #Encryption #CyberWarfare

About that Signal Chat
To learn more about the scandal, Justin Hendrix spoke to Just Security co-editor-in-chief Ryan Goodman and EFF senior staff technologist Cooper Quintin.Justin Hendrix (Tech Policy Press)

Alte Microsoft-Domain: Spammer schleusen Werbemüll in Firmennetze
Microsoft ist offenbar ein Fehler unterlaufen, der dafür gesorgt hat, dass eine von dem Softwarekonzern zuvor für einen Videodienst genutzte Domain in die Hände von Spammern gelangen konnte.Roland Quandt (WinFuture.de)
“It’s so unbelievable,” a former White House official, granted anonymity to discuss The Atlantic’s report candidly, said Monday. “These guys all have traveling security details to set up secure comms for them, wherever they are.”
The former White House official pointed out that members of Trump’s Cabinet — including the vice president, Defense Secretary Pete Hegseth, and Director of National Intelligence Tulsi Gabbard, among others — were likely using personal devices, since in most cases, Signal cannot be downloaded onto official federal devices. This alone creates a host of cybersecurity issues."
https://www.politico.com/news/2025/03/25/signal-cybersecurity-trump-war-planning-00246881
#USA #Trump #CyberSecurity #Signal #Privacy
#Cybersecurity #RecordDownloads #SignalGroupChat #TrumpAdministration #SignalApp
https://www.wired.com/story/signalgate-is-driving-the-most-us-downloads-of-signal-ever/
“These differences may be marketing gloss to Meta, but to us, they’re fundamental life or death issues that the public deserves to understand so they can make an informed choice,” Whittaker concludes.
On Sunday, WhatsApp sent a message to Dutch users stating that the company can’t read their messages, including text and voice messages, photos, videos, and calls.
“They are protected by end-to-end encryption because we are always committed to protecting your privacy,” the note reads."
https://cybernews.com/news/whatsapp-signal-executives-battle/
#Cybersecurity #Privacy #Encryption #Signal #WhatsApp

Risiko für Stromnetze: Viele Sicherheitslücken in PV-Systemen entdeckt
In Photovoltaik-Systemen stecken nicht weniger Sicherheitslücken als in vielen anderen elektronischen Geräten. Die Folgen können gravierend sein - bis hin zu einer Destabilisierung ganzer Stromnetze.Christian Kahle (WinFuture.de)
----
We have so many questions that are making us feel a bit uneasy: ❓
In what ways can you be certain that a particular open-source software solution is secure?
What factors do individuals with an IT background consider when making decisions about open source software safety?
Certain open source software solutions have extensive code bases. Consequently, it would require a significant investment of time to verify the absence of bugs or malicious code. 🐞 ☠️
That said, even those who can understand code may not always have the time or energy to investigate every piece of software they install. So what are their criteria for endorsing a particular piece of software that they haven't analysed its code? 🧭
And what tips do you have for people who aren't developers, to help them make the best choices when they can't understand the code? Who can they trust?
#opensource #cybersecurity
By Victoria Pengilley
The data of 16,000 readers of the Sydney Morning Herald, The Age and The Financial Review is exposed online following a major cyber security breach
https://www.abc.net.au/news/2025-03-27/data-16000-nine-newspapers-readers-breach/105105692
#CyberSecurity #CyberCrime #Media #NewsandMagazinePublishingIndustry #VictoriaPengilley

Lücke in VMware: Virtuelle Maschinen mit problematischen Löchern
Die Windows-Version der Virtualisierungs-Lösung VMware enthält eine schwerwiegende Sicherheitslücke. Markeneigner Broadcom hat jetzt einen Patch veröffentlicht, der das Problem beheben soll und unbedingt zügig eingespielt werden sollte.Christian Kahle (WinFuture.de)

Google: Chrome-Notfall-Patch gegen bereits laufende Spionage-Angriffe
Google hat außerplanmäßig ein wichtiges Sicherheitsupdate für die Windows-Version seines Chrome-Browsers veröffentlicht.Christian Kahle (WinFuture.de)
The date was Saturday, March 15. President Donald Trump was at his Mar-a-Lago estate attending a “candlelight” dinner that wasn’t on his public calendar. On the lawn outside, luxury cars were on display: a Rolls Royce was parked near a Bugatti and Lamborghini. Guests milled about, taking photographs of each other and the vehicles. Earlier that day, the United States had bombed Yemen, targeting Houthi leadership. At least 53 people, including children, were killed.
Trump flew to the event on Air Force One with Elon Musk and Musk’s four year old son X, according to photos and videos viewed by WIRED. Throughout the weekend, Musk was in close contact with Trump and at least one member of the president’s brain trust who was participating in a Signal group chat where highly sensitive details of the planned operation were being shared. Experts say the conversation appears to have violated government protocols on information sharing."
https://www.wired.com/story/trump-officials-signal-chat-candlelight-dinner-mar-a-lago-yemen/
#USA #Trump #Musk #Leaks #PressFreedom #Signal #CyberSecurity #Privacy
"Frau Wolfangel, Sie wollen sich doch nur wieder heimlich einwählen."
Ich schwöre, ich wähle mich (jedenfalls heute 😜 ) nicht ein, sondern schreibe nur unschuldig einen Artikel. Wer weiß die Antwort?
#signal #cybersecurity
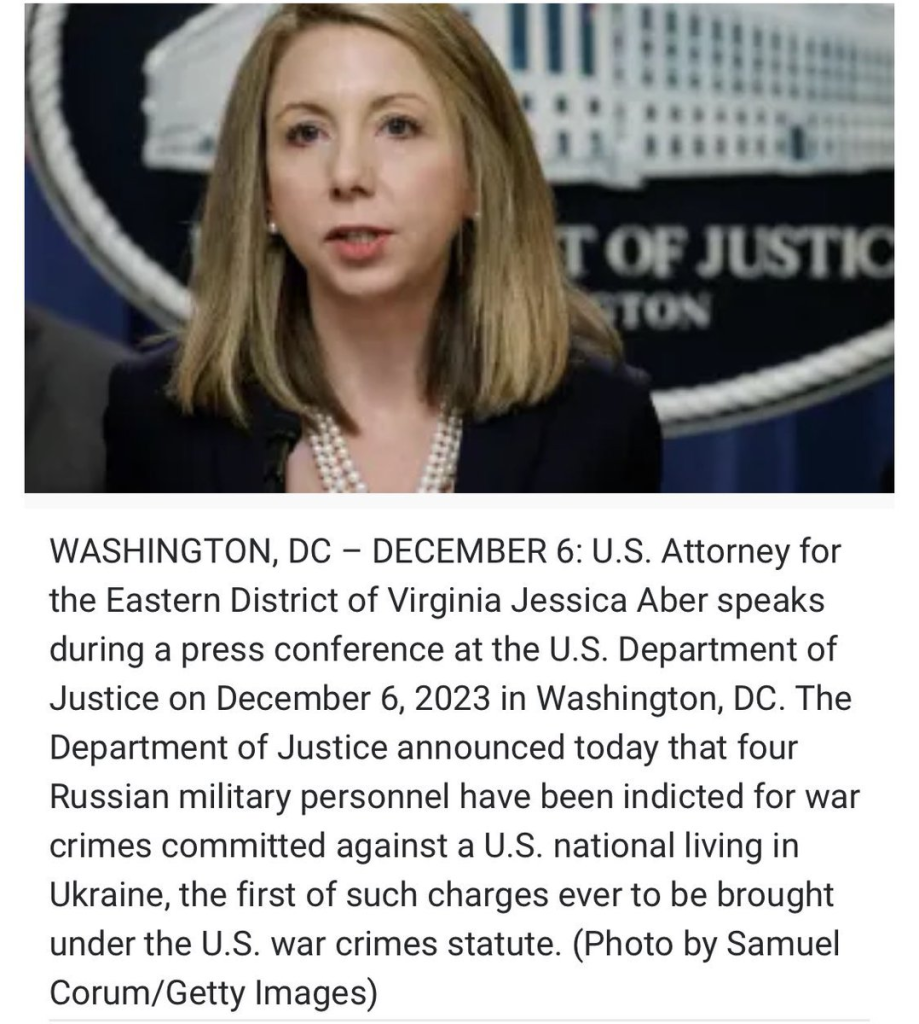
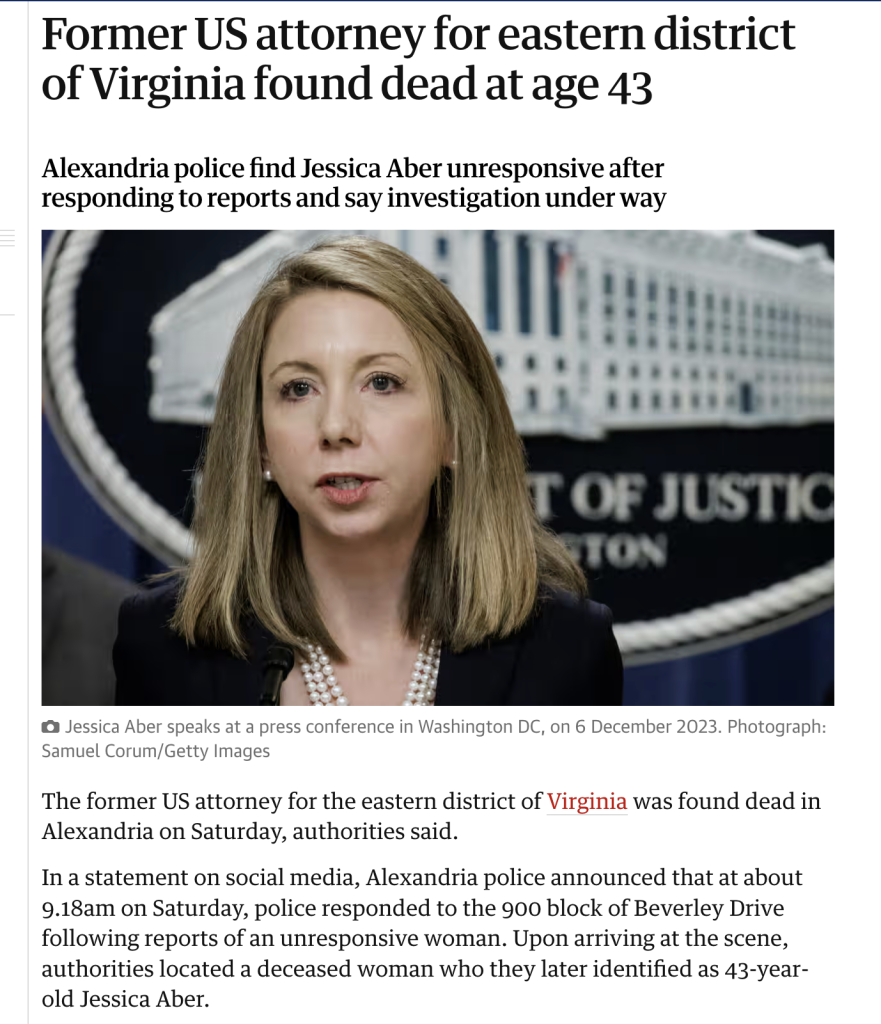
September 2024: US District Attorney Jessica Aber indicts Russian cryptocurrency money launderer / cybercriminal #SergeyIvanov
November 2024: US District Attorney Jessica Aber accuses Virginia based companies of running "three different schemes to illegally transship sensitive American technology to Russia," including sending equipment to a Russian telecommunications company linked to the #Kremlin and Russia's notorious #FSB security agency.
March 2025: Former US District Attorney Jessica Aber found dead at age 43
More: https://www.newsweek.com/jessica-aber-death-2049234
#Putin #VladimirPutin #JessicaAber #Russia #UkraineWar #Virginia #Vapol #crime #alexandria #TrueCrime #uspol #eupol #eu #AsifRahman #infosec #ransomware #cybersecurity
Ex-US Attorney Jessica Aber Investigated Russia, CIA Leaker Before Death
Aber resigned as U.S. Attorney for the Eastern District of Virginia after President Donald Trump returned to the Oval Office.Ellie Cook (Newsweek)
https://grafa.com/news/media-sinclair-cfo-lucy-rutishauser-announces-retirement-plans-404839?utm_source=us_news_en&utm_medium=mastodon&utm_campaign=404839

Ausgefeilte Tarnung: Verseuchte Spieledemo über Steam beworben
Erneut wird ein gefährlicher Malware-Angriff auf Steam-Nutzer bekannt. Als harmlose Spiele-Demo getarnt, verbreitet "Sniper: Phantom's Resolution" Schadsoftware über externe Downloads. Perfide dabei: Die Malware umgeht Windows-Sicherheitssysteme.Nadine Juliana Dressler (WinFuture.de)
Das FBI hat ein Start-up geführt, um die Unterwelt zu verwanzen. Dark Wire ist die Geschichte einer der größten verdeckten Ermittlungen der vergangenen Jahre.
https://www.heise.de/tests/Buchkritik-Dark-Wire-von-Joseph-Cox-10304658.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Cybercrime #Cybersecurity #Entertainment #FBI #Geheimdienste #news
Collaboration between Big Tech and the Trump administration began before Donald Trump’s swearing-in on January 20. Amazon, Meta, Google, Microsoft, and Uber each gave $1 million to Trump’s inauguration. Separately, in personal donations, so did Meta CEO Mark Zuckerberg and Apple’s Tim Cook.
Americans concerned about the Trump administration and Silicon Valley’s embrace of it, may consider becoming a “digital expat”—moving your digital life off of US-based systems. Meanwhile, Europeans are starting to see US data services as “no longer safe” for businesses, governments, and societies.
Here’s a brief rundown of the privacy, security, and civil liberties issues related to the use of US-based digital services that suddenly feel more urgent—and what to do about it."
https://www.wired.com/story/trump-era-digital-expat/
#USA #Trump #BigTech #Privacy #CyberSecurity #DataProtection
Staffed by ex Unit 8200 members, the #cyber spying arm of the #IDF that designed #algorithms that automated the #genocide of #Gaza & was also responsible for the #pagerattack in #Lebanon.
https://open.substack.com/pub/thegrayzone/p/google-imports-ex-israeli-spies-as
#Israel #Palestine #MiddleEast #Genocide #EthnicCleansing #Palestinians #PalestinianLivesMatter #Politics #Egypt #Syria #Iraq #Iran #SaudiArabia #Qatar #USA #Zionism #BDS #Ceasefire #ArmsEmbargo #Netanyahu

Visual Studio Code: Ransomware in Entwicklung in Add-on versteckt
In Microsofts Entwicklungsumgebung Visual Studio Code gibt es den nächsten Sicherheitsalarm - und diesmal scheint es sich um eine echte Gefahr zu handeln. In zwei Erweiterungen wurden Komponenten einer Ransomware entdeckt.Christian Kahle (WinFuture.de)
The data breach dates back to June 2024 but has not been previously reported, and there is no indication that SpyX’s operators ever notified its customers or those targeted by the spyware.
The SpyX family of mobile spyware is now, by our count, the 25th mobile surveillance operation since 2017 known to have experienced a data breach, or otherwise spilled or exposed their victims’ or users’ data, showing that the consumer-grade spyware industry continues to proliferate and put people’s private data at risk.
The breach also provides a rare look at how stalkerware like SpyX can also target Apple customers.
Troy Hunt, who runs data breach notification site Have I Been Pwned, received a copy of the breached data in the form of two text files, which contained 1.97 million unique account records with associated email addresses."
https://techcrunch.com/2025/03/19/data-breach-at-stalkerware-spyx-affects-close-to-2-million-including-thousands-of-apple-users/
#CyberSecurity #Spyware #SpyX #Apple #Stalkerware #Surveillance

Data breach at stalkerware SpyX affects close to 2 million, including thousands of Apple users | TechCrunch
Another consumer-grade spyware operation was hacked in June 2024, which exposed thousands of Apple Account credentials.Zack Whittaker (TechCrunch)
- Infrastructure Analysis of Paragon Spyware. Based on a tip from a collaborator, we mapped out server infrastructure that we attribute to Paragon’s Graphite spyware tool. We identified a subset of suspected Paragon deployments, including in Australia, Canada, Cyprus, Denmark, Israel, and Singapore.
- Identifying a Possible Canadian Paragon Customer. Our investigation surfaced potential links between Paragon Solutions and the Canadian Ontario Provincial Police, and found evidence of a growing ecosystem of spyware capability among Ontario-based police services.
- Helping WhatsApp Catch a Zero-Click. We shared our analysis of Paragon’s infrastructure with Meta, who told us that the details were pivotal to their ongoing investigation into Paragon.
- WhatsApp discovered and mitigated an active Paragon zero-click exploit, and later notified over 90 individuals who it believed were targeted, including civil society members in Italy.
- Android Forensic Analysis: Italian Cluster. We forensically analyzed multiple Android phones belonging to Paragon targets in Italy (an acknowledged Paragon user) who were notified by WhatsApp. We found clear indications that spyware had been loaded into WhatsApp, as well as other apps on their devices."
#CyberSecurity #Israel #Paragon #Spyware #WhatsApp #Meta #Italy #Surveillance
https://citizenlab.ca/2025/03/a-first-look-at-paragons-proliferating-spyware-operations/

Virtue or Vice? A First Look at Paragon’s Proliferating Spyware Operations - The Citizen Lab
In our first investigation into Israel-based spyware company, Paragon Solutions, we begin to untangle multiple threads connected to the proliferation of Paragon's mercenary spyware operations across the globe.Bill Marczak (The Citizen Lab)
There’s also a contradiction at play. If politicians dream of making the UK a technology hub they should not be working to undermine the foundations of cyber security, on which a workable tech industry relies.
The government should withdraw its misguided mandate. Instead of surreptitiously cutting the brake cables on the technological car, it should be working to strengthen security and privacy of the technology that forms the nervous system of our world. Business leaders must also take a role, making it clear that these dangerous moves are unacceptable, and pushing the companies they license technology from to deploy encryption, and other protections, without which their interests and those of their customers will be vulnerable.
We have ceded so many of the core operations of our lives and institutions to tech, we must recognise that strong encryption isn’t the enemy of security — it is security. The argument that weakening encryption will make any of us safer is as wrong as it is dangerous."
https://www.ft.com/content/a934150f-e0f5-4e75-a2d1-a3671ea52ca0
#UK #CyberSecurity #Encryption #Backdoors #Privacy #Apple
The war on encryption is dangerous
Government demands to access encrypted data via back doors will leave it vulnerable to hacks, breaches and theftMeredith Whittaker (Financial Times)
https://techcrunch.com/2025/03/19/researchers-name-several-countries-as-potential-paragon-spyware-customers/
#privacy #cybersecurity #Australia #Canada #Cyprus #Denmark #Israel #Singapore

Researchers name six countries as likely customers of Paragon's spyware | TechCrunch
The Citizen Lab said it believes several governments may be customers of spyware maker Paragon Solutions.Lorenzo Franceschi-Bicchierai (TechCrunch)
#Cybersecurity #Journal #Netzpolitik #Security #news
Oh weh, da kann man den Menschen nur alles Gute und viel Glück wünschen. Im Kreml lacht man sich bestimmt den Rücken krumm.
Liebe Leute, lasst euch das eine Warnung sein, was passiert, falls hier jemals die #AFD irgendetwas relevantes zu sagen bekommt. Die werden denn Staat genauso auf links ... äh ... rechts drehen und alles zerstören, was über Jahrzehnte mühsam aufgebaut wurde!
The report investigates Paragon Solutions, an Israeli spyware company founded in 2019 that sells a product called Graphite. Through infrastructure analysis, the researchers identified potential Paragon deployments in several countries. They also found evidence linking Paragon to the Canadian Ontario Provincial Police. Working with WhatsApp, they discovered and mitigated a Paragon zero-click exploit targeting civil society members. Forensic analysis of Android devices in Italy confirmed Paragon infections. The report also examines a potentially related iPhone spyware case. It highlights Paragon's targeting of individuals involved in migrant rescue operations in the Mediterranean, raising questions about the company's claims of only selling to customers respecting human rights. The findings challenge Paragon's marketing approach and demonstrate the ongoing risks of mercenary spyware abuse, even in democracies.
Pulse ID: 67db3e42358011c1a3975302
Pulse Link: https://otx.alienvault.com/pulse/67db3e42358011c1a3975302
Pulse Author: AlienVault
Created: 2025-03-19 21:59:30
Be advised, this data is unverified and should be considered preliminary. Always do further verification.
#Android #Canadian #CyberSecurity #InfoSec #Israel #Italy #OTX #OpenThreatExchange #RAT #RCE #SpyWare #WhatsApp #bot #AlienVault
Very interesting deep-dive into the Paragon spyware by Israeli company Paragon Solutions Ltd.
Summary:
A First Look at Paragon's Proliferating Spyware Operations" investigates Paragon Solutions, an Israeli spyware vendor founded in 2019 that sells a product called Graphite. Paragon claims to have safeguards against abuse, distinguishing itself from competitors like NSO Group. The investigation mapped Paragon's server infrastructure, identifying potential deployments in Australia, Canada, Cyprus, Denmark, Israel, and Singapore, with a possible connection between Paragon and the Ontario Provincial Police in Canada. Meta and WhatsApp discovered and mitigated a Paragon zero-click exploit, notifying over 90 targeted individuals. Targets included civil society members in Italy, with forensic analysis confirming spyware infections on Android phones. The findings raise serious concerns about Paragon's claims of preventing abuse, as evidence shows targeting of human rights groups, government critics, and journalists.
#Cybersecurity #Spyware #Israel #Denmark #Canada #Journalists #WhatsApp #Paragon

Virtue or Vice? A First Look at Paragon’s Proliferating Spyware Operations - The Citizen Lab
In our first investigation into Israel-based spyware company, Paragon Solutions, we begin to untangle multiple threads connected to the proliferation of Paragon's mercenary spyware operations across the globe.Bill Marczak (The Citizen Lab)
New #Blog post going through a #TryHackMe challenge. This time detecting two different attack types with snort!
https://ligniform.blog/posts/snort-live-attacks/
💜 🌱
#InfoSec #Learning #CyberSecurity #BlueTeam #Hacking
CTF Writeup: Snort Challenge - Live Attacks
Quick writeup of a Snort challenge on TryHackMe.Ligniform (Ligniform Blog)
Let me put the important words in uppercase.
So, CLOUDFLARE ANALYZED PASSWORDS PEOPLE ARE USING to LOG IN to sites THEY PROTECT and DISCOVERED lots of re-use.
[Edit with H/T: https://benjojo.co.uk/u/benjojo/h/cR4dJWj3KZltPv3rqX]
https://blog.cloudflare.com/password-reuse-rampant-half-user-logins-compromised/
#cloudflare #password #cybersecurity

EU opens fiscal tap to secure Europe but warns against ‘defense washing’
Economy Commissioner Valdis Dombrovskis stressed the flexibility is a stop-gap until countries reframe budgets around higher defense needs.Giovanna Faggionato (POLITICO)

Pressure mounts on Metsola to sideline lawmakers linked to Huawei bribery probe
MEPs are demanding the Parliament president strengthen internal reporting mechanisms.Max Griera (POLITICO)

'Autonomie in Gefahr': Niederlande wollen sich von US-Software lösen
Das niederländische Parlament hat heute eine Reihe von Beschlüssen gefasst, mit denen die Regierung dazu gebracht werden soll, sich von der Abhängigkeit von US-Softwareherstellern zu befreien.Roland Quandt (WinFuture.de)
Geschasste Mitarbeiter sollen sich per E-Mail melden - und werden nach Rückkehr sofort freigestellt. Gerüchte über ihr Red Team dementiert die CISA.
https://www.heise.de/news/Chaos-bei-der-CISA-US-Cybersicherheitsbehoerde-holt-Gefeuerte-per-Website-zurueck-10320140.html?wt_mc=sm.red.ho.mastodon.mastodon.md_beitraege.md_beitraege&utm_source=mastodon
#Cybersecurity #Journal #Netzpolitik #Security #news

Chaos bei der CISA: US-Cybersicherheitsbehörde holt Gefeuerte per Website zurück
Geschasste Mitarbeiter sollen sich per E-Mail melden - und werden nach Rückkehr sofort freigestellt. Gerüchte über ihr Red Team dementiert die CISA.Dr. Christopher Kunz (heise online)
A few days ago Brian Krebs wrote about ClickFix, and now Sekoia has written a technical deep dive of said malicious framework.
In the Sekoia report they analyze the evolution of ClearFake, a malicious JavaScript framework that compromises legitimate websites to deliver malware through drive-by downloads. Since its emergence in July 2023, ClearFake has evolved from displaying fake browser updates to using sophisticated social engineering tactics called 'ClickFix' that trick users into executing malicious PowerShell code. The latest variant (December 2024-February 2025) uses fake reCAPTCHA or Cloudflare Turnstile verifications alongside technical issues to deceive users. ClearFake leverages the Binance Smart Chain through a technique called 'EtherHiding' to store malicious code, making it impossible to remove. The framework has infected thousands of websites and is actively distributing Lumma Stealer and Vidar Stealer malware.
https://krebsonsecurity.com/2025/03/clickfix-how-to-infect-your-pc-in-three-easy-steps/
@briankrebs
@sekoia_io
#CyberSecurity #ClickFix #ThreatIntel

clearfake-malware-compromised-websites
ClearFake spreads malware via compromised websites, using fake CAPTCHAs, JavaScript injections, and drive-by downloads.Sekoia TDR (SEKOIA.IO Blog)