Suche
Beiträge, die mit TECH getaggt sind
#Finance #Law #Tech #Journalism
https://propub.li/4fQL3uY

Ten Ways Billionaires Avoid Taxes on an Epic Scale
The top tax-avoidance techniques used by billionaires like Elon Musk, Jeff Bezos, Peter Thiel and Steve Ballmer.ProPublica
Half-Life 2 is getting a major update in celebration of the classic title’s 20th anniversary. In addition to Steam Workshop support directly within the game, Valve has fixed bugs and restored some content, added new graphics settings, updated gamepad controls and a whole lot more.
https://www.half-life.com/en/halflife2/20th
#halflife2 #20th #anniversary #update #valve #retro #gaming #art #engineer #media #tech #news
Half-Life 2 Anniversary Update
Experience Half-Life 2 all over again, with a brand-new commentary mode, improved graphics and gameplay options, Steam Workshop support, and more.Half-Life 2 Anniversary Update
After months of doing watchalongs on here, & the laughs from the #totp crowd, I’d love to try a “disco” night, set up like a real time synched playlist to those who want to join in.
If it works, we could have different people as ‘DJ’ on diff nights.
Only thing is, I’m not sure how best to do that:
Been reading up on apps like Funkwhale, but it’s not clear whether it’d share DRM tracks.
Is posting a Spotify playlist link the best I can do? 😬
Building a Productivity System That Works for You
https://blog.allthingstech.social/building-a-productivity-system-that-works-for-you/
#Tech #Technology #AllThingsTech #Blog #Blogger #Blogging #Author #Writer #WordPress
🔗 https://blog.allthingstech.social/building-a-productivity-system-that-works-for-you/
#Tech #Technology #AllThingsTech #Blog #TechBlog
https://flip.it/zr0ABn
#Tech #AI #ChatGPT #ArtificialIntelligence #Journalism

Study of ChatGPT citations makes dismal reading for publishers | TechCrunch
As more publishers cut content licensing deals with ChatGPT-maker OpenAI, a study put out this week by the Tow Center for Digital Journalism -- looking atNatasha Lomas (TechCrunch)

Most in Germany want Australia-style social media ban: poll
A survey has shown that a majority in Germany would support banning social media use for those under 16. This week, Australian lawmakers approved legislation to that effect.Deutsche Welle
Two critical security flaws impacting the Spam protection, Anti-Spam & FireWall plugin WordPress could allow an unauthenticated attacker to install & enable malicious plugins on susceptible sites.
https://www.wordfence.com/blog/2024/11/200000-wordpress-sites-affected-by-unauthenticated-critical-vulnerabilities-in-anti-spam-by-cleantalk-wordpress-plugin/
#wordpress #it #security #privacy #engineer #media #tech #news
I've tried following the manual and asked for help on the BrailleBlaster mailing list, but the explanation given by another list member didn't help. I can't afford Duxbury and the other translation software I've tried, Sao Mai Braille, doesn't support a lot of US standards for UEB.
I would really appreciate any help with this!
#Braille #BrailleProofreading #BrailleTranscription #tech #technology #AssistiveTechnology #Accessibility
@mastoblind @main
I'm thinking about selling what I have off...
I might be better off just collecting SBCs...
They make some pretty fancy ones these days.
#blog #tech
https://gomoot.com/firefox-ottimizza-i-download-linux-con-la-compressione-tar-xz/
#blog #browser #download #ecosistema #firefox #installazione #linux #lzma #mozilla #news #picks #tech #tecnologia

Firefox ottimizza i download Linux con la compressione .tar.xz
Con il nuovo formato, Firefox riduce la dimensione dei pacchetti del 25%. Un aggiornamento che ottimizza l’efficienza e semplifica la gestione su Linux.cristina (Gomoot : tecnologia e lifestyle)
IT-security researchers at ESET have exposed a malicious campaign by the Russia-linked RomCom group, which combined two previously unknown (zero-day) vulnerabilities to compromise targeted systems including Windows and Firefox.
https://www.welivesecurity.com/en/eset-research/romcom-exploits-firefox-and-windows-zero-days-in-the-wild/
#firefox #windows #zerodays #backdoor #it #security #privacy #engineer #media #tech #news
RomCom exploits Firefox and Windows zero days in the wild
ESET Research details the analysis of a previously unknown vulnerability in Mozilla products exploited in the wild and another previously unknown Microsoft Windows vulnerability, combined in a zero-click exploit.www.welivesecurity.com
https://blog.codeminer42.com/codeminer42-dev-weekly-39/
#blog #codeminer42 #tech #news #weekly
Codeminer42 Dev Weekly #39 - The Miners
We invite you to read it, like it, and share it with your friends the newest Dev Weekly!Gabriel Quaresma (The Miners - Codeminer42's Engineering Blog)
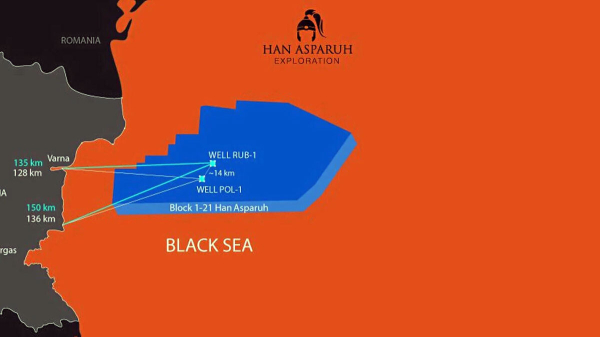
OMV Petrom and NewMed Energy to Advance Exploration in Bulgaria’s Han Asparuh Offshore Block - EUROPE SAYS
OMV Petrom and NewMed Energy Balkan are committed to accelerate exploration efforts in Han Asparuh offshore block inEUROPE SAYS (EUROPESAYS.COM)

Australia passes landmark social media ban for children under 16
Australian lawmakers on Thursday approved a landmark ban on social media for children under 16 in some of the world’s toughest such controls.Peter Guo (NBC News)

Bluesky's open API means anyone can scrape your data for AI training | TechCrunch
Bluesky might not be training AI systems on user content, but there's little stopping third-parties from doing so.Paul Sawers (TechCrunch)
https://gomoot.com/cosa-fa-un-microcontrollore-raspberry-pi/
#ai #blog #ia #iot #luci #microcontroller #microcontrollere #micropython #motori #news #picks #pico #raspberry #robotica #sensori #tech #tecnologia
Cosa fa un microcontrollore Raspberry Pi ?
Scopri quello che c'è da sapere sul microcontrollore Raspberry Pi e le sue infinite applicazioni. I microcontrollori sono il cuore della tecnologia IoT.Graziano (Gomoot : tecnologia e lifestyle)
A small hand-selected list of design, gaming, technology and more based websites or services that are participating in the Black Friday sale.
https://www.adamsdesk.com/posts/black-friday-sales/
#blog #BlackFriday #tech #gaming #design #100DaysToOffload

Apple has released emergency security updates for macOS Sequoia that fix two zero-day vulnerabilities that “may have been actively exploited on Intel-based Mac systems”. As per usual, Apple didn’t share details about the attacks in which patched vulnerabilities are exploited.
[CVE-2024-44309 & CVE-2024-44308]
https://support.apple.com/en-us/121753
#apple #macos #update #it #security #privacy #engineer #media #tech #news
About the security content of macOS Sequoia 15.1.1 - Apple Support
This document describes the security content of macOS Sequoia 15.1.1.Apple Support
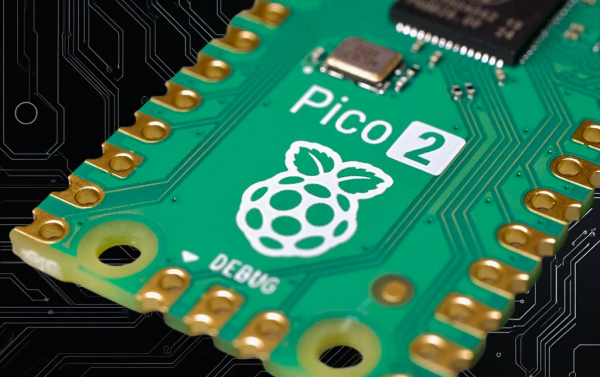
https://gomoot.com/raspberry-pi-pico-2-w-il-microcontrollore-wireless-da-5-euro
#arm #blog #iot #microcontroller #news #picks #pico2w #raspberry #riscv #tech #tecnologia #wifi #wireless

Raspberry Pi Pico 2 W: il microcontrollore Wireless da 5 Euro
La Raspberry Pi Foundation lancia il microcontrollore dualcore Raspberry Pi Pico 2 W, WiFi e Bluetooth integrati, prestazioni superiori a un prezzo accessibileGraziano (Gomoot : tecnologia e lifestyle)
https://blog.thalium.re/posts/llvm-powered-devirtualization/
#ycombinator #blog #tech
LLVM-powered devirtualization
Virtualization is a powerful technique for code obfuscation, and reversing it can be challenging. In this post, we cover the work done during an internship on developing an automated devirtualization tool.THALIUM
https://www.thenationalnews.com/future/technology/2024/11/26/what-is-the-goldfish-generation-and-has-it-changed-media-habits-forever/

What is the Goldfish Generation and has it changed media habits for ever?
TikTok, Vice and Blinx officials discuss how to best capture and retain audiences at Global Media CongressCody Combs (The National)
#tech #websites #blog #blogs #technology
Threat hunters are warning about an updated version of the Python-based NodeStealer that's now equipped to extract more information from victims Facebook Ads Manager accounts and harvest credit card data stored in web browsers.
https://www.netskope.com/blog/python-nodestealer-targets-facebook-ads-manager-with-new-techniques
#facebook #socialmedia #ads #malware #it #security #privacy #engineer #media #tech #news
Python NodeStealer Targets Facebook Ads Manager with New Techniques - Netskope
Summary In September 2023, Netskope Threat Labs reported a Python-based NodeStealer targeting Facebook business accounts. NodeStealer collects FacebookJan Michael Alcantara (Netskope)
[KolibriOS lets you do simple tasks and even play games on your legacy PC.]
While most operating systems are written in C and C++, KolibriOS is written in pure x86 assembly and as a result small and lightweight enough to run off a standard 1.44 MB floppy disk.
https://en.wikipedia.org/wiki/KolibriOS
#kolibrios #floppydisk #x86 #assembler #code #programming #retrocomputing #retro #gaming #it #engineer #media #tech #news
#ChromeOSFlex #chromeos #android #google #blog #tech #TechLovers #technology #developers
https://terryjking8.wordpress.com/2024/11/24/the-future-of-chromeos/

The future of ChromeOS, and the consquences of merging it with Android
I always view ChromeOS as a beacon of hope for the open-source desktop. Despite being controlled by a conglomerate, it empowered users to acquire a genuine Linux computer with the convenience of ma…TerryJKing
That could allow a local attacker to gain root privileges without requiring user interaction. Needrestart is a utility that scans a system to determine the services that need to be restarted after applying shared library updates.
https://blog.qualys.com/vulnerabilities-threat-research/2024/11/19/qualys-tru-uncovers-five-local-privilege-escalation-vulnerabilities-in-needrestart
#linux #ubuntu #it #security #privacy #engineer #tech #media #news
Qualys TRU Uncovers Five Local Privilege Escalation Vulnerabilities in needrestart | Qualys Security Blog
The Qualys Threat Research Unit (TRU) has identified five Local Privilege Escalation (LPE) vulnerabilities within the needrestart component…Saeed Abbasi (Qualys, Inc.)
🔗 https://weblog.kylereddoch.me/2024/11/apple-music-to-discord
#KylesTechKorner #Blog #Tech #Weblog

Apple Music to Discord - Kyle's Tech Korner
My life and journey through this world of technologyweblog.kylereddoch.me
https://gomoot.com/a-minecraft-movie-tra-entusiasmo-e-scetticismo
#blog #film #jackblack #minecraft #movie #news #picks #teaser #tech #tecnologia #trailer #warnerbros

A Minecraft Movie: tra entusiasmo e scetticismo
A Minecraft Movie: il film avventura in live action divide i fan ma il primo trailer completo promette avventura e divertimento blocchetto dopo blocchettoGraziano (Gomoot : tecnologia e lifestyle)
https://about.flipboard.com/inside-flipboard/tech-and-media-newsletters-on-flipboard/
#Flipboard #Newsletter #Tech #Media #Journalism #IndependentJournalist #NewsInfluencers
The Newest Tech and Media Newsletters on Flipboard
Add popular newsletters in media and tech to your Flipboard. We're thrilled to add publications from Om Malik, Matthew Ingram, and others.Marci McCue (About Flipboard)
T-Mobile has joined a list of major organizations like AT&T, Verizon & Lumen Technologies that have been singled out as part of what appears to be a full-blown Chinese threat actors cyber espionage campaign.
https://www.wsj.com/politics/national-security/t-mobile-hacked-in-massive-chinese-breach-of-telecom-networks-4b2d7f92
#us #telecom #companies #breach #it #security #privacy #engineer #media #tech #news
🔗 https://blog.allthingstech.social/my-first-few-days-with-the-mac-mini/
#Tech #Technology #AllThingsTech #Blog #TechBlog
My First Few Days With The Mac Mini
https://blog.allthingstech.social/my-first-few-days-with-the-mac-mini/
#Tech #Technology #AllThingsTech #Blog #Blogger #Blogging #Author #Writer #WordPress
Check out what @saskia had to say about Bluesky continuing to grow.
https://forbetter.ghost.io/even-more-bluesky-growth/
#Fediverse #Mastodon #SocialMedia #Bluesky #X #OpenSocial #SocialWeb #Tech

Even more Bluesky Growth
Bluesky is breaking ceiling after ceiling for open social media. It's getting a bit boring now isn't it? We've all heard about the success of Bluesky. I mean, even ITV News did a segment on it.Saskia (FORbetter)
#fifine #fifinemicrophones #tech #review #blog #microphone
https://churapereviews.com/2024/11/20/fifine-m9-lavalier-mic-system-review/
As I'd prefer not to fully cut off & never buy anything from all these places, but this pushy sales tactic definitely makes that a temptation, because if I had similar in person, I'd definitely never buy anything at said retailer?
#Tech #Gardening #Sales


![[ImageSource: Valve]
Valve says it also made massive updates to Half-Life 2’s maps, which will fix “longstanding bugs, restore content and features lost to time, and improve the quality of a few things like lightmap resolution and fog.” There’s a new option to play with the original launch day blood and fire effects as well, and Valve has updated Half-Life 2’s gamepad controls to “match” last year’s Half-Life 1 anniversary update.
<https://www.theverge.com/2023/11/17/23965754/half-life-25th-anniversary-update>
And finally Valve added 3.5 hours of new developer commentary within the game. The company also is printing an expanded second edition of the Raising the Bar book about the game’s development, which includes “the Half-Life 2 development story, with never-before-seen concept art from Episode One and Episode Two, along with ideas and experiments for the third episode that never came to be.” The book will return to print in 2025.
Maybe soon we’ll get Half-Life 3? Maybe? [ImageSource: Valve]
Valve says it also made massive updates to Half-Life 2’s maps, which will fix “longstanding bugs, restore content and features lost to time, and improve the quality of a few things like lightmap resolution and fog.” There’s a new option to play with the original launch day blood and fire effects as well, and Valve has updated Half-Life 2’s gamepad controls to “match” last year’s Half-Life 1 anniversary update.
<https://www.theverge.com/2023/11/17/23965754/half-life-25th-anniversary-update>
And finally Valve added 3.5 hours of new developer commentary within the game. The company also is printing an expanded second edition of the Raising the Bar book about the game’s development, which includes “the Half-Life 2 development story, with never-before-seen concept art from Episode One and Episode Two, along with ideas and experiments for the third episode that never came to be.” The book will return to print in 2025.
Maybe soon we’ll get Half-Life 3? Maybe?](https://friendica-leipzig.de/photo/preview/600/319709)


![[ImageSource: ESET]
RomCom Victims Heatmap
ESET’s investigation shows that RomCom targeted various sectors, including government entities in Ukraine, the pharmaceutical industry in the US and the legal sector in Germany, for both espionage and cybercrime purposes. The group, also known as Storm-0978, Tropical Scorpius or UNC2596, is known for both opportunistic attacks and targeted espionage.
From October 10th to November 4th, ESET’s data showed that users visiting these malicious websites were primarily located in Europe and North America, with the number of victims ranging from one to as many as 250 in some countries. [ImageSource: ESET]
RomCom Victims Heatmap
ESET’s investigation shows that RomCom targeted various sectors, including government entities in Ukraine, the pharmaceutical industry in the US and the legal sector in Germany, for both espionage and cybercrime purposes. The group, also known as Storm-0978, Tropical Scorpius or UNC2596, is known for both opportunistic attacks and targeted espionage.
From October 10th to November 4th, ESET’s data showed that users visiting these malicious websites were primarily located in Europe and North America, with the number of victims ranging from one to as many as 250 in some countries.](https://friendica-leipzig.de/photo/preview/600/314593)
![[ImageSource: ESET]
RomCom Attack Flow
The exploit chain worked by first redirecting users to fake websites, which used domains designed to appear legitimate and included the names of other organizations, before sending them to a server hosting the exploit code.
These fake sites often used the prefix or suffix “redir” or “red” to a legitimate domain, and the redirection at the end of the attack took the victims to the legitimate website, hiding the attack. Once the exploit successfully ran, it installed RomCom’s custom backdoor, giving the attackers remote access and control over the infected machine.
"The compromise chain is composed of a fake website that redirects the potential victim to the server hosting the exploit and should the exploit succeed, shellcode is executed that downloads and executes the RomCom backdoor," said ESET researcher Damien Schaeffer. [ImageSource: ESET]
RomCom Attack Flow
The exploit chain worked by first redirecting users to fake websites, which used domains designed to appear legitimate and included the names of other organizations, before sending them to a server hosting the exploit code.
These fake sites often used the prefix or suffix “redir” or “red” to a legitimate domain, and the redirection at the end of the attack took the victims to the legitimate website, hiding the attack. Once the exploit successfully ran, it installed RomCom’s custom backdoor, giving the attackers remote access and control over the infected machine.
"The compromise chain is composed of a fake website that redirects the potential victim to the server hosting the exploit and should the exploit succeed, shellcode is executed that downloads and executes the RomCom backdoor," said ESET researcher Damien Schaeffer.](https://friendica-leipzig.de/photo/preview/600/314595)


![Apple has transitioned to using Intel processors on Macs in June 2006 and stopped shipping them altogether in June 2023, after starting using its own silicon in 2020.
The two vulnerabilities “may have been actively exploited on Intel-based Mac systems”, but it’s unclear at this time whether that means that they can’t be exploited on Apple-based Macs.
[⚠️In any case, all MacOS Sequoia users should update their systems as soon as possible.⚠️]
CVE-2024-44309 affects WebKit, the browser engine used in the Safari web browser and all iOS and iPadOS web browsers, and can be triggered when it’s made to process maliciously crafted web content. It can enable a cross site scripting (XSS) attack.
CVE-2024-44308 affects JavaScriptCore (the built-in JavaScript engine for WebKit) and can likewise be exploited via maliciously crafted web content. It can lead to arbitrary code execution.
<Both vulnerabilities have been reported by security researchers Clément Lecigne and Benoît Sevens of Google’s Threat Analysis Group (TAG).> Apple has transitioned to using Intel processors on Macs in June 2006 and stopped shipping them altogether in June 2023, after starting using its own silicon in 2020.
The two vulnerabilities “may have been actively exploited on Intel-based Mac systems”, but it’s unclear at this time whether that means that they can’t be exploited on Apple-based Macs.
[⚠️In any case, all MacOS Sequoia users should update their systems as soon as possible.⚠️]
CVE-2024-44309 affects WebKit, the browser engine used in the Safari web browser and all iOS and iPadOS web browsers, and can be triggered when it’s made to process maliciously crafted web content. It can enable a cross site scripting (XSS) attack.
CVE-2024-44308 affects JavaScriptCore (the built-in JavaScript engine for WebKit) and can likewise be exploited via maliciously crafted web content. It can lead to arbitrary code execution.
<Both vulnerabilities have been reported by security researchers Clément Lecigne and Benoît Sevens of Google’s Threat Analysis Group (TAG).>](https://friendica-leipzig.de/photo/preview/600/306034)


![[ImageSource: Netskope Threat Labs]
"We recently found several Python NodeStealer samples that collect budget details of the account using Facebook Graph API," Michael Alcantara explained. "The samples initially generate an access token by logging into adsmanager.facebook[.]com using cookies collected on the victim's machine."
Aside from collecting the tokens and business-related information tied to those accounts, the malware includes a check that's explicitly designed to avoid infecting machines located in Vietnam as a way to evade law enforcement actions, further solidifying its origins. [ImageSource: Netskope Threat Labs]
"We recently found several Python NodeStealer samples that collect budget details of the account using Facebook Graph API," Michael Alcantara explained. "The samples initially generate an access token by logging into adsmanager.facebook[.]com using cookies collected on the victim's machine."
Aside from collecting the tokens and business-related information tied to those accounts, the malware includes a check that's explicitly designed to avoid infecting machines located in Vietnam as a way to evade law enforcement actions, further solidifying its origins.](https://friendica-leipzig.de/photo/preview/600/302336)
![[ImageSource: Netskope Threat Labs]
On top of that, certain NodeStealer samples have been found to use the legitimate Windows Restart Manager to unlock SQLite database files that are possibly being used by other processes. This is done so in an attempt to siphon credit card data from various web browsers.
Data exfiltration is achieved using Telegram, underscoring that the messaging platform still continues to be a crucial vector for threat actors despite recent changes to its policy.
Malvertising via Facebook is a lucrative infection pathway, often impersonating trusted brands to disseminate all kinds of malware. This is evidenced by the emergence of a new campaign starting November 3, 2024, that has mimicked the Bitwarden password manager software through Facebook sponsored ads to install a rogue Google Chrome extension.
<https://www.bitdefender.com/en-us/blog/labs/inside-bitdefender-labs-investigation-of-a-malicious-facebook-ad-campaign-targeting-bitwarden-users> [ImageSource: Netskope Threat Labs]
On top of that, certain NodeStealer samples have been found to use the legitimate Windows Restart Manager to unlock SQLite database files that are possibly being used by other processes. This is done so in an attempt to siphon credit card data from various web browsers.
Data exfiltration is achieved using Telegram, underscoring that the messaging platform still continues to be a crucial vector for threat actors despite recent changes to its policy.
Malvertising via Facebook is a lucrative infection pathway, often impersonating trusted brands to disseminate all kinds of malware. This is evidenced by the emergence of a new campaign starting November 3, 2024, that has mimicked the Bitwarden password manager software through Facebook sponsored ads to install a rogue Google Chrome extension.
<https://www.bitdefender.com/en-us/blog/labs/inside-bitdefender-labs-investigation-of-a-malicious-facebook-ad-campaign-targeting-bitwarden-users>](https://friendica-leipzig.de/photo/preview/600/302338)

![[ImageSource: KolibriOS]
Screenshot of the KolibriOS desktop on first boot with default wallpaper.
As a fork of 32-bit MenuetOS back in 2004, KolibriOS has since followed its own course, sticking to the x86 codebase and requiring only a modest system with an i586-compatible CPU. Unlike MenuetOS’ proprietary x86_64 version, there’s no 64-bit in KolibriOS, but at this level you probably won’t miss it.
<https://wiki.kolibrios.org/wiki/Hardware_Support#Network> [ImageSource: KolibriOS]
Screenshot of the KolibriOS desktop on first boot with default wallpaper.
As a fork of 32-bit MenuetOS back in 2004, KolibriOS has since followed its own course, sticking to the x86 codebase and requiring only a modest system with an i586-compatible CPU. Unlike MenuetOS’ proprietary x86_64 version, there’s no 64-bit in KolibriOS, but at this level you probably won’t miss it.
<https://wiki.kolibrios.org/wiki/Hardware_Support#Network>](https://friendica-leipzig.de/photo/preview/600/299602)
![[ImageSource: KolibriOS]
A curiosity recently caught our eye—that curiosity is KolibriOS, a super-lightweight and ultra-fast OS designed for legacy PCs with its floppy drive-friendly install size of just 1.44 MB.
The OS was really fast, stable, runs DOOM smoothly and overall seems to be a great small OS for x86 platforms that could give an old system a new lease on life.
<https://youtu.be/LjvG54xszoY> [ImageSource: KolibriOS]
A curiosity recently caught our eye—that curiosity is KolibriOS, a super-lightweight and ultra-fast OS designed for legacy PCs with its floppy drive-friendly install size of just 1.44 MB.
The OS was really fast, stable, runs DOOM smoothly and overall seems to be a great small OS for x86 platforms that could give an old system a new lease on life.
<https://youtu.be/LjvG54xszoY>](https://friendica-leipzig.de/photo/preview/600/299604)
![Multiple decade-old security vulnerabilities have been disclosed in the needrestart package.
The vulnerabilities are believed to have existed since the introduction of interpreter support in needrestart 0.8, which was released on April 27, 2014.
"These needrestart exploits allow Local Privilege Escalation (LPE) which means that a local attacker is able to gain root privileges," Ubuntu said in an advisory, noting they have been addressed in version 3.8.
<https://ubuntu.com/blog/needrestart-local-privilege-escalation>
The 5 flaws are listed below:
• CVE-2024-48990 [CVSS score: 7.8] - A vulnerability that allows local attackers to execute arbitrary code as root by tricking needrestart into running the Python interpreter with an attacker-controlled PYTHONPATH environment variable.
• CVE-2024-48991 [CVSS score: 7.8] - A vulnerability that allows local attackers to execute arbitrary code as root by winning a race condition & tricking needrestart into running their own, fake Python interpreter.
• CVE-2024-48992 [CVSS score: 7.8] - A vulnerability that allows local attackers to execute arbitrary code as root by tricking needrestart into running the Ruby interpreter with an attacker-controlled RUBYLIB environment variable.
• CVE-2024-11003 [CVSS score: 7.8] and CVE-2024-10224 [CVSS score: 5.3] - Two vulnerabilities that allows a local attacker to execute arbitrary shell commands as root by taking advantage of an issue in the libmodule-scandeps-perl package. (before version 1.36) Multiple decade-old security vulnerabilities have been disclosed in the needrestart package.
The vulnerabilities are believed to have existed since the introduction of interpreter support in needrestart 0.8, which was released on April 27, 2014.
"These needrestart exploits allow Local Privilege Escalation (LPE) which means that a local attacker is able to gain root privileges," Ubuntu said in an advisory, noting they have been addressed in version 3.8.
<https://ubuntu.com/blog/needrestart-local-privilege-escalation>
The 5 flaws are listed below:
• CVE-2024-48990 [CVSS score: 7.8] - A vulnerability that allows local attackers to execute arbitrary code as root by tricking needrestart into running the Python interpreter with an attacker-controlled PYTHONPATH environment variable.
• CVE-2024-48991 [CVSS score: 7.8] - A vulnerability that allows local attackers to execute arbitrary code as root by winning a race condition & tricking needrestart into running their own, fake Python interpreter.
• CVE-2024-48992 [CVSS score: 7.8] - A vulnerability that allows local attackers to execute arbitrary code as root by tricking needrestart into running the Ruby interpreter with an attacker-controlled RUBYLIB environment variable.
• CVE-2024-11003 [CVSS score: 7.8] and CVE-2024-10224 [CVSS score: 5.3] - Two vulnerabilities that allows a local attacker to execute arbitrary shell commands as root by taking advantage of an issue in the libmodule-scandeps-perl package. (before version 1.36)](https://friendica-leipzig.de/photo/preview/600/290296)




