Suche
Beiträge, die mit PRIVACY getaggt sind
Tesla-Fahrzeuge erfassen ständig ihre Umgebung, überwachen das Fahrverhalten und übertragen Daten in die USA. Ob europäische Alternativen wirklich datenschutzfreundlicher sind, ist schwer zu prüfen. Fast alle Autos kannst du aber offline stellen und für Navi/Stau ein TomTom oder trackingfreies Android nehmen. Die beste Wahl: Fahrrad fahren und Open-Source-Car-Projekte wie AGL (Automotive Grade Linux) unterstützen.
#NoTesla #SurveillanceCars #Privacy #AGL #LinuxCars
LOCAL AND GENERAL…
A #Wellington periodical recently published #photographs showing a number of infantile paralysis #patients who are under treatment at the Wellington Hospital. At yesterday’s meeting of the Hospital Board, exception to the photographs being published was taken by Mr. C. H. Chapman, who wanted to know who gave permission for the photographs to be taken. He voiced his strong disapproval of such photographs being permitted to be taken, and said he hoped that whoever had taken them would never be permitted to do so again. The chairman (Mr. F. Castle) said as far as he knew no member of the board gave authority. Mr. C. M. Luke stated that his committee intended to bring up the matter at its next meeting.
https://paperspast.natlib.govt.nz/newspapers/EP19250227.2.45
#OnThisDay #OTD #PapersPast #Children #Hospitals #Polio #Poliomyelitis #Privacy #NewZealand

Anti-Surveillance Mapmaker Refuses Flock Safety's Cease and Desist Demand
Flock Safety loves to crow about the thousands of local law enforcement agencies around the United States that have adopted its avian-themed automated license plate readers (ALPRs).Electronic Frontier Foundation

EFF to California's Supreme Court: Protect the Privacy of Internet Users' Communications
The Stored Communications Act is built on the principle that users have a reasonable expectation of privacy that companies like Snap and Meta will not disclose your communications to third parties.Electronic Frontier Foundation
"If they're going to cave into Zuck's demand to facilitate spying on Instagram users, do we really think they'll resist Kier Starmer's demands to remove Signal – and any other app that stands up to the Snooper's Charter – from the App Store?
It goes without saying that the "bad guys" the UK government claims it wants to target will be able to communicate in secret no matter what Apple does here. They can just use an Android phone and sideload a secure messaging app, or register an iPhone in Ireland or any other country and bring it to the UK. The only people who will be harmed by the combination of the British government's reckless disregard for security, and Apple's designs that trade the security of its users for the security of its shareholders are millions of law-abiding Britons, whose most sensitive data will be up for grabs by anyone who hacks their accounts."
https://pluralistic.net/2025/02/25/sneak-and-peek/
#CyberSecurity #UK #Apple #Encryption #Backdoors #Privacy #Totalitarianism #iCloud
The U.K. news cannot be seen in isolation and follows years of battling between big tech and governments over warranted, legal access to encrypted messages and content to fuel investigations into serious crimes such as terrorism and child abuse.
As I reported in 2020, “it is looking ever more likely that proponents of end-to-end security, the likes of Facebook and Apple, will lose their campaign to maintain user security as a priority.” It has taken five years, but here we now are.
The last few weeks may have seemed to signal a unique fork in the road between the U.S. and its primary Five Eyes ally, the U.K. But it isn’t. In December, the FBI and CISA warned Americans to stop sending texts and use encrypted platforms instead. And now the U.K. has forced open iCloud to by threatening to mandate a backdoor. But the devil’s in the detail — and we’re fast approaching a dangerous pivot."
https://www.forbes.com/sites/zakdoffman/2025/02/24/fbis-new-iphone-android-security-warning-is-now-critical/
#USA #FBI #CyberSecurity #Encryption #Privacy #UK #CISA #Apple #Backdoor

FBI Warns iPhone, Android Users—We Want ‘Lawful Access’ To All Your Encrypted Data
UK forces Apple to provide encrypted data to security agencies—is America next?Forbes
https://aliyesha.com/sub/articles/news/display/uk_uttarakhand_govt_literary_award_controversy
#uttarakhand #dehradun #india #news #press #LiteraryAward #AwardControversy #CasteBias #WritersRights #LiteraryJustice #literature
Enjoy tracker free reading with us. #privacy #privacymatters

देहरादून: उत्तराखण्ड सरकार का साहित्यिक पुरस्कार विवादों में।
उत्तराखण्ड राज्य सरकार जब भी राज्यस्तरीय पुरस्कारों का चयन करती है, वे हमेशा की तरह विवादों में रहते हैं।प्रेम पंचोली (Aliyesha)
https://aliyesha.com/sub/articles/news/display/nd_metro_golden_line_deep_tunnel_work
#newdelhi #delhi #india #news #press #metro #railway #tunnel #DelhiMetro #GoldenLine #UndergroundMetro #DMRC #UrbanTransport #PublicTransport
Enjoy tracker free reading with us. #privacy #privacymatters

नई दिल्ली: दिल्ली मेट्रो की बड़ी कामयाबी, गोल्डन लाइन पर सबसे गहरी टनल का काम पूरा।
दिल्ली में मेट्रो विस्तार के फेज-4 के तहत DMRC ने एक और बड़ी उपलब्धि हासिल की है।दिल्ली ब्यूरो (Aliyesha)
Viele bekannte VPN-Dienste haben fragwürdige Datenschutzrichtlinien oder unterliegen US-Gesetzen. Bevorzuge europäische Anbieter wie Mullvad oder ProtonVPN, die strenge No-Logs-Richtlinien versprechen – auch wenn deren Einhaltung letztlich eine Frage des Vertrauens bleibt.
#VPN #NoUS #Privacy #Mullvad #ProtonVPN
https://www.camocopy.com/data/de/
#UnplugTrump #AI #GPT4All #Ollama #Privacy #FOSS

Volle Kontrolle über deine Daten - CamoCopy
🔐 Volle Kontrolle über deine Daten - 🇪🇺 Wir ziehen niemals Nutzen aus der Verwendung deiner persönlichen Daten.CamoCopy
Gibt es Listen der lokal steuerbaren Alternativen?
#UnplugTrump #NoCloud #HomeAssistant #SmartHome #Privacy
https://aliyesha.com/sub/articles/news/display/pb_maha_shivratri_live_jiohotstar
#india #news #press #MahaShivaratri #DivineNight #LiveAarti #Jyotirlinga #Spirituality #Meditation #Sadhguru #SriSriRaviShankar #JioHotstar #IshaFoundation #ArtOfLiving #Shiva #ShivParvati
Enjoy tracker free reading with us. #privacy #privacymatters

Chandigarh: Maha Shivaratri: Experience Live Aarti from Jyotirlingas Across India on 26th February.
This Maha Shivaratri, a 12-hour special live broadcast will take place from 6 PM on 26th February to 6 AM the next morning.Dr. Kharbanda (Aliyesha)
https://aliyesha.com/sub/articles/news/display/nd_chaos_delhi_assembly_cag_report
#newdelhi #delhi #india #news #press #politics #aap #bjp #CAG #CAGReport #ExcisePolicy #LiquorPolicyScandal #Corruption #kejriwal
Enjoy tracker free reading with us. #privacy #privacymatters

नई दिल्ली: दिल्ली विधानसभा में हंगामा: सीएजी रिपोर्ट पेश, कई विधायकों का निलंबन।
दिल्ली विधानसभा के दूसरे दिन आज भारी हंगामा देखने को मिला। चुनाव में प्रमुख मुद्दा बनी सीएजी की रिपोर्ट सदन में पेश की गई।दिल्ली ब्यूरो (Aliyesha)
“Save Social”: Rettung der sozialen Medien?
"Save Social" will Digitalkonzerne entmachten und fordert mit prominenter Unterstützung alternative Strukturen von der nächsten Bundesregierung.Deutschlandfunk Kultur
Viele IoT-Geräte (bspw. smarte Steckdosen, Thermostate, Kameras) senden Daten an (US-)Hersteller-Server. Kaufe lokal steuerbare Alternativen oder setze auf Open-Source-Lösungen wie Home Assistant.
#NoCloud #HomeAssistant #SmartHome #Privacy

European Commission Gets Dinged for Unlawful Data Transfer, Sending a Big Message About Accountability
The European Commission was caught failing to comply with its own data protection regulations and, in a first, ordered to pay damages to a user for the violation.Electronic Frontier Foundation
https://blog.thenewoil.org/how-the-uk-is-weakening-safety-worldwide
#Apple #ADP #politics #backdoor #cybersecurity #privacy #blog

How the UK is Weakening Safety Worldwide
This week, the UK put the entire world at risk. I understand that may sound like alarmist hyperbole, but follow me. To understand, we hav...The New Oil
Leland Dudek, a data analyst working in a small anti-fraud office, was suspected of sharing unauthorized access to information with representatives of Musk’s U.S. #DOGE Service. Now he’s the acting #SocialSecurity commissioner.
https://archive.is/029VN#selection-537.0-541.226
"his actions raised enough alarm that he... violated #privacy & #tax laws that sr officials placed him on paid leave as they launched their investigation"
#Musk #News
https://harrylitman.substack.com/i/157635895/a-few-legal-updates-and-summaries
"There are three main kinds of claims directly concerning Musk among the 60+ #lawsuits against the administration... The lawsuits allege violations of:
1. The Federal Advisory Committee Act (FACA)...
2. Potential violations of restrictions on disseminating sensitive information, especially under the #Privacy Act...
3. Violations of the Appointments Clause"
#Musk #Coup #Corruption #Trump #Politics #USPol #News #USNews #US #USA
Accountability for Elon, Emil, and Ed
And some lighter Friday fareHarry Litman (Talking Feds Substack)
A document setting the terms of work at the IRS by Gavin Kliger, a software engineer on Elon Musk’s team, only allows him to see anonymized taxpayer information.
https://www.nytimes.com/2025/02/21/us/politics/irs-doge-gavin-kliger.html
"The #IRS will not allow a member of Elon Musk’s team to view individual #tax returns while he works at the agency...
Gavin Kliger, a 25-year-old... [White House] pushed for Kliger to have broad visibility of IRS data"
#Musk #Politics #Privacy #News #US
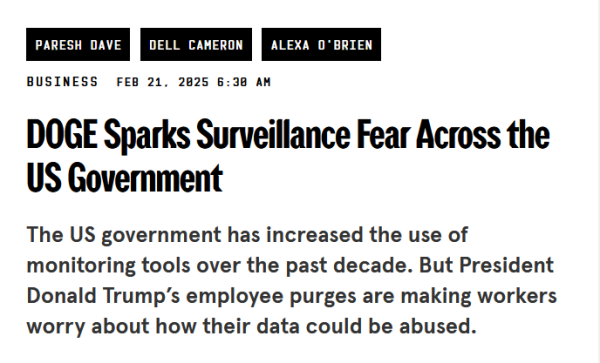
...Trump’s employee purges are making workers worry about how their #data could be abused.
https://www.wired.com/story/surveillance-privacy-doge-federal-employees/
"a barrage of menacing messages... included personal details...
the kinds of encounters that workers across the US #government say they have had w/ #technology...
as Musk’s #DOGE org is rapidly burrowing into various govt agencies & depts... sensitive info "
#Musk #Coup #Corruption #USPol #Privacy #Security #News #USA
We at Tuta would never build a backdoor - and our #opensource code is proof of that.
👉 https://tuta.com/blog/uk-demands-apple-backdoor-encryption
Apple removes cloud encryption for UK users - but there's a grain of hope | Tuta
UK demanded Apple to remove its cloud encryption and Apple complied, but only partially.Tuta
This is a fairly large release as this marks the release of our new video player. The migration from Video.js over to Shaka will allow us to support new features such as higher resolutions and better scrubbing in live videos.
Check out the full patch notes below. You can download the new release over on our website.
https://github.com/FreeTubeApp/FreeTube/discussions/5948
https://freetubeapp.io/#download
#opensource #privacy
Release v0.22.0 Beta · FreeTubeApp FreeTube · Discussion #5948
Summary Our Video Player has undergone a massive overhaul. We have switched from video.js to shaka-player. This allows us to add allot of new features and fix many issues. Notably, it's now possibl...GitHub
Recall allows Microsoft’s Windows 11 Copilot+ devices to screenshot every action a person takes on their PC.
What can you do? Switching to Linux is the clear answer, but some don't know what distro to try.
DistroSea.com is a website that lets you run and test 60+ Linux distributions straight from your web browser.
Have fun!
Source: https://distrosea.com/
#Linux #Computer #Windows #DOS #OPSEC #InfoSec #Privacy #Surveillance
https://www.theguardian.com/lifeandstyle/2025/feb/22/the-bot-asked-me-four-times-a-day-how-i-was-feeling-is-tracking-everything-actually-good-for-us
Gathering data used to be a fringe pursuit of Silicon Valley nerds. Now we’re all at it, recording everything from menstrual cycles and mobility to toothbrushing and time spent in daylight. Is this just narcissism redesigned for the big tech age?
KEWL🌀NEWS
#TRACKING #BIGDATA #IDENTITY #PRIVACY #EXPOSURE PRESS
As the Trump administration concludes its first 30 days in office, three worrying trends emerge at the intersection of technology and democratic governance. New America’s Open Technology Institute has long championed democratically accountable tech policymaking, and over the past month, we have tracked federal actions that run counter to this objective:
- The weakening of oversight of U.S. government surveillance
- The elimination of institutions that protect American consumers and their data
- Systematic efforts to access some of America’s most vital data systems without regard for individual privacy or data security"
https://www.newamerica.org/oti/blog/trumps-tech-governance-making-sense-of-the-administrations-first-30-days/
#USA #Trump #Surveillance #ConsumerRights #Privacy #DataProtection #CyberSecurity

Trump’s Tech Governance: Making Sense of the Administration’s First 30 Days
As the Trump administration concludes the first 30 days, three worrying trends emerge at the intersection of tech and democracy.New America
Some people think the problem with mass surveillance is a kind of machine-driven, automated mind-control ray. They believe the self-aggrandizing claims of tech bros to have finally perfected the elusive mind-control ray, using big data and machine learning.
But you don't need to accept these outlandish claims – which come from Big Tech's sales literature, wherein they boast to potential advertisers that surveillance ads are devastatingly effective – to understand how and why this is harmful. If you're struggling with opioid addiction and I target an ad to you for a fake cure or rehab center, I haven't brainwashed you – I've just tricked you. We don't have to believe in mind-control to believe that targeted lies can cause unlimited harms.
And those harms are indeed grave."
https://pluralistic.net/2025/02/20/privacy-first-second-third/#malvertising
#USA #AdTech #DataBrokers #DataBrokerage #Privacy #BigTech #MassSurveillance #DataProtection

Cornered by the UK’s Demand for an Encryption Backdoor, Apple Turns Off Its Strongest Security Setting
Today, in response to the U.K.’s demands for a backdoor, Apple has stopped offering users in the U.K. Advanced Data Protection, an optional feature in iCloud that turns on end-to-end encryption for files, backups, and more.Electronic Frontier Foundation
few lessons from here:
1. Apple are not your friends when it comes to privacy, and they never will be
2. encrypt and backup with your own keys and independently of the big tech platforms
3. campaign against such surveillance requests by govts
https://www.bbc.com/news/articles/cgj54eq4vejo
#Privacy #Security #Apple #iOS #Mac #UnitedKingdom #Tech #Technology

Apple pulls data protection tool after UK government security row
Customers' photos and documents stored online will no longer be protected by end to end encryption.Zoe Kleinman (BBC News)
Alles, was ich mir für das Winterhalbjahr vorgenommen hatte, konnte ich auch fertigstellen - sogar noch ein klein wenig mehr 😉
Im Rahmen meiner Bemühungen meine Datensicherheit und die Privatsphäre so gut wie mir möglich ist zu schützen, habe ich heute das letzte „Projekt“ fertiggestellt:
Die Synchronisation der Lesezeichen, und sogar der geöffneten Tabs, ohne Firefox-Sync oder ähnliche externe Dienstleister zu nutzen. Geholfen hat mir dabei das Tool “floccus” (https://floccus.org)
Neben der Passwortsynchronisation über KeePassXC hilft es mir den Browser LibreWolf (auf Android Firefox und KeePass2Android ) auf meinen Endgeräten zu nutzen, ohne mir Änderungen und Ergänzungen irgendwie anders zukommen lassen zu müssen.
Vielleicht mache ich mir im nächsten Winter einmal die Mühe und nehme mir die Zeit, Firefox zu härten (https://brainfucksec.github.io/firefox-hardening-guide), aber solange ich all das bereits mit LibreWolf nutzen kann, eilt das ja nicht 😆
Das Sommerhalbjahr kann also mit vielen Fahrradtouren, Wanderungen und neuen Fotos kommen 😀
Danke an @leChris für den Hinweis auf floccus.
#floccus #KeePassXC #Android #KeePass2Android #Passwortsynchronisation #Lesezeichen #LibreWolf #Datenschutz #Privatsphäre #Privacy
https://aliyesha.com/sub/articles/news/display/bh_highspirits_manufacturing_unit_fatuha
#bihar #patna #india #news #press #politics #BJP #JDU #government #governance #ManufacturingGrowth #EmploymentBoost #EconomicDevelopment #jobs #employment
Enjoy tracker free reading with us. #privacy #privacymatters

Patna: Nitish Mishra Inaugurates Highspirit’s State-of-the-Art Manufacturing Unit in Fatuha.
Nitish Mishra, Industry Minister, Government of Bihar, inaugurated Highspirit’s new manufacturing unit in Fatuha.Alok Sharma (Aliyesha)
This account is ran by Preston, the main developer of FreeTube and is where I'll likely post updates and information regarding the project. You can learn more about FreeTube using the site link in my profile where you can find out how to interact with the project and participate in the discussion.
Whether you're a user or a contributor, we'd love to have you stop by and check it out.
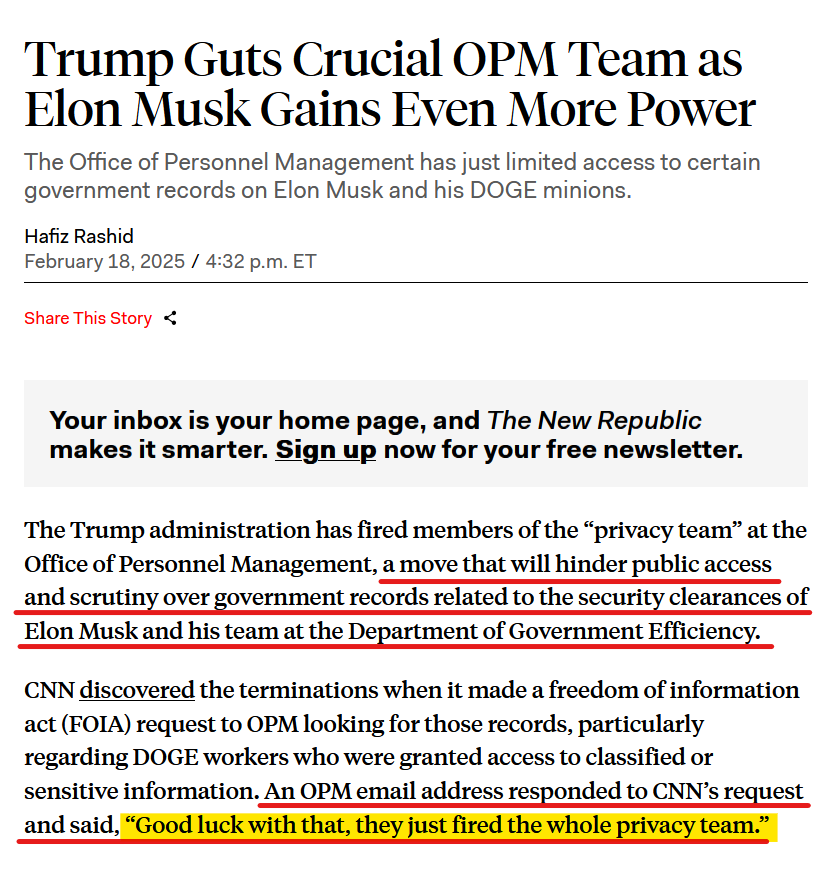
The Office of Personnel Management has just limited access to certain government records on #ElonMusk and his #DOGE minions.
https://newrepublic.com/post/191663/elon-musk-opm-privacy-team
"The Trump administration has fired members of the “privacy team” at the #OPM, a move that will hinder #public access & scrutiny over #government records related to the #security clearances of #ElonMusk & Doge."
#Musk #Coup #Trump #Corruption #Politics #Privacy #USPol #News #US #USA
But there are also two broad, vague exceptions..."
https://www.wired.com/story/privacy-act-doge-lawsuits/
#ElonMusk #Musk #Doge #Lawsuit #Resistance #Resist #Privacy #Law #Legal #Data #Information #Government #Politics #US #USPol #USA #News #USNews
Elon Musk’s DOGE Is Being Sued Under the Privacy Act: What to Know
At least eight ongoing lawsuits related to the so-called Department of Government Efficiency’s alleged access to sensitive data hinge on the Watergate-inspired Privacy Act of 1974. But it’s not airtight.Eric Geller (WIRED)
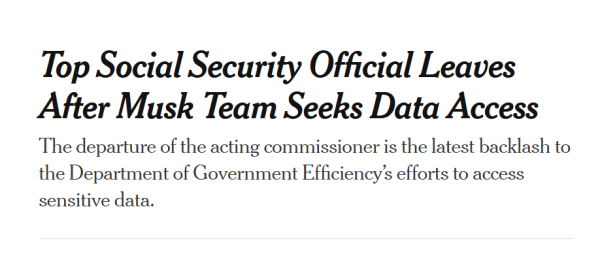
The departure of the acting commissioner is the latest backlash to #DOGE efforts to access sensitive data.
https://www.nytimes.com/2025/02/17/us/politics/social-security-musk-team-access.html
"abrupt departure of a senior federal official who refused to provide Musk’s lieutenants with access to closely held #data. Musk’s team has been embedding with agencies across the federal #government & seeking access to private data"
#Privacy #ElonMusk #Coup #Trump #Politics #News #USA #US
https://aliyesha.com/sub/articles/news/display/nd_new_government_cabinet_meeting
#newdelhi #delhi #india #news #press #bjp #aap #medical #health #ayushman #CAG #CAGReport #corruption
Enjoy tracker free reading with us. #privacy #privacymatters

नई दिल्ली: दिल्ली की रेखा सरकार की पहली कैबिनेट में दो बड़े फैसले, आयुष्मान योजना में 10 लाख का मेडिक्लेम फ्री।
दिल्ली की मुख्यमंत्री रेखा गुप्ता ने आज शपथग्रहण के बाद दो बड़े फैसले लिए हैं।दिल्ली ब्यूरो (Aliyesha)
So bequem die Möglichkeit der Synchronisation zwischen mehreren Endgeräten auch sein kann, die Daten der #Lesezeichen, #AddOns, vielleicht sogar die #Passwörter und neuerdings auch E-Mail-Masken und obendrein auch noch die Telefonnummer-Maske sowie einem #VPN in die Hände EINES Anbieters zu geben - lieber nicht ¯\_(ツ)_/¯
Die Integration von #KeePass war zwar ein wenig herausfordernd, aber jetzt habe ich mich auch hier noch ein wenig besser absichern können 😀
🔗 https://librewolf.net/
#Datenschutz #Privacy #Privatsphäre

LibreWolf Browser
A custom version of Firefox, focused on privacy, security and freedom.librewolf.net






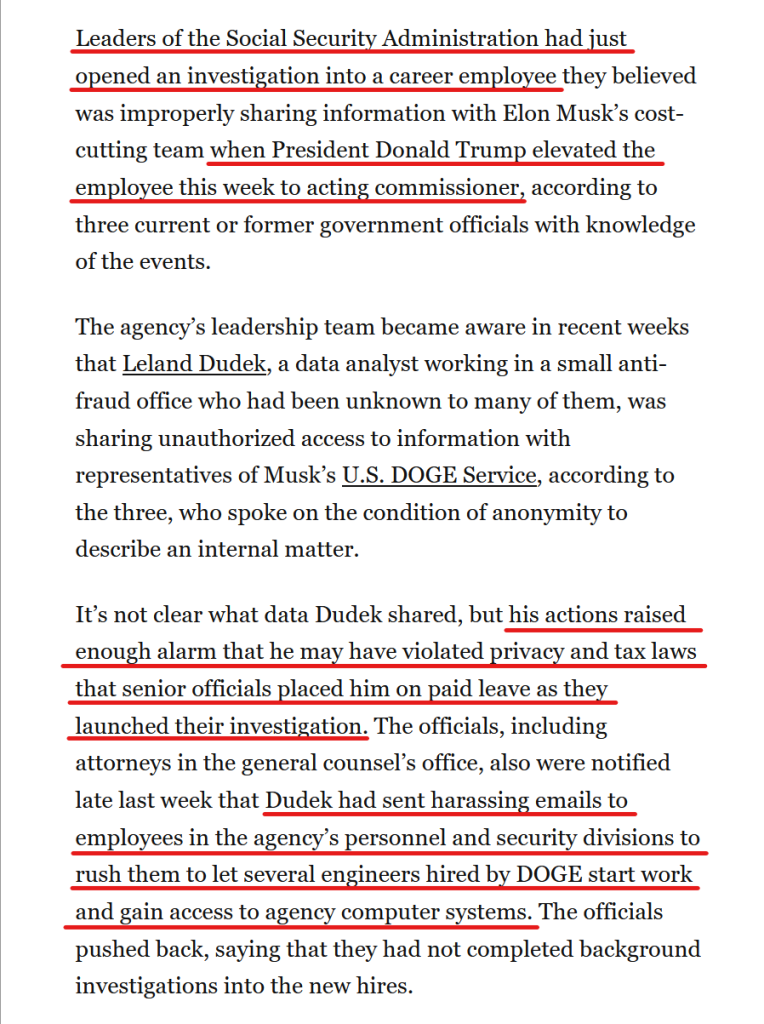





![Sub-heading and text from article:
What Is the Privacy Act?
The Privacy Act is a law that limits how the federal government can collect, use, and share information about US citizens and other people in the United States.
The law’s core features include letting people access government records about them; letting people correct those records if they contain mistakes; requiring agencies to limit information collection, publish lists of records databases, and protect data from hackers; and restricting how agency employees and third parties can access records.
Those restrictions on accessing data are at the heart of the ongoing DOGE saga.
The Privacy Act prohibits an agency from disclosing someone’s records—even within the agency—unless that person approves in writing or the agency meets one of the law’s 12 exceptions. Most of the exceptions deal with fairly specific circumstances, such as congressional oversight, law enforcement investigations, court orders, census work, statistical research, and National Archives preservation. But there are also two broad, vague exceptions: Agencies can share records with their own employees who “have a need for the record in the performance of their duties” or with third parties for “a routine use” (defined as one that is “compatible with the purpose for which [the data] was collected”). Sub-heading and text from article:
What Is the Privacy Act?
The Privacy Act is a law that limits how the federal government can collect, use, and share information about US citizens and other people in the United States.
The law’s core features include letting people access government records about them; letting people correct those records if they contain mistakes; requiring agencies to limit information collection, publish lists of records databases, and protect data from hackers; and restricting how agency employees and third parties can access records.
Those restrictions on accessing data are at the heart of the ongoing DOGE saga.
The Privacy Act prohibits an agency from disclosing someone’s records—even within the agency—unless that person approves in writing or the agency meets one of the law’s 12 exceptions. Most of the exceptions deal with fairly specific circumstances, such as congressional oversight, law enforcement investigations, court orders, census work, statistical research, and National Archives preservation. But there are also two broad, vague exceptions: Agencies can share records with their own employees who “have a need for the record in the performance of their duties” or with third parties for “a routine use” (defined as one that is “compatible with the purpose for which [the data] was collected”).](https://friendica-leipzig.de/photo/preview/600/646152)